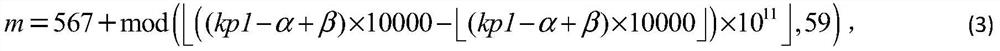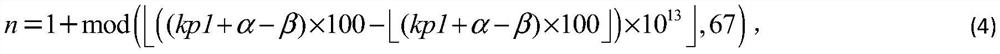Commodity anti-counterfeiting code generation method based on Chinese character encryption
A technology of commodity anti-counterfeiting codes and Chinese characters, applied in the field of digital anti-counterfeiting, can solve the problems of high cost and low operability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
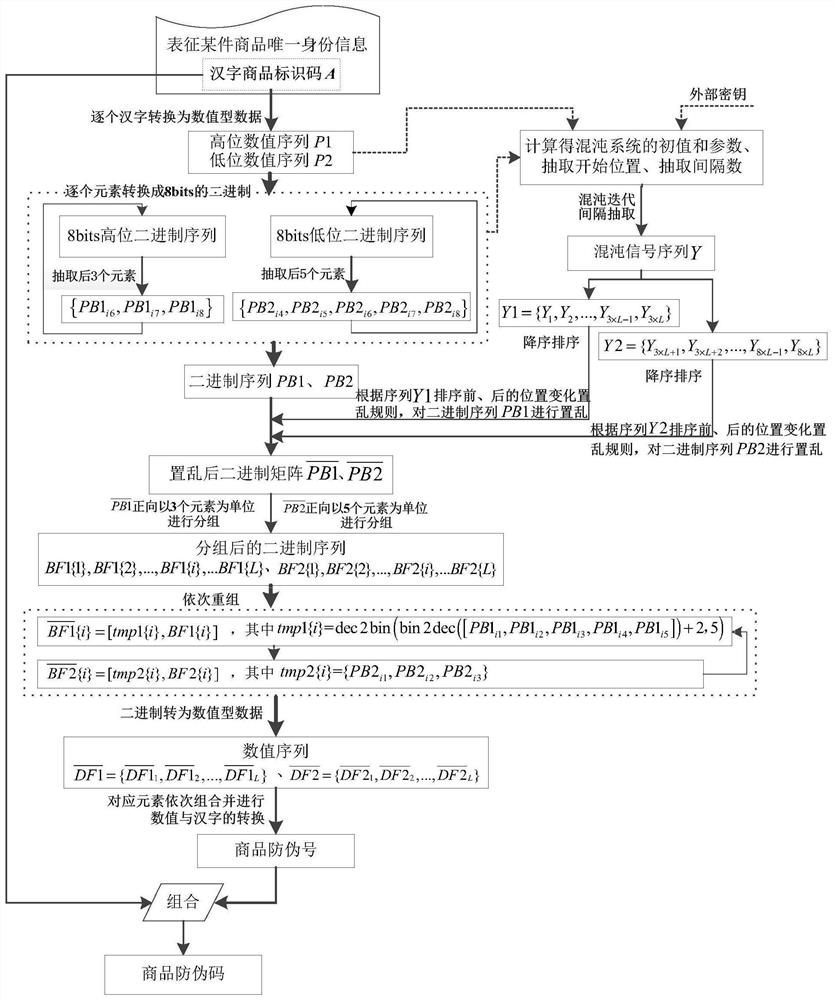
[0084] According to the above-mentioned method for generating an anti-counterfeit code based on Chinese character encryption, the steps are as follows:
[0085](1) First, the Chinese character product identification code A = "江苏省##集团××subsidiary@@commodity production date 2020-02-01 production line 12 serial number 123456", which represents the unique identity information of a product, is converted into Chinese characters one by one 为数值型数据,得到高位数值序列P1={189,203,202,163,163,188,205,161,161,215,185,203,161,163,163,201,198,161,201,178,200,198,163,163,163,163,163,163,163,163,163,163,161,201,178,207,163,163,208,193,186,163,163,163,163,163,163}和低位数值序列P2={173,213,161,163,163,175,197,193,193,211,171,190,161,192,192,204,183,161,250,250,213,218,178,176,178,176,173,176,178,173,176,177,161,250,250,223,177,178,242,208,197,177,178,179,180,181,182}。
[0086] Then, the element P in the high-digit value sequence P1 is sequentially i1 Convert one by one into 8bits binary sequence {PB1 i1 ,PB1 i2...
Embodiment 2
[0111] According to the above-mentioned product anti-counterfeiting code generation method based on Chinese character encryption, the product identification code character string A of a certain product and its product anti-counterfeiting code generation steps are similar to the specific embodiment 1, only a slight change occurs in a certain external key: α= 0.12345000000001; or β=3.749999999999999, the generation result of the commodity anti-counterfeiting code is shown in Table 1. It can be seen from the table below that once the external key changes slightly, the generated product anti-counterfeiting number and product anti-counterfeiting code will change greatly. It can be seen that a method for generating a product anti-counterfeiting code based on Chinese character encryption proposed in this patent has the advantages of encryption. key sensitivity.
[0112] Table 1 When the external key changes slightly, the product anti-counterfeiting code generation results
[0113] ...
Embodiment 3
[0116] According to the above-mentioned method for generating an anti-counterfeit code based on Chinese character encryption, the steps for generating the external key and its anti-counterfeit code are similar to those in Embodiment 1, only the string A of the product identification code of a certain product undergoes a slight change: "Jiangsu Province ##Group ××subsidiary@@commodity production date 2020-02-01 production line 12 serial number 123456"; or "Jiangsu Province##Group ××subsidiary@@commodity production date 2020-12-01 production line 12 serial number 123456 "; or "Jiangsu Province ##Group ×× Subsidiary @@ Commodity Production Date 2020-02-01 Production Line 12 Serial Number 123459", the product anti-counterfeiting code generation results are shown in Table 2. It can be seen from the following table: once the product identification code character string representing the unique identity information of a certain product changes slightly, the generated product anti-count...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com