Relay protection key data redundancy storage and reliability recovery system and method
A relay protection and key data technology, applied in the direction of electrical digital data processing, error detection of redundant codes, error detection of redundant data in calculations, etc., can solve the problem of reducing the operating efficiency of the processor and the switching speed of two machines Slow, low real-time remote database backup and other issues, to achieve reliable backup, improve operating efficiency, and high reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
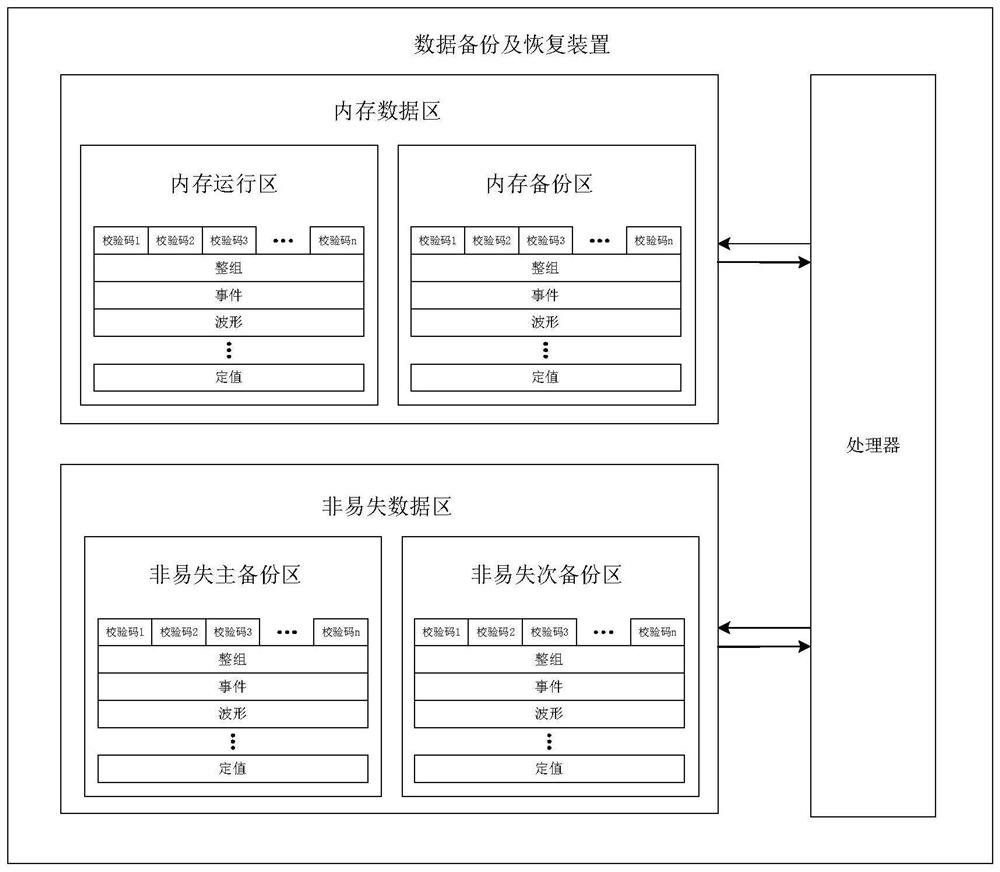
[0049] see figure 1 , a system for redundant storage and reliability recovery of relay protection key data in this embodiment includes a memory data area, a non-volatile data area and a processor; the memory data area includes a memory operation area and a memory backup area; the non-volatile The lost data area includes a non-volatile primary backup area and a non-volatile secondary backup area. The processor is used for data backup and recovery of the internal memory data area and the non-volatile data area, and to calculate and judge check codes.
[0050] The memory operation area, the memory backup area, the non-volatile main backup area and the non-volatile secondary backup area are all divided into a check code storage space and a data storage space. The check code storage space stores the check code calculated according to the stored data. The data storage space is used to store key data of relay protection.
[0051] Among them, the memory data is divided into the whole...
Embodiment 2
[0053] see figure 1 and figure 2 , on the basis of Embodiment 1, this embodiment proposes a method for redundant storage and reliability recovery of key data of relay protection, which is carried out according to the following steps:
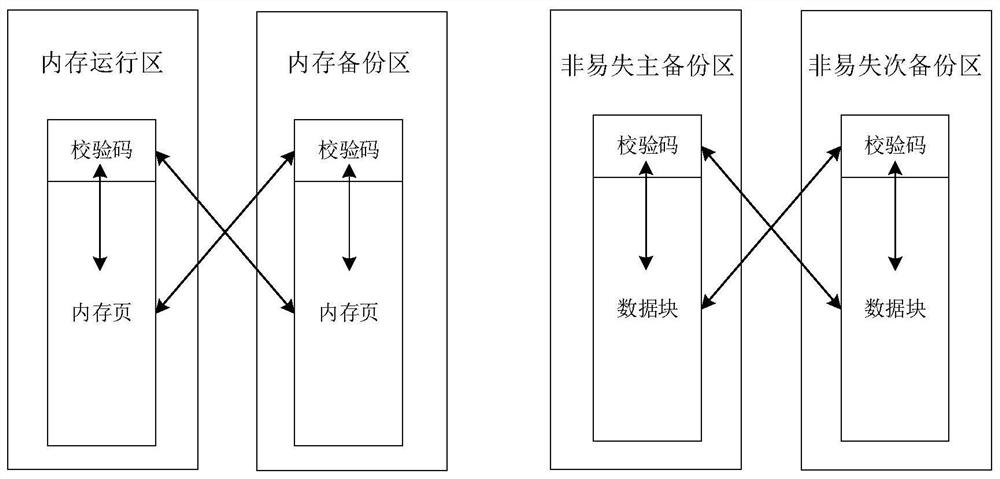
[0054] Step 1: When initializing the data space, the memory data is classified and stored according to the type of relay protection data. Each type of data is based on the memory page and each page is verified separately. The verification code is based on the summary of the national secret SM3; non-volatile The data is classified and stored according to the type of relay protection data. Each type of data is in the unit of data block and each block is checked separately. The check code is based on the summary of the national secret SM3.
[0055] The check code of the memory data is stored separately from the content, the size of the data content space is allocated in advance, divided according to the memory pages, and the summary generated by ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com