Internet-of-things security and protection sensor network searching method, device, equipment and storage medium
An Internet of Things and sensor technology, applied in the computer field, can solve problems such as large battery power loss, shorten battery life cycle, and safety hazards, and achieve the effect of improving user experience, avoiding shortening battery life cycle, and avoiding excessive power consumption.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
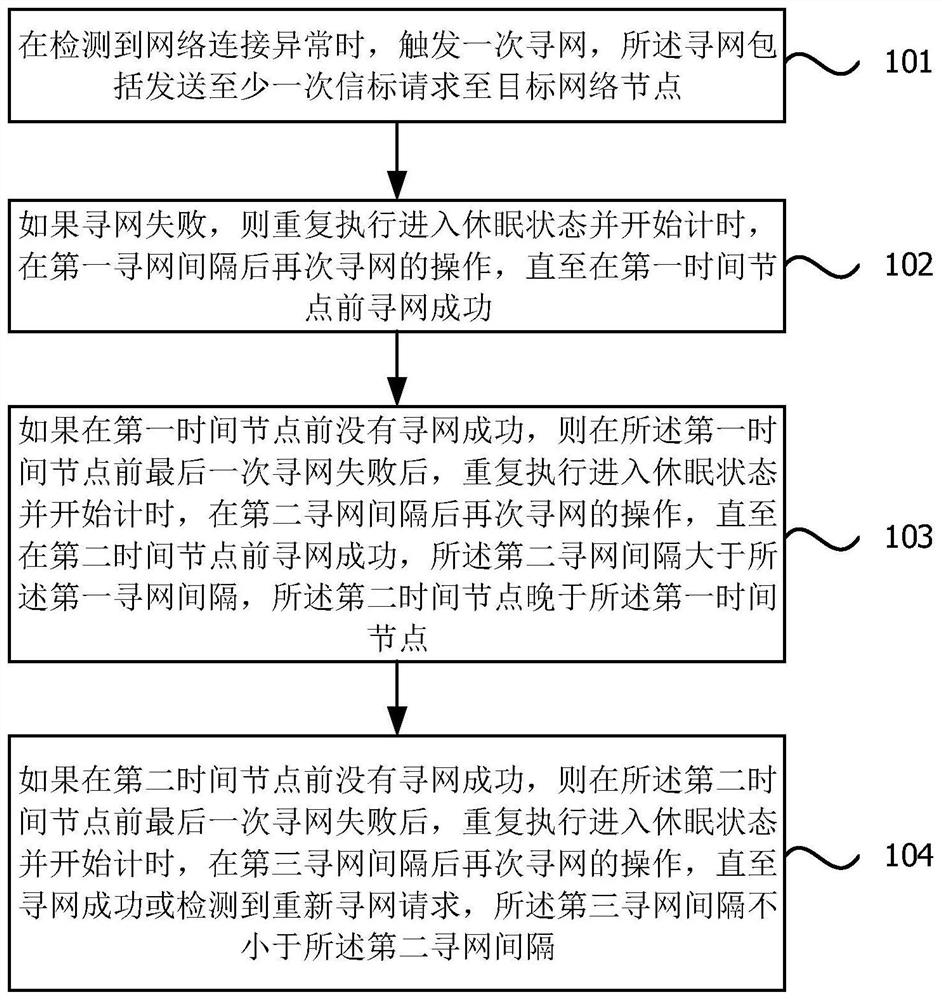
[0025] figure 1 It is a flow chart of a method for finding a network of an Internet of Things security sensor provided by Embodiment 1 of the present invention. The embodiment of the present invention can be applied to the situation where the security sensor detects an abnormal network connection and needs to find the network efficiently. The method can be executed by the Internet of Things security sensor network finding device provided by the embodiment of the present invention. It is implemented in the form of hardware, and generally can be integrated in computer equipment. For example, security sensor devices. Such as figure 1 As shown, the method of the embodiment of the present invention specifically includes:
[0026] Step 101. When an abnormal network connection is detected, a network search is triggered, and the network search includes sending a beacon request to a target network node at least once.
[0027] Among them, abnormal network connection includes network...
Embodiment 2
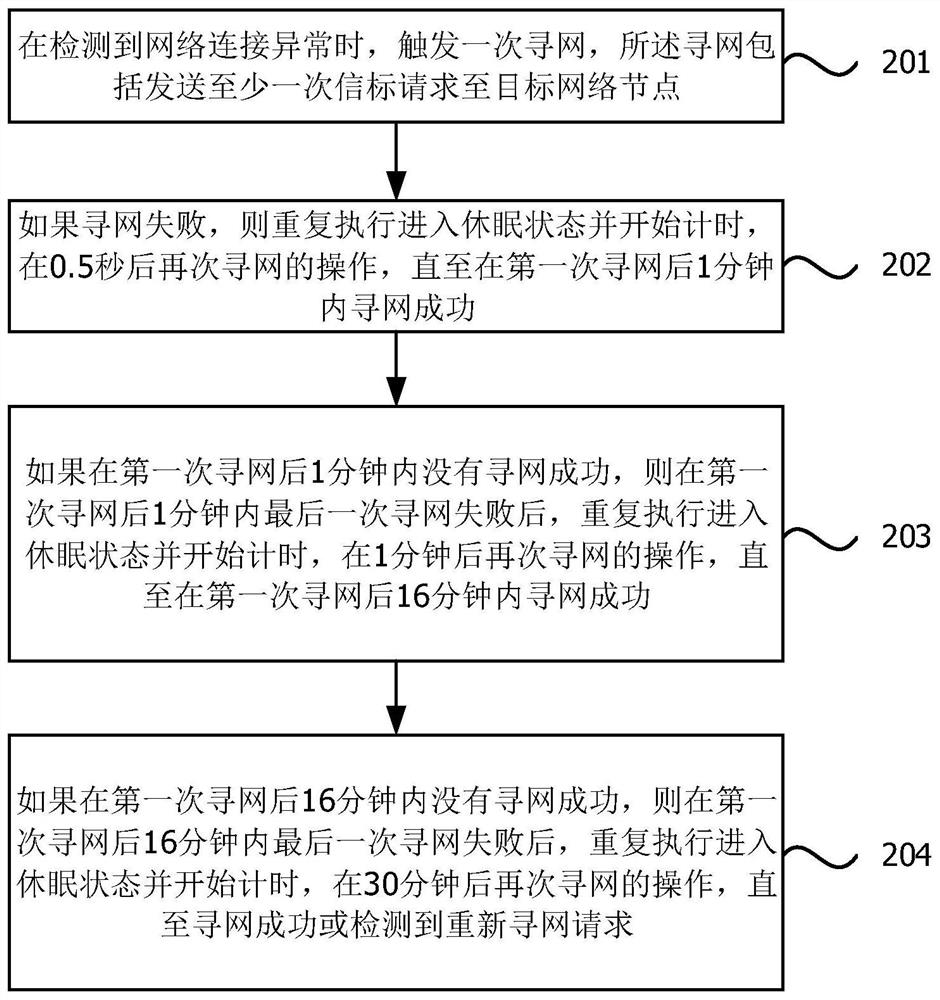
[0051] figure 2 It is a flow chart of a method for finding a network of an Internet of Things security sensor provided by Embodiment 2 of the present invention. The embodiment of the present invention can be combined with each optional solution in the above-mentioned one or more embodiments. In the embodiment of the present invention, the first network hunting interval is 0.5 seconds, and the first time node is the first network hunting After 1 minute, the second network hunting interval is 1 minute, the second time node is 15 minutes after the first time node, and the third network hunting interval is 30 minutes.
[0052] Such as figure 2 As shown, the method of the embodiment of the present invention specifically includes:
[0053] Step 201. When an abnormal network connection is detected, a network search is triggered, and the network search includes sending a beacon request to a target network node at least once.
[0054] Step 202, if the network search fails, repeat ...
Embodiment 3
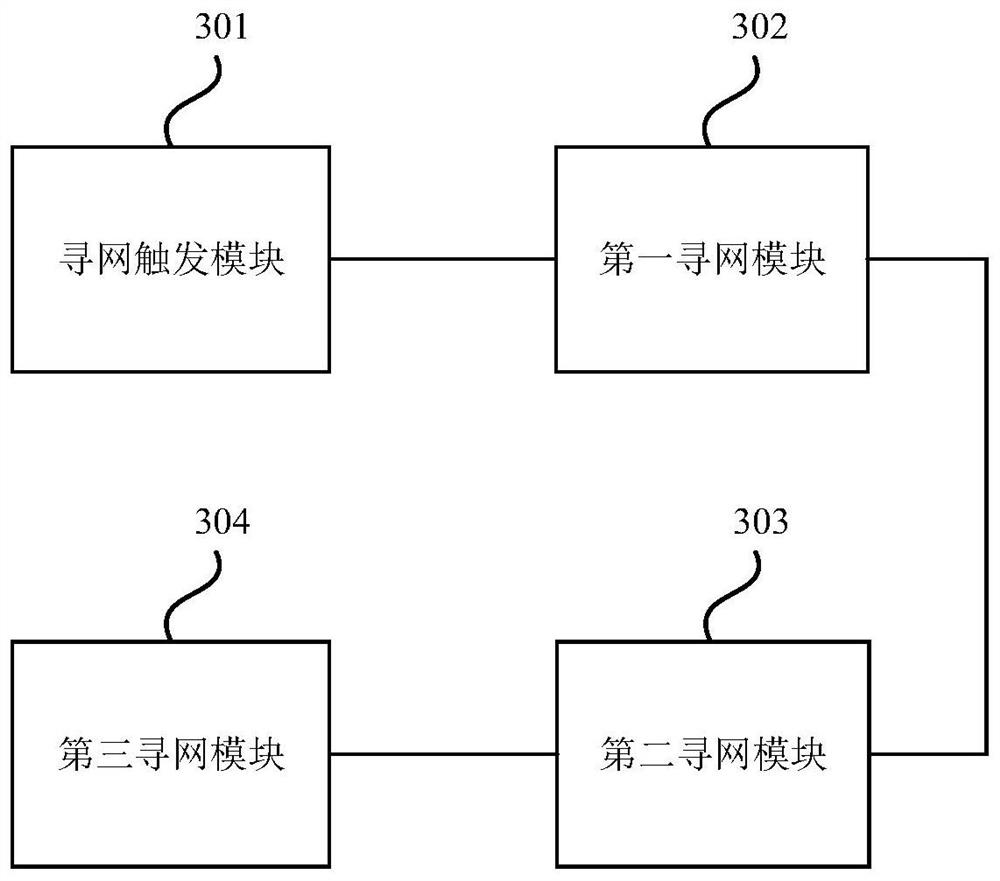
[0064] image 3 A schematic structural diagram of an Internet of Things security sensor network finding device provided by Embodiment 3 of the present invention, as shown in image 3 As shown, the device includes: a network hunting trigger module 301 , a first network hunting module 302 , a second network hunting module 303 and a third network hunting module 304 .
[0065] Wherein, the network hunting trigger module 301 is configured to trigger a network hunting when an abnormal network connection is detected, and the network hunting includes sending at least one beacon request to the target network node; the first network hunting module 302 is used to If the network fails, repeat the operation of entering the dormant state and start timing, and search the network again after the first network search interval until the network search succeeds before the first time node; the second network search module 303 is used to If there is no successful network search before the time no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com