Mobile PC divulgence prevention device based on user track after departing from predetermined track
A technology of predetermined trajectory and user trajectory, applied in encryption devices with shift registers/memory, services based on location information, secure communication devices, etc., can solve problems such as user information leakage, hidden dangers of people's information security, etc., to prevent Effects of data breaches
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
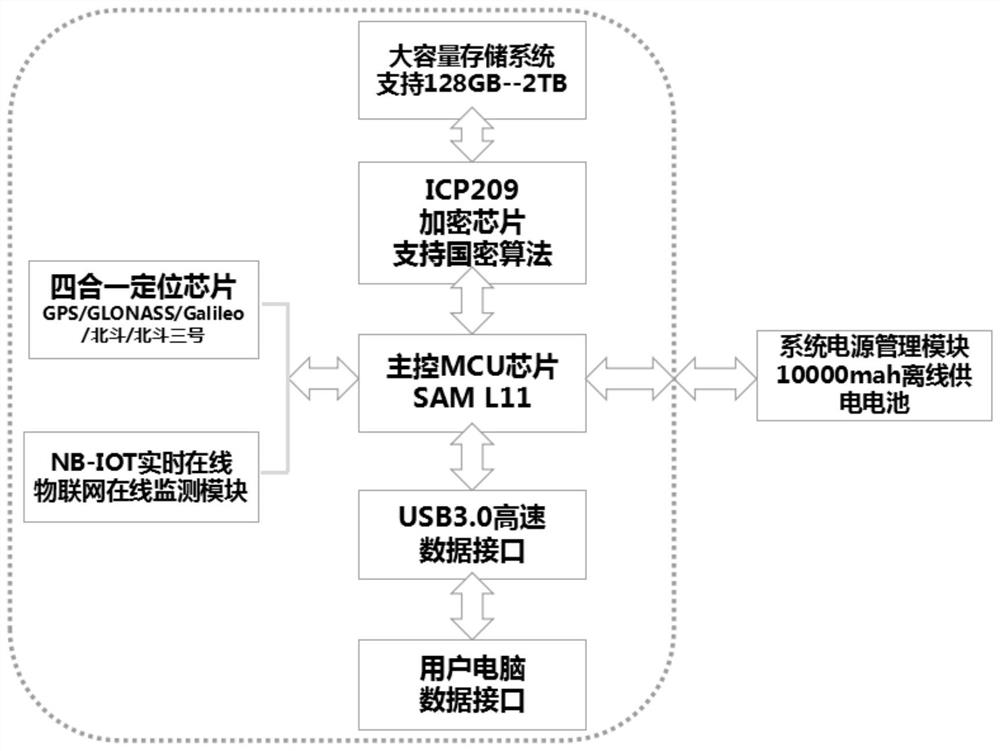
[0018] Example 1: See Figure 1-3 , a mobile PC based on the user's trajectory to prevent leaks after leaving the predetermined trajectory, including a large-capacity storage system, a four-in-one positioning chip, an encryption chip, a main control MCU chip, NB-IOT real-time online Internet of Things online monitoring module, USB3. 0 high-speed data interface, user computer data interface and system power management module. Monitoring module, USB3.0 high-speed data interface, user computer data interface power supply, main control MCU chip is also connected with encryption chip, four-in-one positioning chip, NB-IOT real-time online Internet of Things online monitoring module and USB3.0 high-speed data interface, The encryption chip is also connected to the large-capacity storage system, and the USB3.0 high-speed data interface is also connected to the data interface of the user's computer.
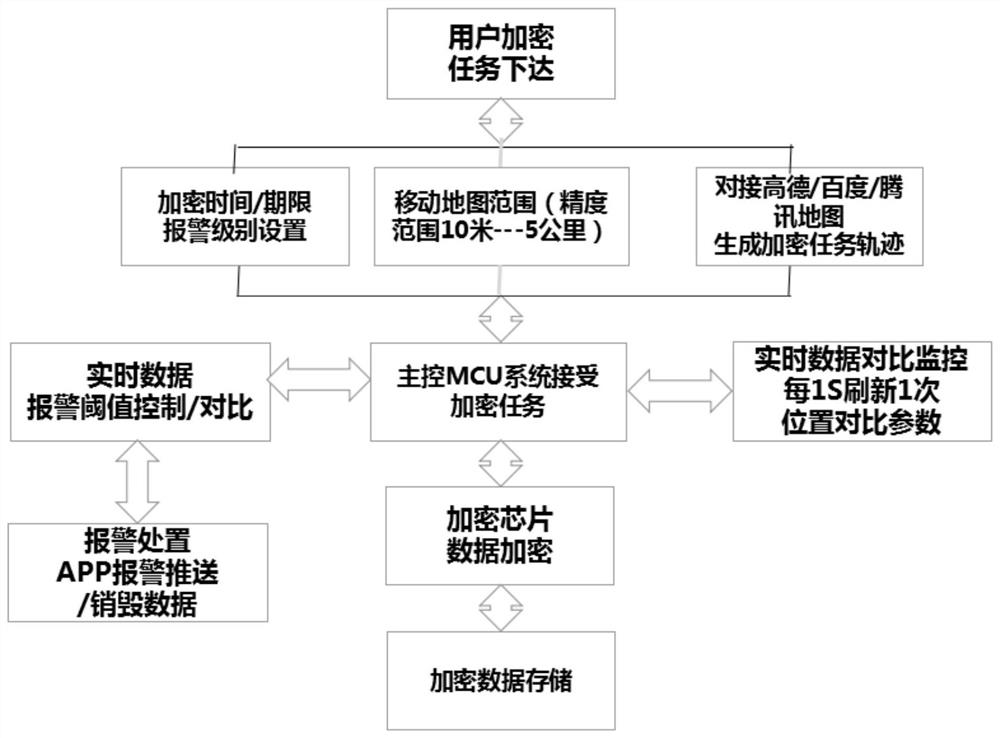
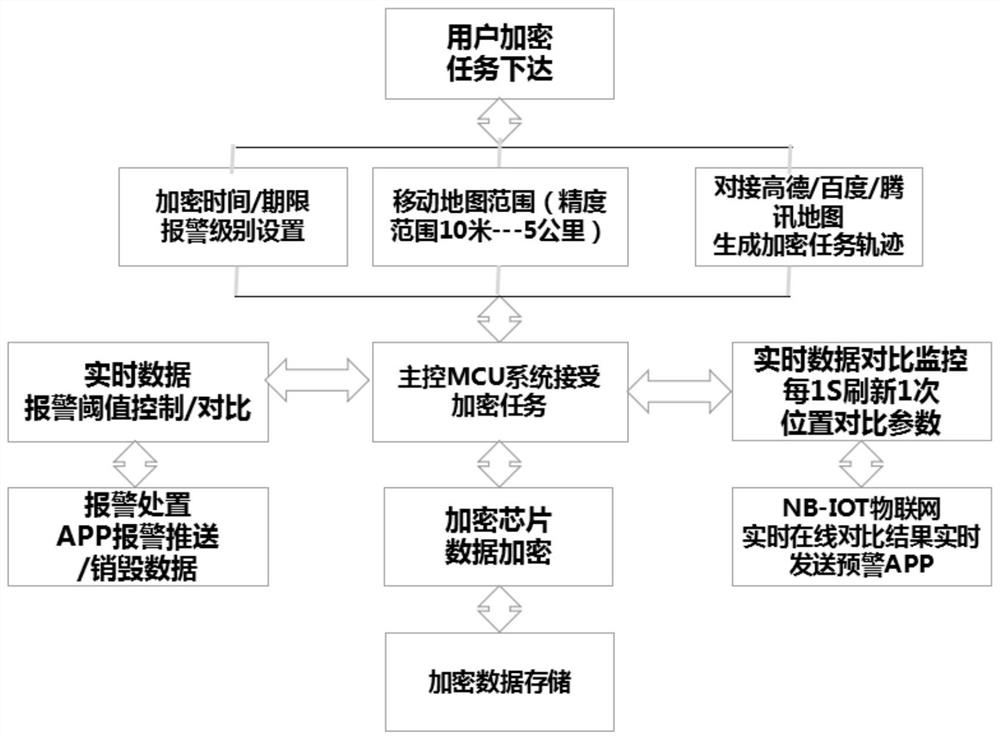
[0019] User management software function: set encryption tasks, connect encryption e...
Embodiment 2
[0029] Embodiment 2: On the basis of Embodiment 1: the system power management module includes a 10,000mah battery, which ensures that the device can be used for 2-3 months without power, and is automatically charged when plugged in / connected to a PC.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com