Block chain-based V2G transaction privacy protection method, device and system
A blockchain and block technology, applied in the field of blockchain and privacy protection, can solve problems such as energy waste, achieve the effect of ensuring flexibility and security, saving transaction costs, and solving trust problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0043] Embodiment 1, this embodiment provides a V2G transaction privacy protection method based on blockchain;
[0044] A blockchain-based V2G transaction privacy protection method, including:
[0045] The blockchain node receives the transaction parameters sent anonymously by the buyer client, and records the transaction parameters and the first zero-knowledge proof generated by the buyer client on the blockchain; the blockchain node verifies the correctness of the first zero-knowledge proof , and record the verified transaction parameters on the blockchain;
[0046] The blockchain node receives the guarantee fee sent anonymously by the buyer client, and records the guarantee fee and the second zero-knowledge proof generated by the buyer client on the blockchain in the form of a smart contract; the blockchain node verifies the second zero-knowledge proof The correctness of the knowledge proof, and the verification fee is recorded on the blockchain;
[0047] The blockchain n...
Embodiment 11
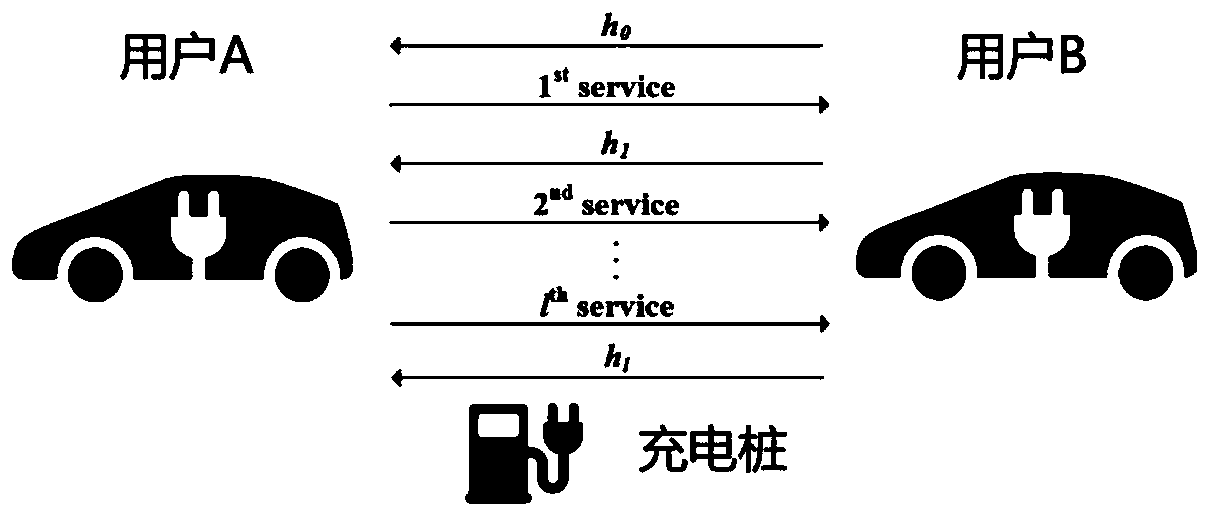
[0134] Consider the specific actions of the seller in the transaction. User A is an electric car user, and the zero-knowledge balance in his account is cmt A =SHA256(v A , sn A ,r A ), he wants to sell the electricity in the electric car to user B, including the following steps:
[0135] 1.1.1 User A and user B negotiate the transaction parameter cmt offline c , N, pk A , pk B , and then wait for user B to deploy the smart contract in the blockchain;
[0136] 1.1.2 After the smart contract is deployed on the blockchain, user A checks whether the transaction parameters in the contract are the same as those previously negotiated by the two parties, and checks whether there is a correct amount of guarantee fee in the contract.
[0137] If the parameters are the same and the amount of guarantee fee is correct, proceed to the next step of the transaction;
[0138] If the parameters are different or the amount of guarantee fee is incorrect, it is considered that user B has c...
Embodiment 12
[0144] Consider the specific actions of the buyer in the transaction. User B is an electric car user, and the zero-knowledge balance in his account is cmt B =SHA256(v B , sn B ,r B ), he wants to purchase electricity from user A, including the following steps:
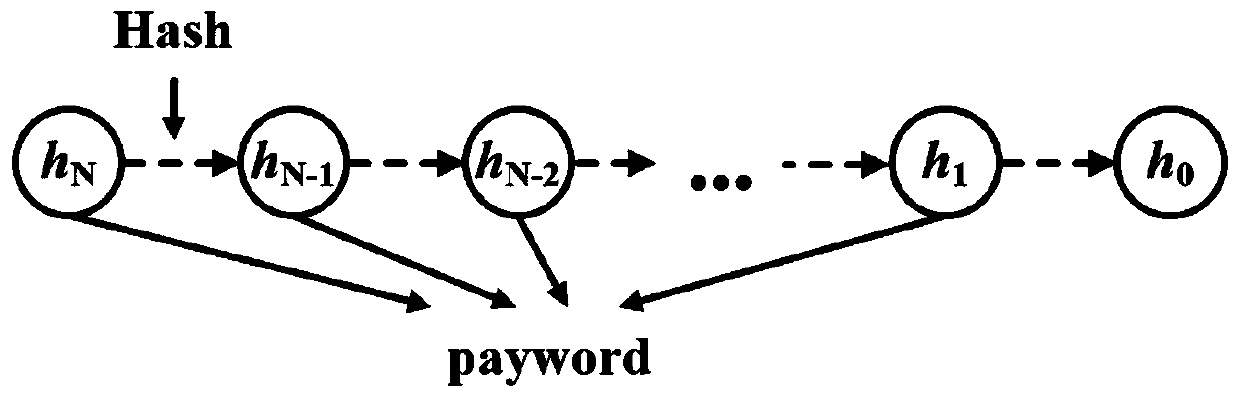
[0145] 1.2.1 User B generates a guarantee fee certificate cmt c =SHA256(amt,r c ), negotiate the transaction parameters cmt with user A offline c , N, pk A , pk B , then user B generates a hash chain of length N with hash root h 0 .
[0146] 1.2.2 User B generates parameters and constructs a zero-knowledge amount cmt v =SHA256(amt,sn v ,r v ), and construct a zero-knowledge balance cmt using B ’=SHA256(v B ’, sn B ’, r B '). User B generates a zero-knowledge proof π based on these parameters convert , and put sn B , cmt B , cmt v , cmt B ’ and π convert , sent to the blockchain, after waiting for miners to verify, cmt v Become an effective zero-knowledge amount.
[0147] 1.2.3 User B deploys a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com