Log monitoring method for behavior anomaly detection based on deep learning improved IFOREST
A deep learning and anomaly detection technology, applied in the field of network security, can solve problems such as long running time and achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
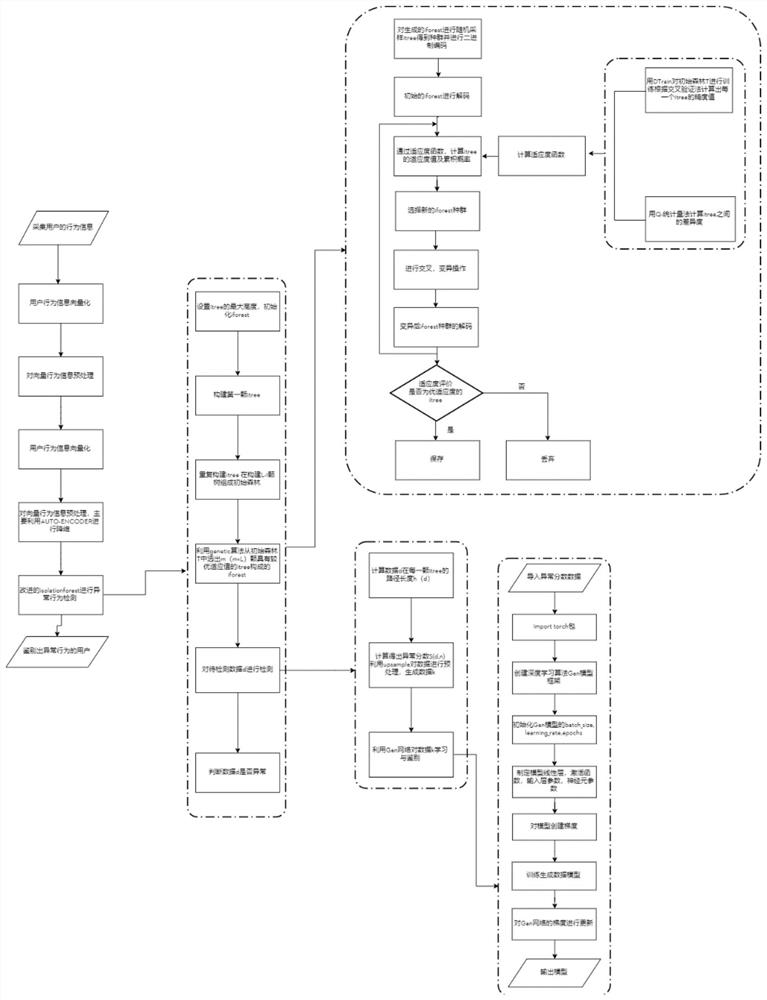
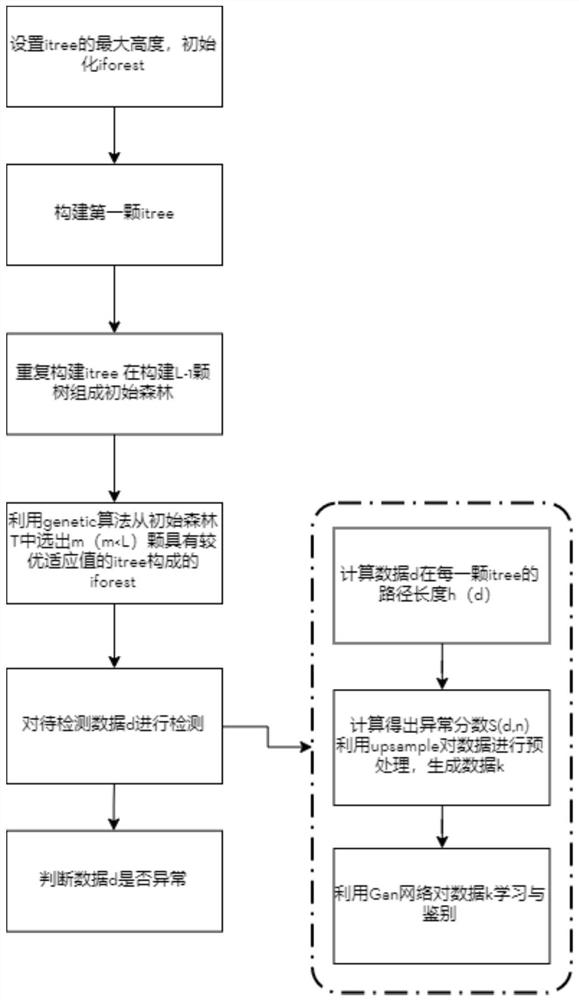
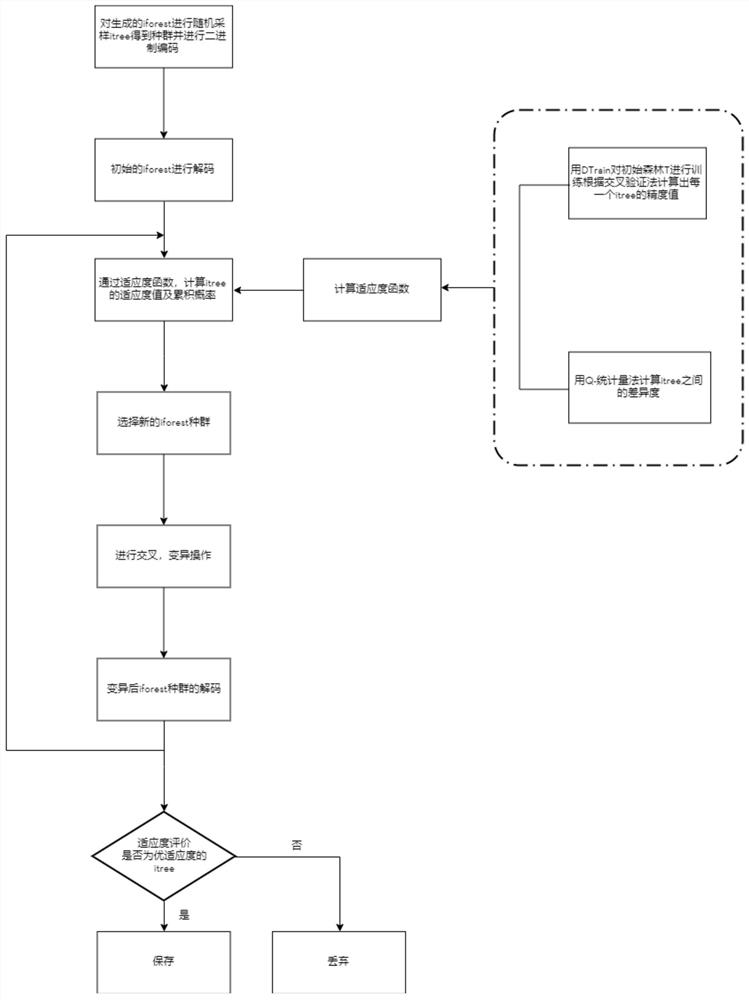
[0058] A log monitoring method based on deep learning to improve IFOREST for abnormal behavior detection, the specific operation steps are as follows:
[0059] Step 1, use the log user information generated in the platform system to extract, and take the user's operation on the database as an example to make long-term statistics on the number of operations performed by the user on different behaviors such as adding tables, deleting tables, changing tables, and looking up tables every day , generate user log behavior vectors and store them in MySQL;
[0060] Step 2. Obtain the log user behavior vector and use Auto-Encoder to reduce the dimensionality. According to the ratio of 8:2, the data is randomly divided into the user behavior training set and the user behavior test set. The user behavior training set is used to train and generate user b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com