Quantum key management method and system based on block chain
A technology of quantum key and management method, which is applied in the field of quantum key management based on blockchain, can solve the problems of key update, difficult implementation of supervision, and less research content, so as to protect security, ensure correctness, The effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
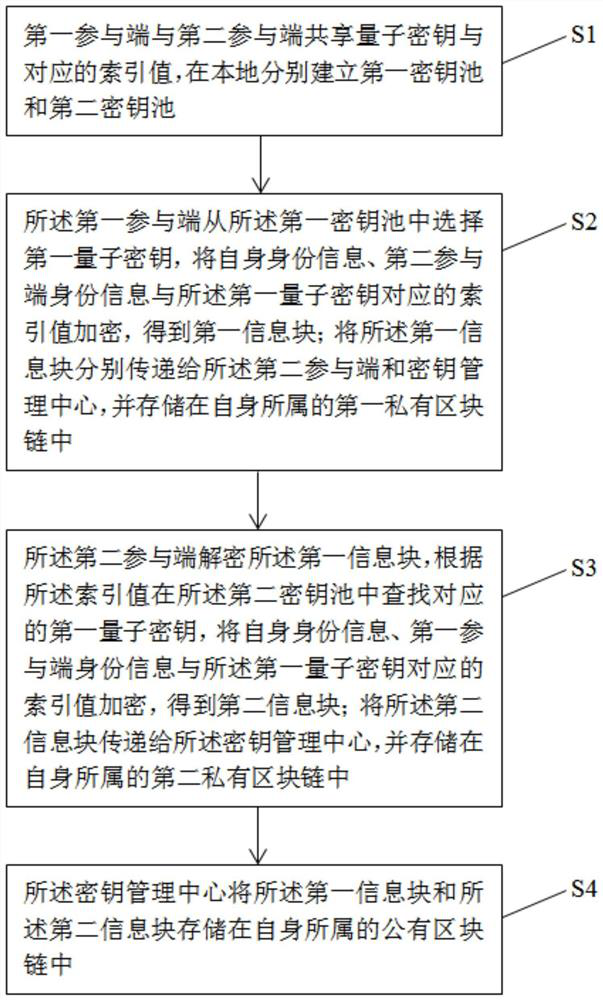
[0041] Such as figure 1 As shown, a blockchain-based quantum key management method includes the following steps:
[0042] Step S1. The first participant and the second participant share the quantum key and the corresponding index value, and respectively establish the first key pool and the second key pool locally.
[0043] In the present invention, the quantum key sequence is shared between the first participating terminal and the second participating terminal through the QKD device, and the QKD device can use an internationally accepted quantum key distribution protocol, such as the BB84 protocol, the B92 protocol or the E91 protocol for the distribution of quantum key sequences. The number of quantum keys in the key pool can be set as required.
[0044] Step S2. The first participant selects a first quantum key from the first key pool, and encrypts its own identity information, the identity information of the second participant, and an index value corresponding to the firs...
Embodiment 2
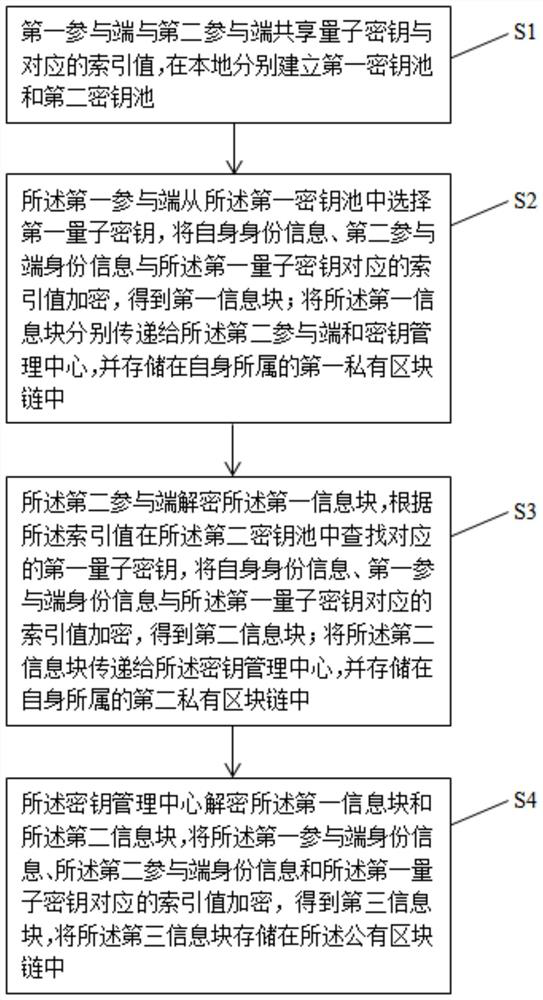
[0060] Such as Figure 4 As shown, in order to further improve the security of communication, the present invention also sets the updating and destroying steps of the key, specifically including:
[0061] Step S6. Set the key update time. When the update time is reached, the first participant and the second participant share the new quantum key and the corresponding index value, respectively adding to their respective key pools , and destroy the expired quantum keys and corresponding index values in their respective key pools.
[0062] Wherein, the update time is set synchronously when the key is generated, and each key can be set individually, or a common update time can be set for multiple keys. Regardless of the setting method, when performing an update operation, the generation of a new key and the destruction of an old key must be performed simultaneously. If the key is in use when updating, the old key will be transferred to the cache database first, and when the par...
Embodiment 3
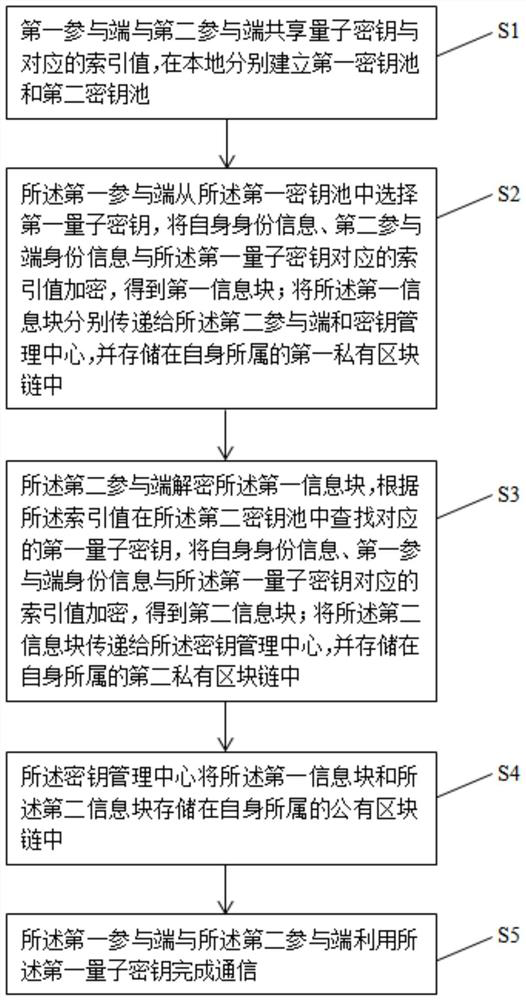
[0067] Such as Figure 5 As shown, in this example, considering that it is difficult to implement one-to-one key sharing and management each time, in order to facilitate the management of multiple communication participants, the following embodiments are provided, including:
[0068] Step S1. The first participating terminal and the second participating terminal share the quantum key and the corresponding index value, respectively establish the first key pool and the second key pool locally; the first participating terminal has several first slaves end; the second participating end has a plurality of second slave ends.
[0069] Step S2. The first slave transmits its own identity information and the identity information of the second slave to be communicated to the first participant; the first participant selects from the first key pool The first quantum key encrypts the identity information of itself, the identity information of the second participant, the identity informatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com