Intrusion detection system based on Internet of Things flow and detection method thereof
An intrusion detection system and intrusion detection technology are applied in the field of Internet of Things security to achieve the effect of improving detection rate, detection accuracy and reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
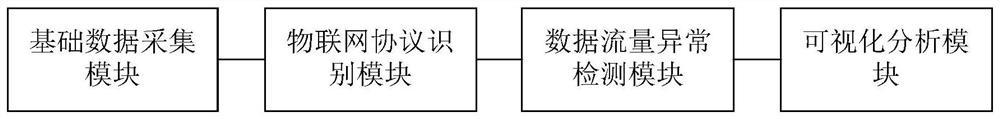
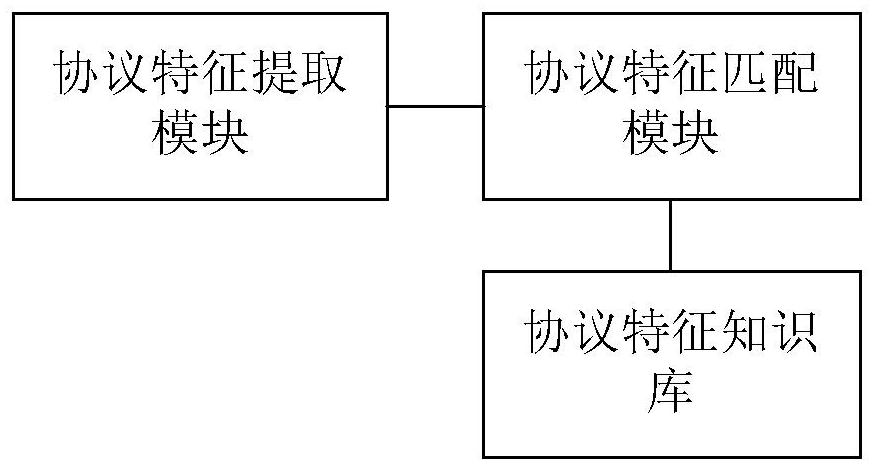
[0058] like figure 1As shown, the intrusion detection system based on the Internet of Things traffic of the present invention includes a basic data acquisition module, an Internet of Things protocol identification module connected with the basic data acquisition module, an abnormal data flow detection module connected with the Internet of Things protocol identification module, and A visual analysis module connected with the data traffic anomaly detection module.
[0059] Specifically, the basic data acquisition module runs or is mounted in a third-party device of the Internet of Things, which is used to collect network data traffic in the Internet of Things environment, generate initial data of the data flow, and transmit the initial data to the Internet of Things protocol Identification module; that is, the basic data acquisition module can capture the data packets flowing through the network card in real time on the Internet of Things link layer, and can also export the IoT ...
Embodiment 2
[0074] This embodiment adopts the detection method of the intrusion detection system based on the Internet of Things traffic in Embodiment 1, such as Figure 5 As shown, it specifically includes the following steps:
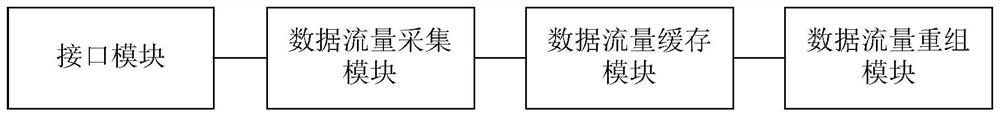
[0075] Step 1: The basic data acquisition module acquires the initial data of the IoT data stream. like Image 6 As shown, the basic data acquisition module obtains the initial data of the Internet of Things data flow including the following steps:
[0076] A. The basic data acquisition module is connected to the router, gateway or switch through the interface module on it. When the basic data acquisition module is started, the data flow acquisition module on the basic data acquisition module will start from the link layer of the Internet of Things or run on the The IoT data traffic packets are obtained from the devices in the Internet of Things environment, and the traffic packets are stored in the data traffic cache module. When the Internet of Things data t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com