Design method of SoC (System on Chip) security disk control chip architecture for trusted storage
A credible and safe technology, which is applied in general stored program computers, architectures with a single central processing unit, computer security devices, etc., can solve the problem of lack of independent design capabilities, insufficient reliability of security disk control chips, and inability to implement encryption Algorithms can be dynamically configured and other issues to achieve the effect of ensuring data security, ensuring data read and write speed, and realizing bandwidth expansion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The technical solutions provided by the present invention will be further described below in conjunction with the accompanying drawings.
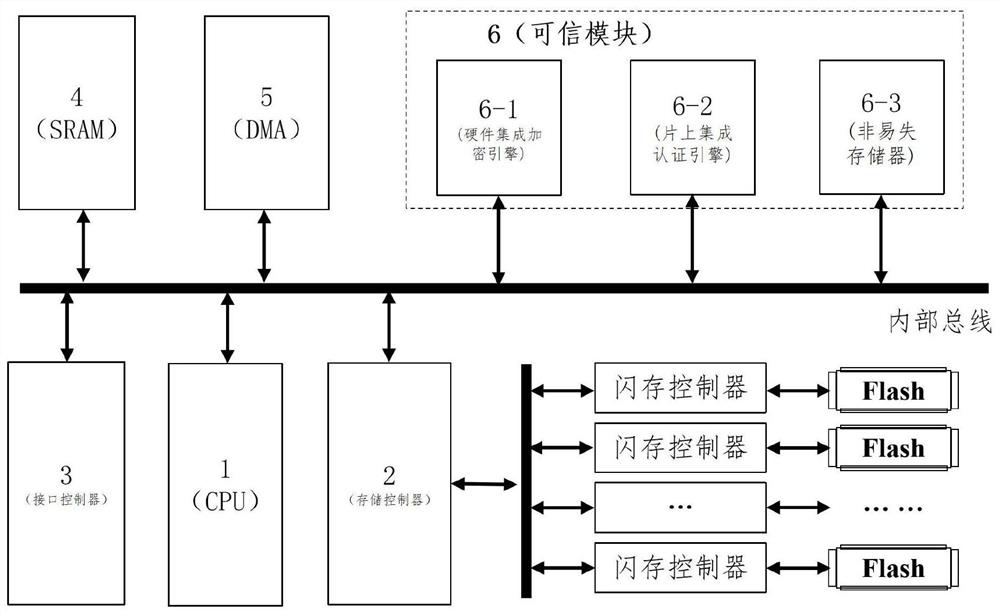
[0038] Such as figure 1 As shown, a SoC security disk control chip architecture for trusted storage includes a central processing unit 1 (CPU), a storage controller 2, an interface controller 3, a buffer 4 (SRAM), a direct access channel 5 (DMA ) and trusted module 6. Central processing unit 1 is connected with storage controller 2, interface controller 3, trusted module 6, direct access channel 5 and cache memory 4 through internal bus; cache memory 4 (SRAM) is used for data cache; direct access channel 5 (DMA) is used for direct access of data between external data and cache (Buffer). The storage controller 2 is connected to multiple flash memories through multiple flash controllers to read and write data on the hard disk.
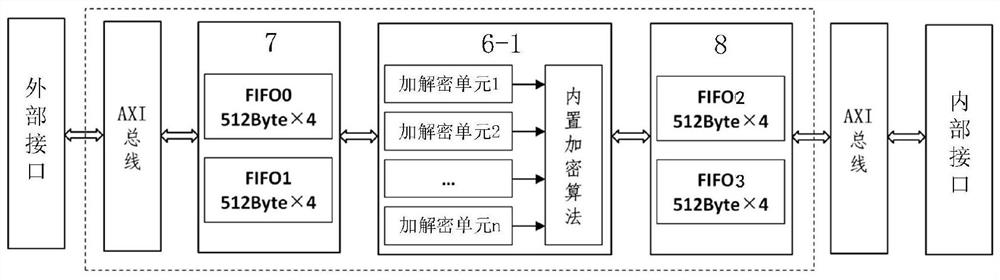
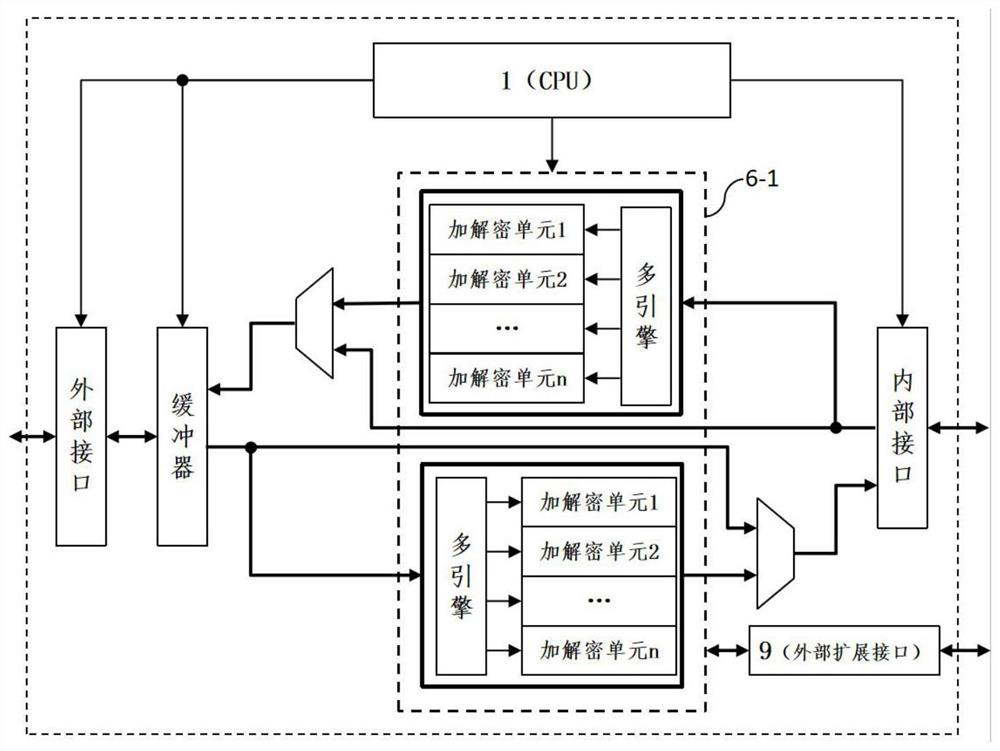
[0039] The trusted module 6 includes a parallel hardware encryption engine 6-1, an on-chip integrated aut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com