Android malicious software family clustering method based on method call graph
A method call graph, malware technology, applied in computer parts, decompilation/disassembly, program code conversion, etc., can solve the problems of high randomness of API sequence, huge similarity calculation, influence of detection effect, etc. Avoiding limitations, extracting features is stable, and enriching the effect of calculation methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] In order to make the object, technical solution and advantages of the present invention clearer, the present invention is further described in detail. It should be understood that the specific embodiments described here are only used to explain the present invention, and are not intended to limit the present invention, that is, the described embodiments are only some of the embodiments of the present invention, but not all of the embodiments.
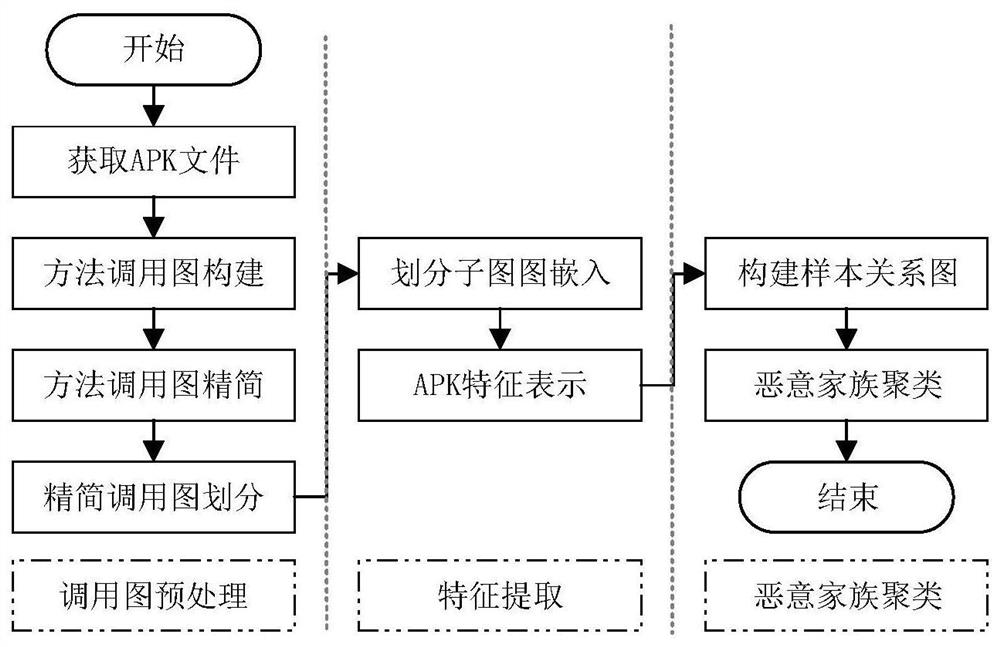
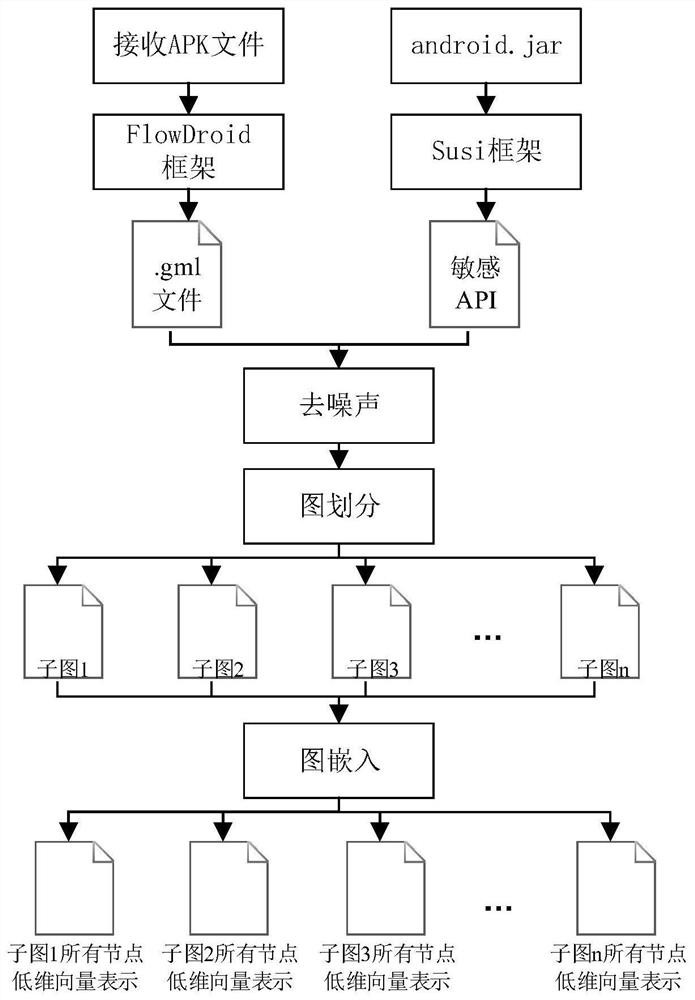
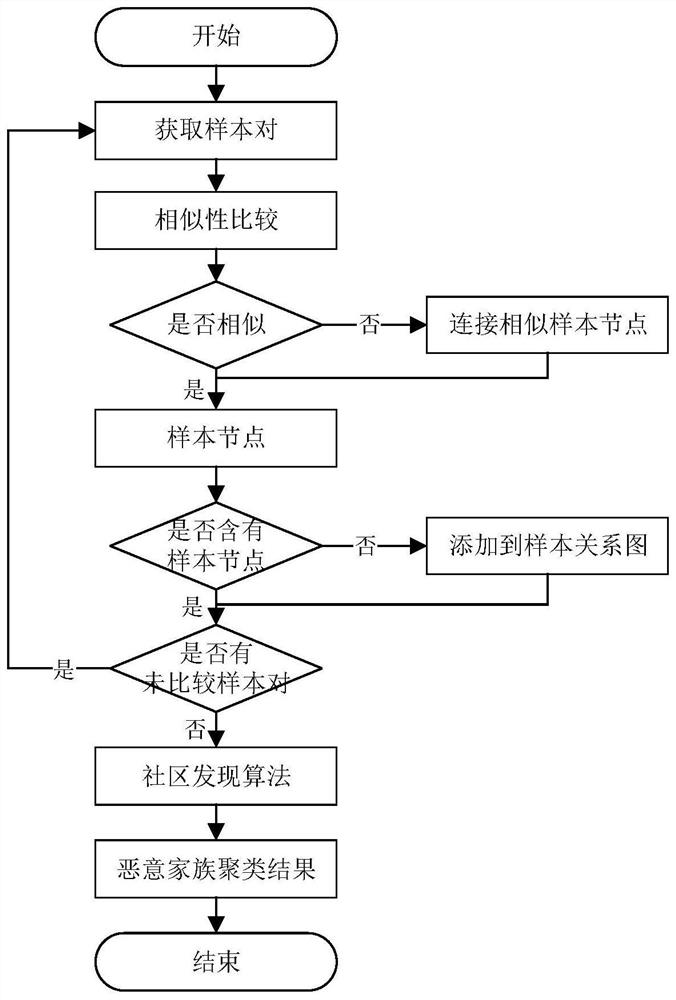
[0041] The invention provides a method for constructing a method call graph, and uses the method call graph as a feature of malware detection, which is a new exploration of Android malware detection. Using the community discovery algorithm, the method call graph is cut through simple graph partitioning, which improves the detection efficiency. At the same time, the vector space after graph embedding has more flexible and rich calculation methods, and can also compress data and play a role in dimensionality reduction.
[0042] Su...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com