Security event processing method and system, medium and computer equipment
A security event and processor technology, applied in the field of network security, can solve the problems of inability to deal with large-scale security incident scenarios, low processing efficiency, slow automatic response to large-scale security incidents, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
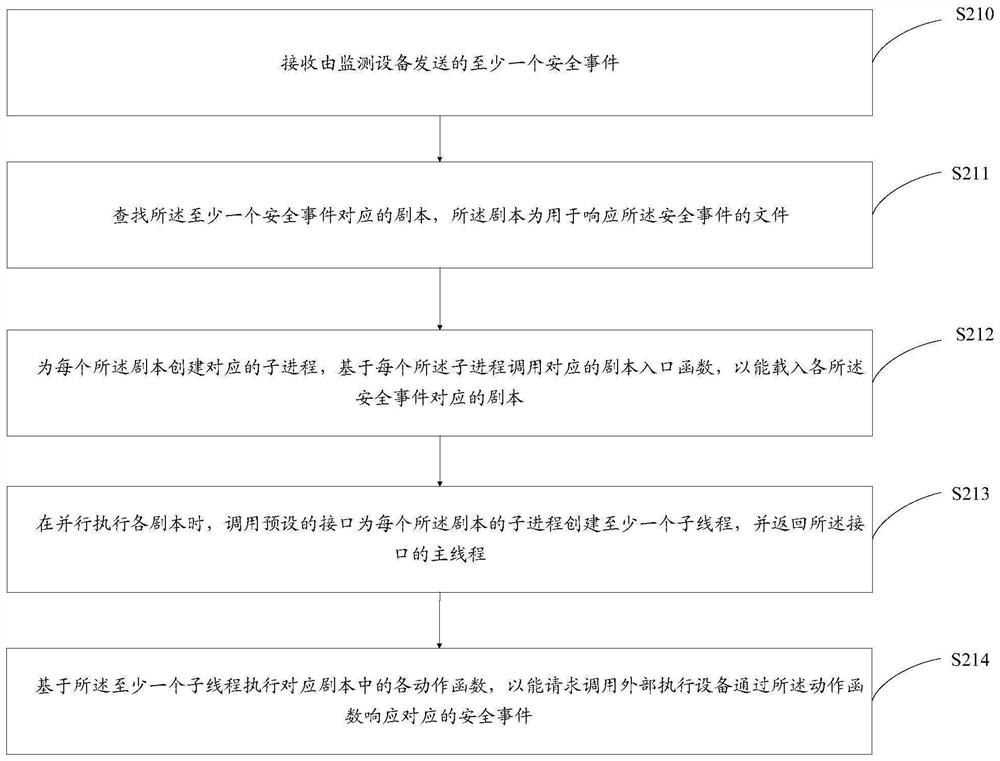
[0048] This embodiment provides a method for handling security events, such as figure 1 and figure 2 As shown, the methods include:
[0049] S210. Receive at least one security event sent by the monitoring device;
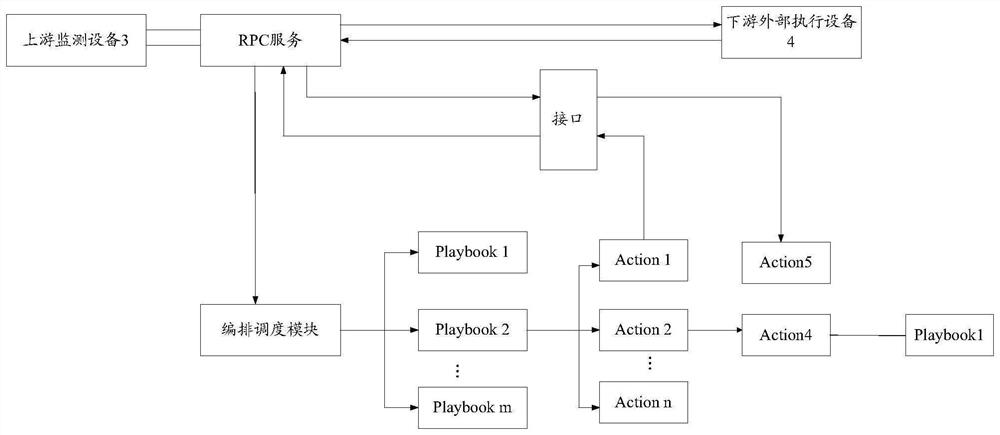
[0050]refer to figure 1 In this application, at least one security event reported by the upstream monitoring device can be received through the Remote Procedure Call Protocol (RPC, Remote Procedure Call Protocol) service. After receiving at least one security event, the security event is not processed immediately, but the security event Stored in the preset event queue. Among them, the RPC service is a service framework based on the RPC protocol, and is a multi-threaded service model. Upstream monitoring equipment can include specific hardware monitoring equipment, and can also include monitoring equipment such as firewalls; security incidents can include but are not limited to the following: network attacks, virus intrusion, virus extortion, and mining viruse...
Embodiment 2
[0100] This embodiment provides a device for processing security events, please refer to Figure 4 , the device includes: a receiving module 41, a search module 42, a creation module 43 and an execution module 44; wherein;
[0101] A receiving module 41, configured to receive at least one security event sent by the monitoring device;
[0102] A search module 42, configured to search for a script corresponding to the at least one security event, where the script is a file for responding to the security event;
[0103] Create module 43, be used for creating corresponding subprocess for each described script, call corresponding script entry function based on each described subprocess, to be able to load the script corresponding to each described security event; Execute each script in parallel , call the preset interface to create at least one sub-thread for each sub-process of the script, and return to the main thread of the interface;
[0104] The execution module 44 is config...
Embodiment 3
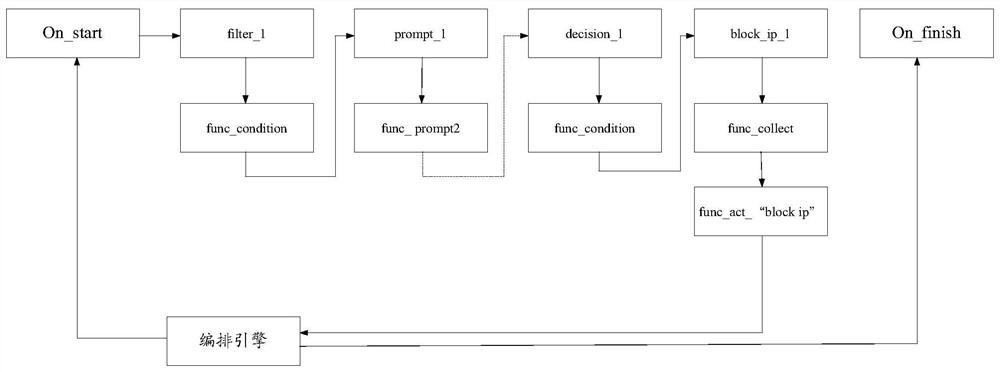
[0152] This embodiment provides a computer device, such as Figure 5 As shown, it includes a memory 410, a processor 420, and a computer program 411 stored on the memory 410 and operable on the processor 420. When the processor 420 executes the computer program 411, the following steps are implemented:
[0153] receiving at least one security event sent by the monitoring device;
[0154] Find a script corresponding to the at least one security event, where the script is a file for responding to the security event;
[0155] Create a corresponding sub-process for each of the scripts, and call the corresponding script entry function based on each of the sub-processes, so as to be able to load the script corresponding to each of the security events;
[0156] When each script is executed in parallel, call a preset interface to create at least one sub-thread for each sub-process of the script, and return to the main thread of the interface;
[0157] Each action function in the cor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com