Network security defense method and system, effect evaluation method and related device thereof
A network security and defense system technology, applied in the fields of related devices, systems and their effect evaluation methods, and network security defense methods, can solve the problems of computing technology cyberspace full of risks and uncertain threats, and achieve the ultimate goal of solving endogenous security problems. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
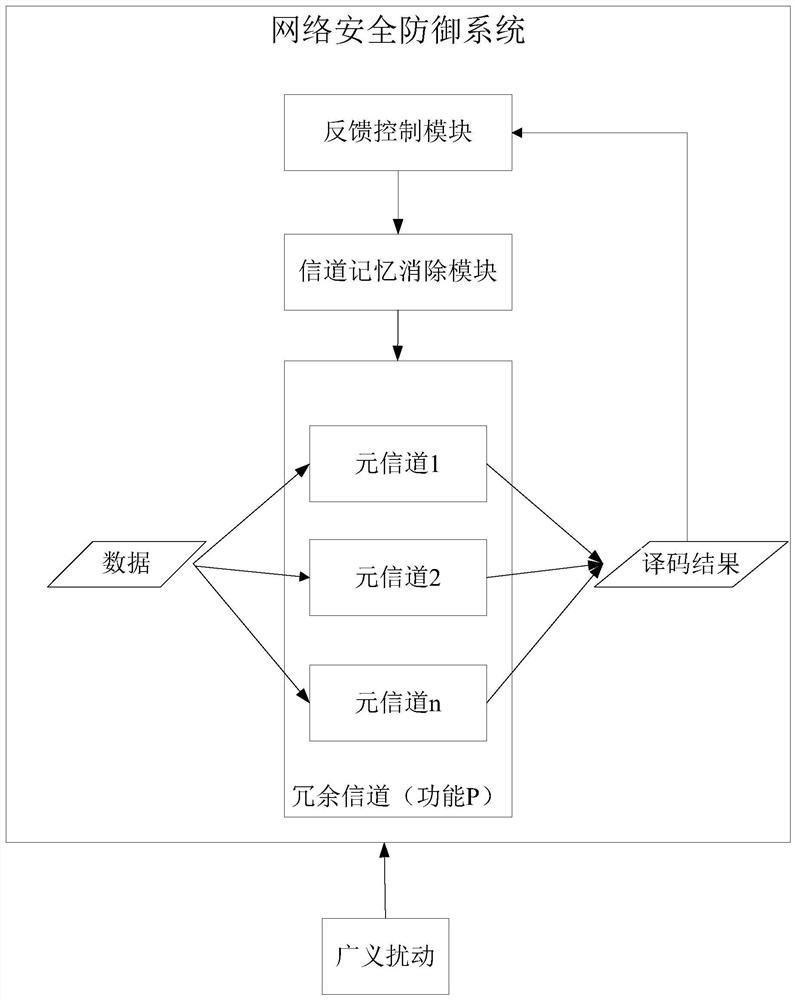
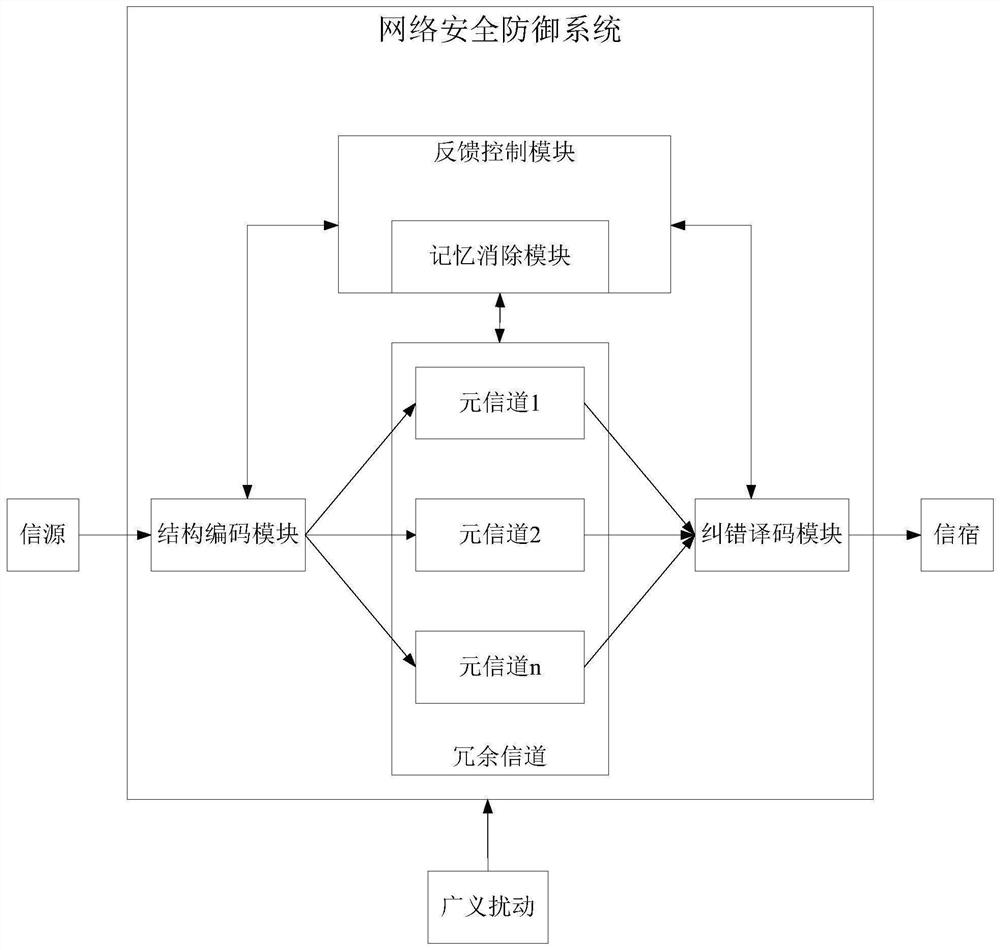
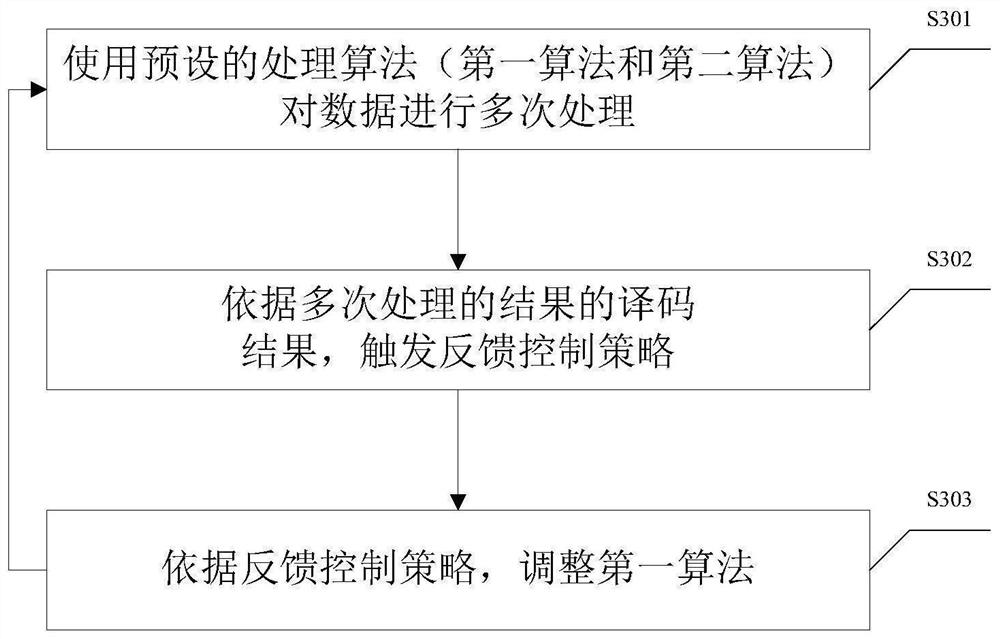
[0047] The construction principle of the dynamic heterogeneous redundant memory elimination device and the network security defense system disclosed in the embodiment of the present application is as follows:
[0048] 1. The applicant proposed the definition and connotation of endogenous security issues
[0049]The cyberspace of the information world has the same philosophical essence as the physical space of the real world: "everything is a self-generated (endogenous) contradiction, and contradiction is the root of all movement and vitality." The identity of contradictions is the prerequisite for the existence and development of things, and they are the conditions for the development of each other. The fighting nature of the contradiction will promote the ebb and flow of the two sides of the contradiction, resulting in an unbalanced development of the forces of both sides, and creating conditions for the transformation of opposites and the qualitative change of things. Takin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com