Multi-level hybrid vulnerability automatic mining method
An automatic mining and multi-level technology, applied in the computer field, can solve problems such as path explosion, slowness, and slow solution speed of symbolic execution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
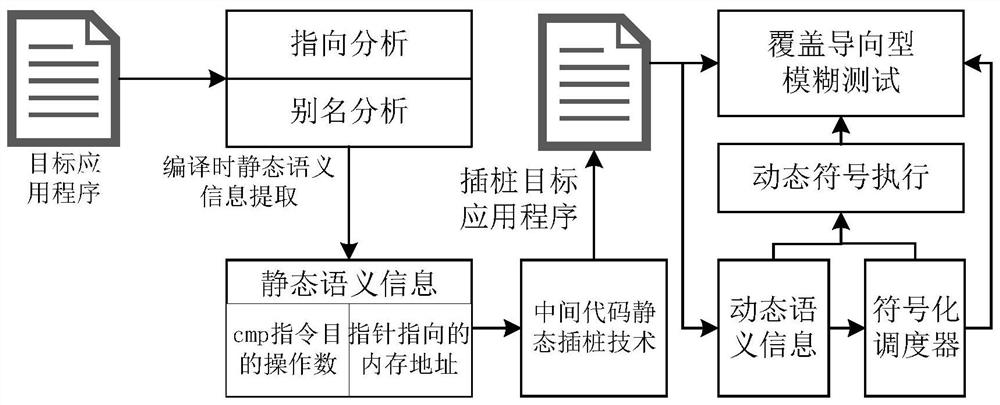
[0043] Please refer to Figure 1-4 , the present invention provides a technical solution: a multi-level mixed vulnerability automatic mining method, comprising the following steps:
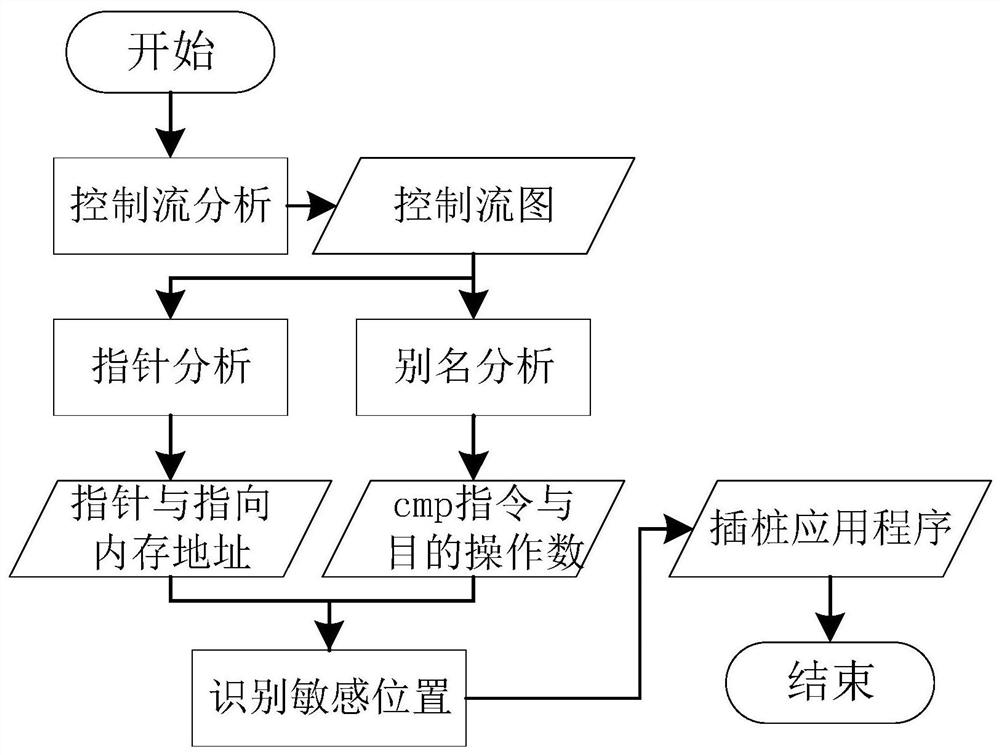
[0044] S1: Use static analysis technology to use pointer analysis to obtain the pointer allocation and assignment process in the program, and record the memory address locations pointed to by all pointers; use alias analysis technology to obtain the destination operand of CMP instructions to clarify the jump address of the target program;
[0045] S2: Through the static insertion technology of the intermediate code, the monitoring code is inserted into the key position of the target program;
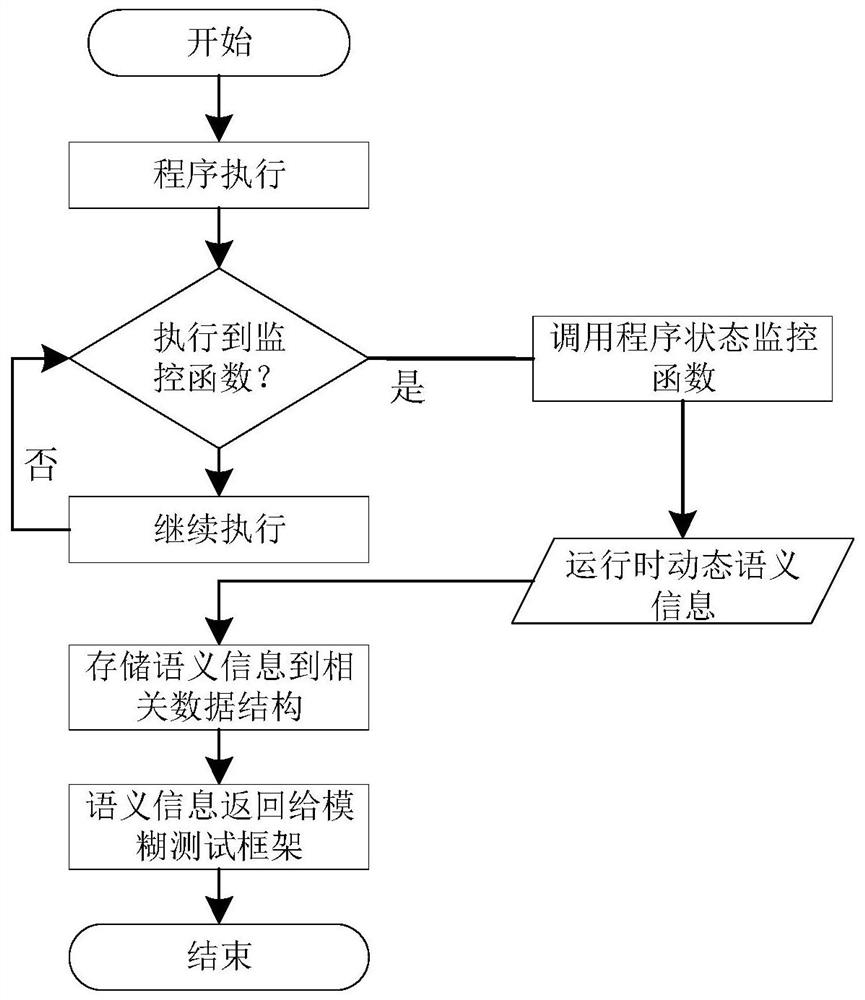
[0046] S3: Save the current stack frame information in the global data structure when the monitoring function is executed in the target program after instrumentation through the dynamic semantic information extraction technology, and the stack frame information includes the memory address saved from the esp ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com