Method for generating attack path and attack graph based on multiple dimensions
An attack path and attack graph technology, applied in the field of network security, can solve the problems of inability to accurately analyze the key vulnerability factors of the attack graph and low generation efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The technical solution of the present invention will be further described below in conjunction with the accompanying drawings.
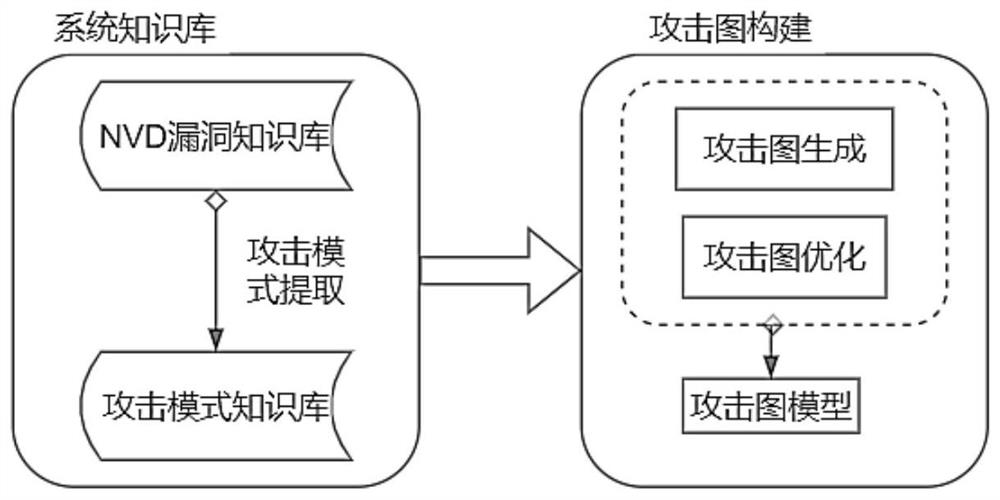
[0018] The overall process of multi-dimensional attack path and attack graph generation is as follows: figure 1 As shown, it mainly includes two steps of system knowledge base construction and attack graph construction.
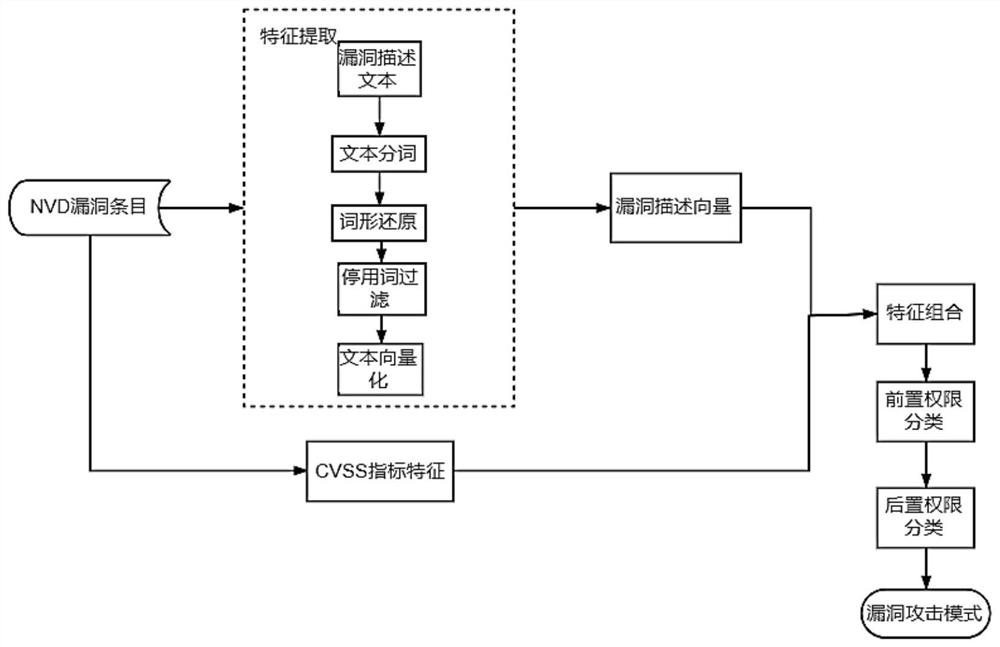
[0019] In the process of system knowledge base construction, the core step is attack pattern extraction.
[0020] An attack pattern represents the set of preconditions and corresponding attack consequences that an attacker needs to satisfy in order to successfully exploit a vulnerability to launch an attack. It is the inference rule of the attack graph construction algorithm. The present invention defines the attack mode as a 3-tuple . Among them, precondition is the prerequisite to exploit this vulnerability, which is divided into two metrics: (1) The reachability of the attack source and target host, which is divided into...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com