Industrial Internet data security monitoring method and system based on block chain
An industrial Internet and data security technology, applied in the field of blockchain-based industrial Internet data security monitoring, can solve the problems of central organization failure, intrusion and tampering, verification result falsification, etc., so as to weaken the dependence of institutions and avoid key exchange , the effect of a reliable data base
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in further detail below in conjunction with the embodiments and accompanying drawings. Here, the exemplary embodiments and descriptions of the present invention are used to explain the present invention, but not to limit the present invention.
[0022] For ease of understanding or description, the relevant technical terms involved in the present invention are explained or defined as follows:
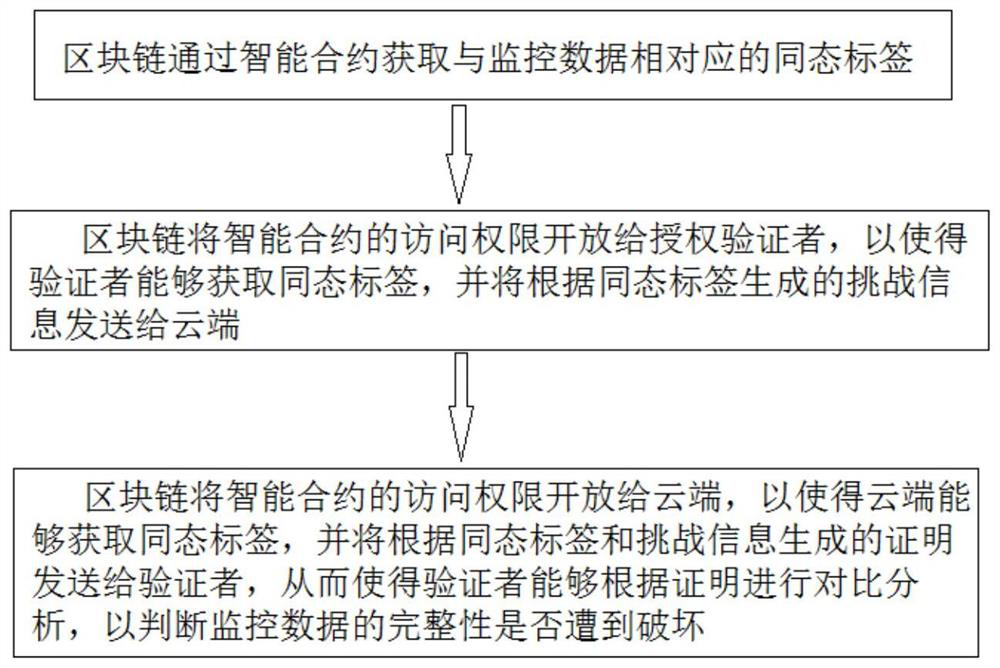
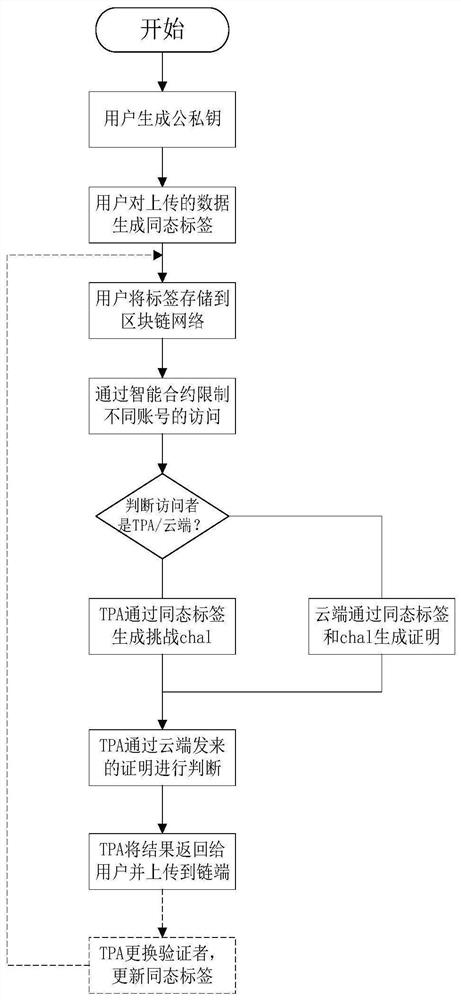
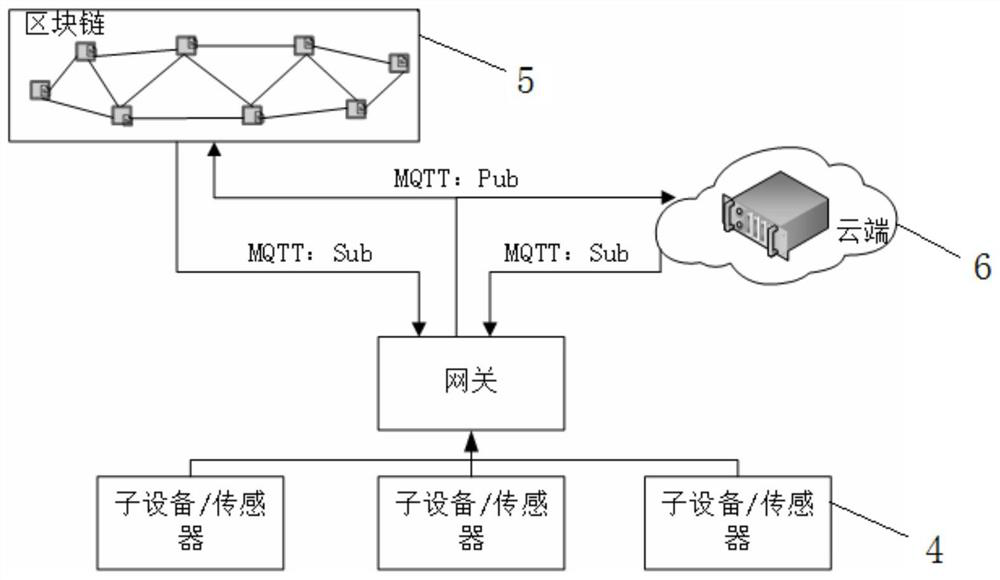
[0023] 1. Data Integrity Verification: It refers to the means of proof to verify whether the received data is completely consistent with the original data. Among them, in the integrity verification, it usually uses cryptography to verify the data on the server and the previously stored data. Are the data consistent.
[0024] 2. Homomorphic label: It is a label generated based on homomorphic encryption. In the process of data integrity verificati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com