Method executed by user equipment and user equipment
A technology of user equipment and physical downlink, applied in the field of user equipment, can solve the problems of adding low-priority synchronization sources for UEs, failing to serve as UE synchronization sources, conflicts, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
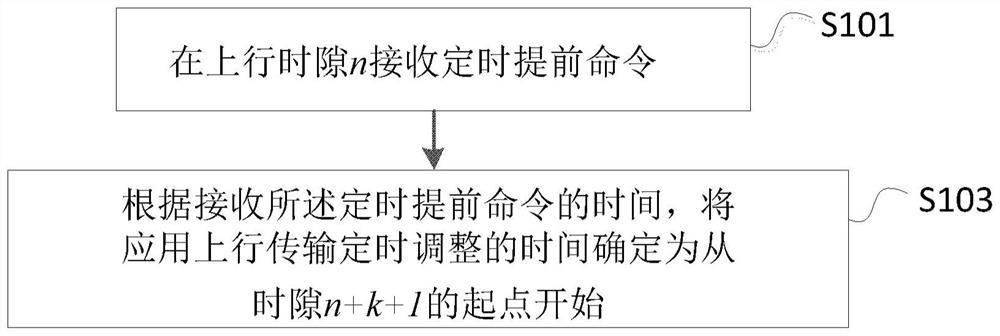
[0196] Below, combine figure 1 To illustrate the method executed by the user equipment in the first embodiment of the present invention.
[0197] figure 1 It is a flowchart showing the method executed by the user equipment according to the first embodiment of the present invention.
[0198] Such as figure 1 As shown, in the first embodiment of the present invention, the steps performed by the user equipment UE include: step S101 and step S103.
[0199] Specifically, in step S101, a timing advance command is received in the uplink time slot n. among them,
[0200] · The uplink time slot n may be the last time slot of the uplink time slot that overlaps with one or more time slots for PDSCH reception.
[0201] · The PDSCH may be a PDSCH that provides a timing advance command.
[0202] · When determining the uplink time slot n, it can be assumed that T TA =0, where T TA It is the value of uplink transmission timing adjustment, the unit is second.
[0203] · When determining the uplink t...
Embodiment 2
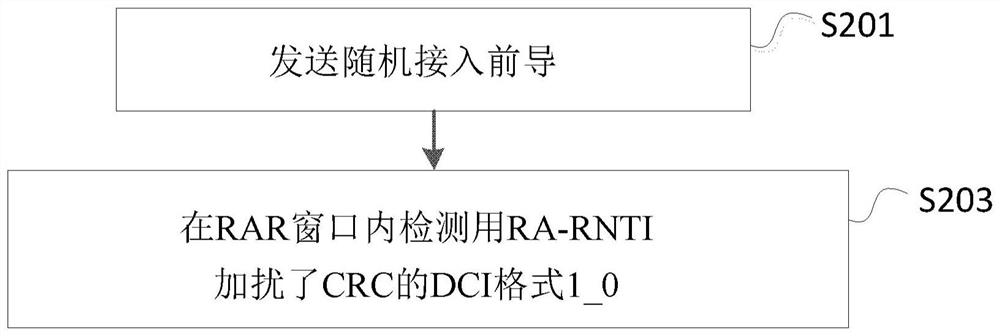
[0262] Below, combine figure 2 To illustrate the method executed by the user equipment in the second embodiment of the present invention.
[0263] figure 2 It is a flowchart showing the method executed by the user equipment according to the second embodiment of the present invention.
[0264] Such as figure 2 As shown, in the second embodiment of the present invention, the steps performed by the user equipment UE include: step S201 and step S203.
[0265] Specifically, in step S201, a random access preamble (random access preamble, sometimes referred to as physical random access channel, PRACH) is sent. Wherein, the transmission of the random access preamble can be triggered by a higher layer, can also be triggered by a PDCCH order (PDCCH order), or can be triggered by other methods.
[0266] In addition, in step S203, the DCI format 1_0 in which the CRC is scrambled with RA-RNTI is detected in the RAR (Random Access Response) window.
[0267] Optionally, if the UE detects the DCI f...
Embodiment 3
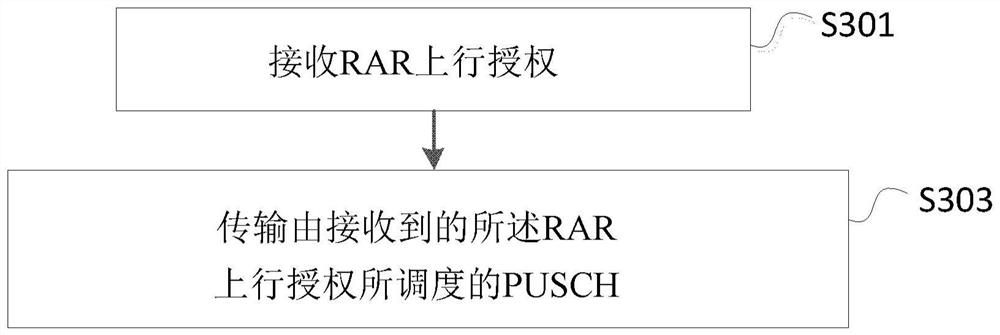
[0273] Below, combine image 3 To illustrate the method executed by the user equipment in the third embodiment of the present invention.
[0274] image 3 It is a flowchart showing the method executed by the user equipment according to the third embodiment of the present invention.
[0275] Such as image 3 As shown, in the third embodiment of the present invention, the steps performed by the user equipment UE include: step S301 and step S303.
[0276] Specifically, in step S301, the RAR uplink authorization is received. Wherein, the RAR uplink grant may be included in a MAC RAR, the MAC RAR may be included in a MAC PDU, and the MAC PDU may be carried by a PDSCH. In addition, sometimes, when the context is clear, it can also be considered that the PDSCH carries a "RAR message" (RAR message), and the RAR message contains the RAR uplink grant.
[0277] In addition, in step S303, the PUSCH scheduled by the received RAR uplink grant is transmitted. The UE may assume that the minimum tim...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com