Signature management method and device and electronic equipment
A management method and electronic signature technology, applied in computer security devices, data processing applications, electronic digital data processing, etc., can solve the problems of information leakage, high security requirements of third-party platforms, etc., and achieve the effect of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0055]In order to facilitate the understanding of this embodiment, firstly, an operating environment for executing a signature management method disclosed in the embodiment of the present application is introduced in detail.
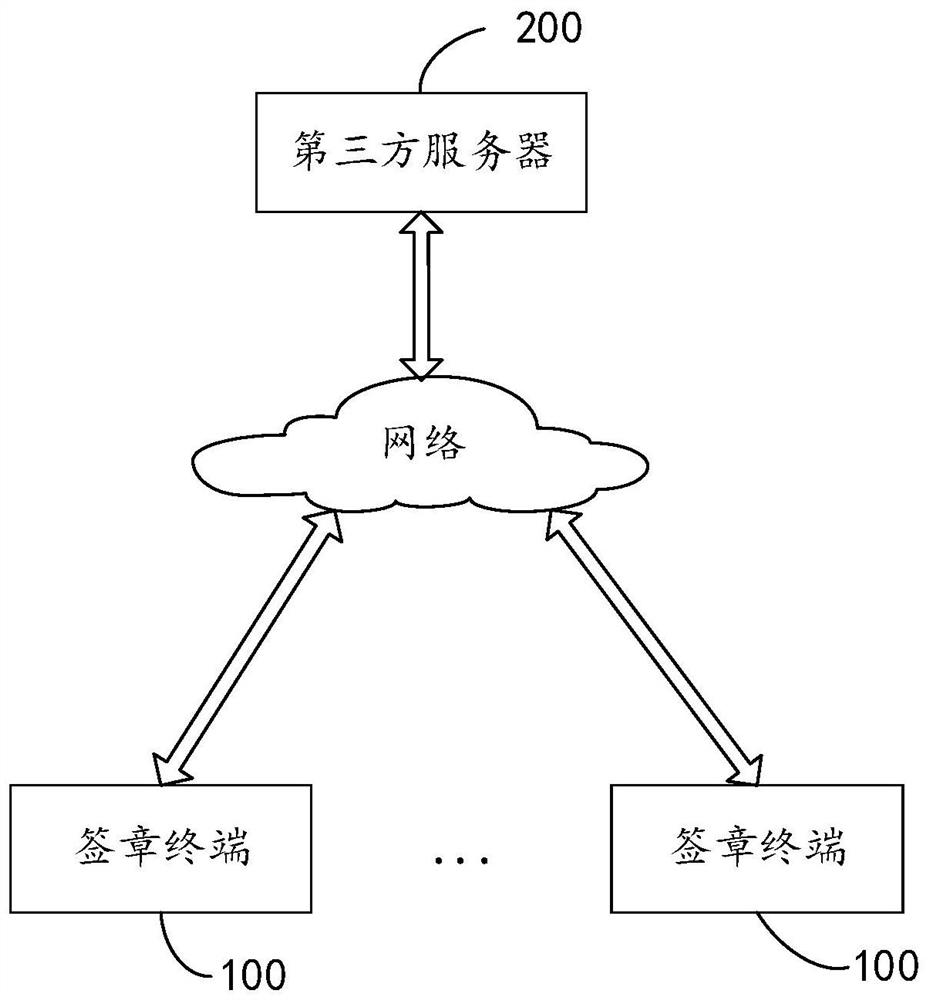
[0056] Such as figure 1 Shown is a schematic diagram of the signature management system provided by the embodiment of the present application. The signature management system includes: a signature terminal 100 and a third-party server 200 .
[0057] The third-party server 200 communicates with one or more signing terminals 100 through the network for data communication or interaction. The third-party server 200 may be a web server, a database server, and the like. The signature terminal 100 may be a personal computer (personal computer, PC), a tablet computer, a smart phone, a personal digital assistant (personal digital assistant, PDA) and the like.
[0058] In this embodiment, the third-party server 200 is used to store the signature data sent by th...
Embodiment 2
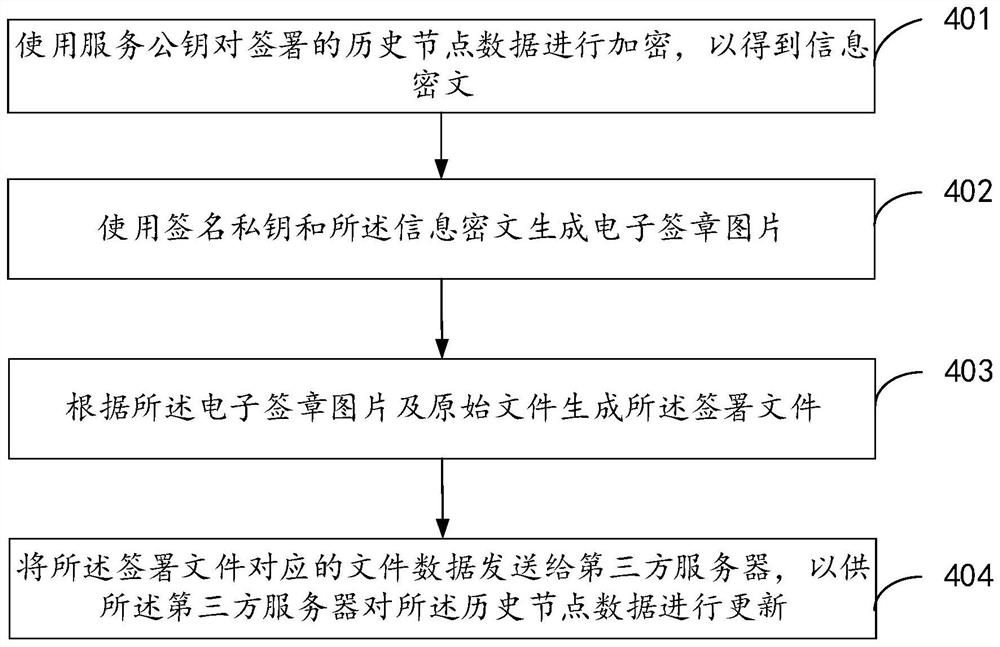
[0072] see image 3 , is a flow chart of the signature management method provided in the embodiment of the present application. The following will be image 3 The specific process shown will be described in detail. Optionally, the signature management method in the embodiment of the present application can be applied to a signature terminal.
[0073] Step 401, use the service public key to encrypt the signed historical node data to obtain information ciphertext.
[0074] Optionally, the above service public key may be provided by a third-party server.
[0075] Optionally, before generating the information ciphertext, it may also be judged whether the historical node data is the latest historical node data. If the current storage of the signing terminal is not the latest historical node data, first obtain the latest historical node data, and then encrypt the signed historical node data with the service public key to obtain the information ciphertext.
[0076] Exemplarily, ...
Embodiment 3
[0127] Based on the same application concept, the embodiment of the present application also provides a signature management device corresponding to the signature management method. Since the problem-solving principle of the device in the embodiment of the present application is similar to the aforementioned embodiments of the signature management method, this application For the implementation of the device in the embodiment, reference may be made to the description in the embodiment of the above method, and repeated descriptions will not be repeated.
[0128] see Figure 4 , is a schematic diagram of the functional modules of the signature management device provided in the embodiment of the present application. Each module in the signature management apparatus in this embodiment is used to execute each step in the above method embodiment. The signature management device includes: an encryption module 501, a first generation module 502, a second generation module 503, and a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com