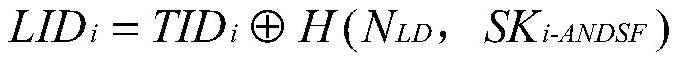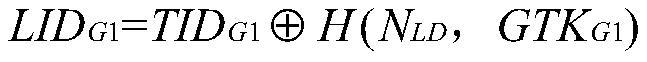Batch switching authentication and key agreement method for heterogeneous network
A technology for handover authentication and key negotiation, applied in the field of batch handover authentication and key negotiation, it can solve the problems of consuming large network resources, low security level, and the communication process is no longer secure, so as to reduce system overhead and achieve strong security guarantees. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
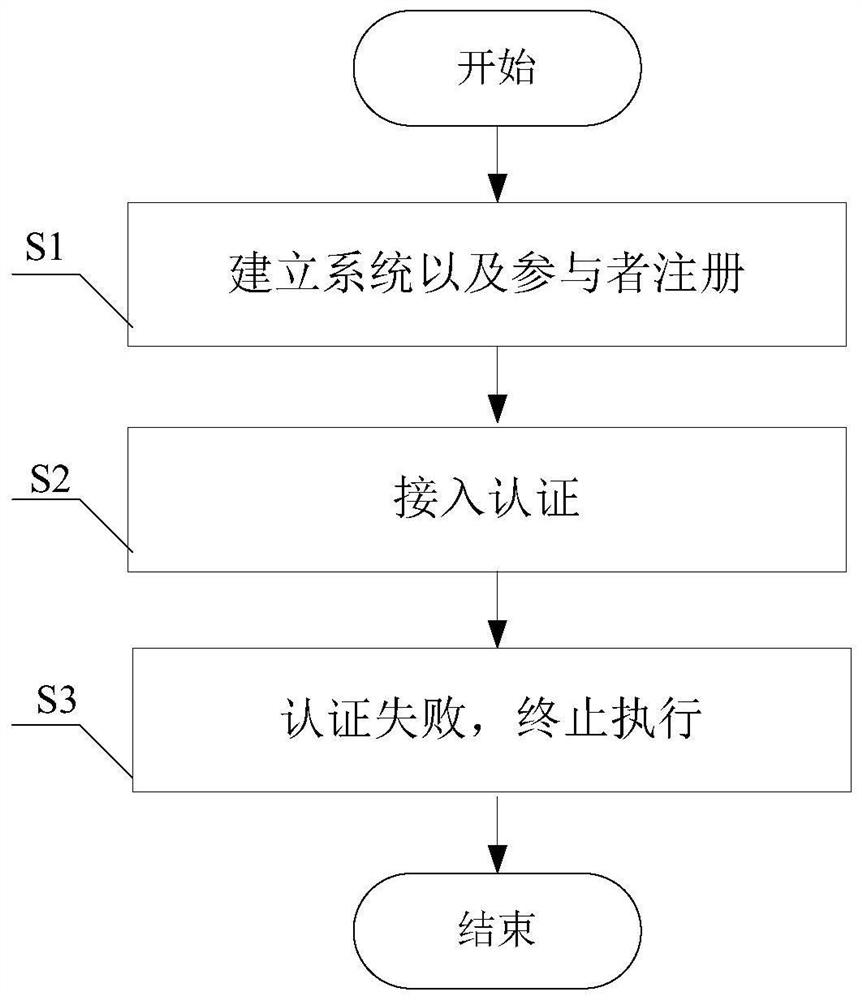
[0123] Such as figure 1 As shown, the present invention provides a batch handover authentication and key agreement method for heterogeneous networks, and its implementation method is as follows:
[0124] S1. Establish system and participant registration: establish a system, and register users authenticated by several participants on the LTE-A network to obtain their respective identity information;
[0125] In this embodiment, when the user equipment roams from the LTE-A network to the WLAN network, it first needs to register on the LTE-A network. It is assumed that all user equipments have completed two-way identity authentication with the LTE-A network, and have obtained relevant parameters for subsequent communication. It includes (1) the temporary identity TID used to communicate with the discovery function module ANDSF; (2) the group pre-shared group temporary key GTKG1; (3) the pre-shared key negotiated with the service gateway and the packet gateway in the LTE system r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com