Sybil attack node detection method and device considering sensor errors
A technology of witch attack and detection method, applied in security devices, transmission monitoring, transmission systems, etc., can solve the problems of not considering the physical measurement error of sensors, increase communication pressure, leak user privacy, etc., to accelerate intelligent development and improve The effect of driving safety and ensuring rationality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The technical solution of the present disclosure will be described in detail below in conjunction with the accompanying drawings.
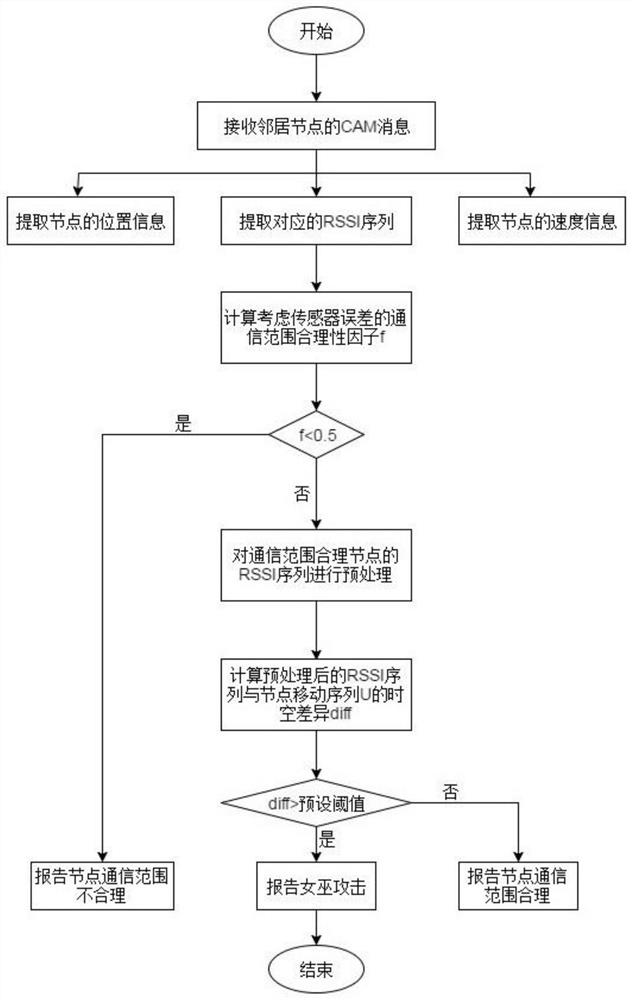
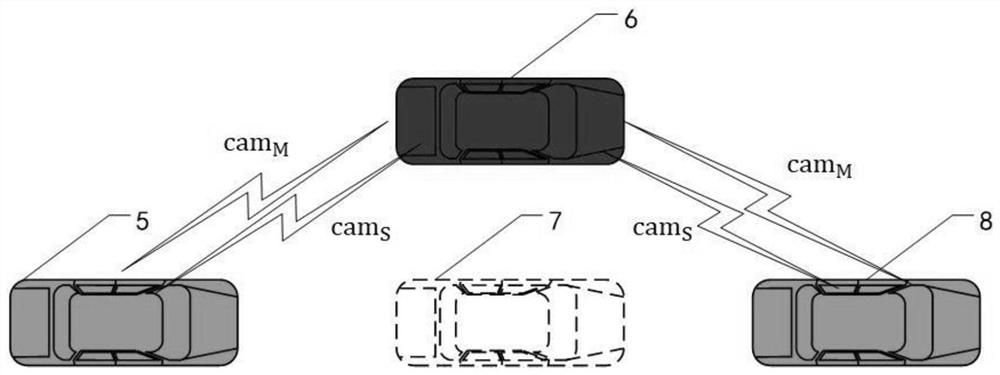
[0039] In the description of the present disclosure, it should be understood that the terms "first" and "second" are used for description purposes only, and cannot be interpreted as indicating or implying relative importance or implicitly indicating the quantity of indicated technical features, Used only to distinguish different components. In this application, "first node" generally refers to all neighbor nodes. Similarly, "first CAM (cooperative awareness message, cooperative awareness information) message" means a cooperative broadcast message broadcast by neighbor nodes in real time; All communication nodes with communication range rationality factor f.
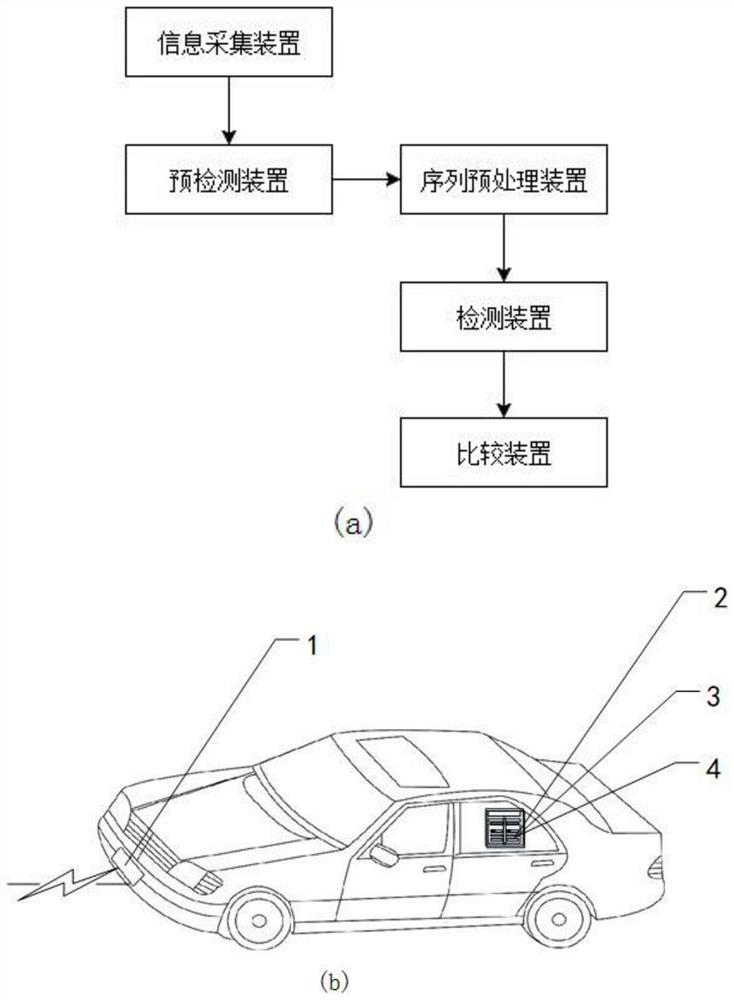
[0040] figure 1 It is a schematic diagram of the disclosed process, such as figure 1 As shown, the normal vehicle node receives the first CAM message broadcast by the first node, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com