A quantitative evaluation method and system for privacy protection in a multi-party data collaboration scenario
A privacy protection and data collaboration technology, applied in the field of network information, can solve problems such as high communication costs, leakage, and privacy attack models incorporated into the framework, and achieve the effect of improving matching capabilities and making full use of them
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
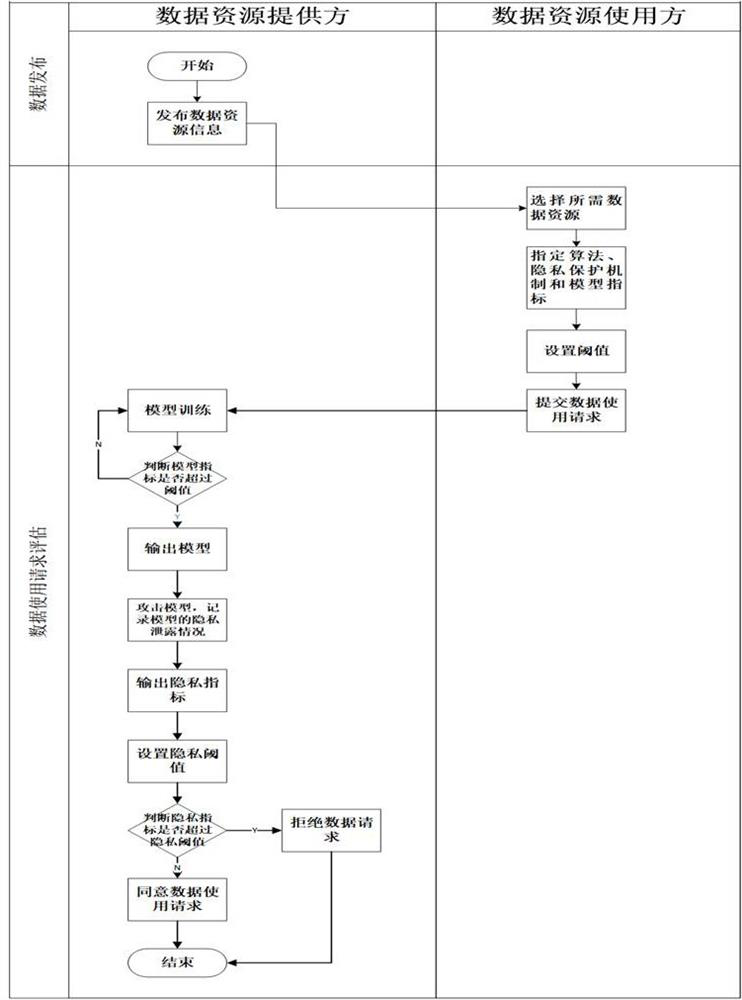
[0050] An implementation method for providing an assessment of a member inference attack in the data resource provider during the data usage process is as follows:
[0051] Data supplied with data resource providers Training model , Assume that the attacker does not understand with Basic situation, such as Structure and various training super parameters and Distribution, etc., but can only be used in black boxes That is, Provides N-dimensional vector input X, get the feedback M-dimensional vector output Y, where .
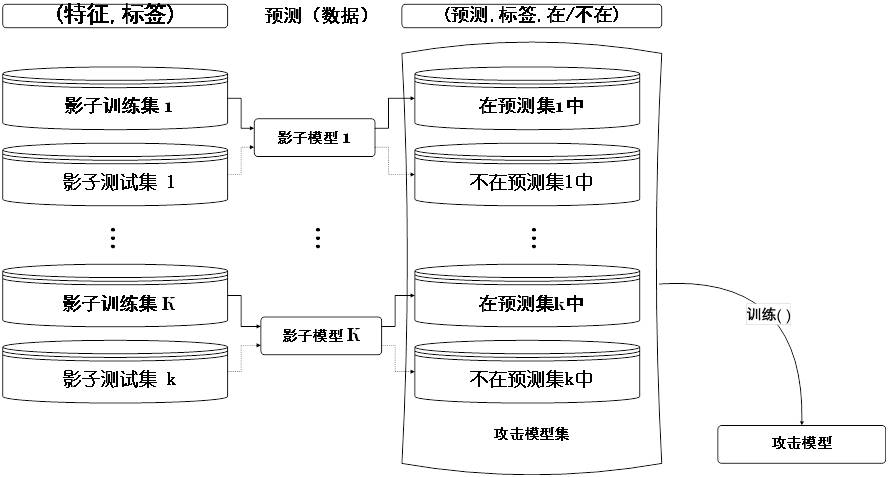
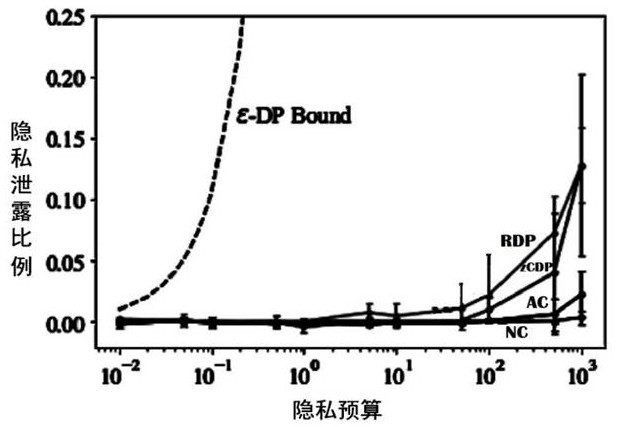
[0052] By repeated Send request, attacker can work with Similar large amounts of data samples Feature vector x Predict, it is possible to obtain a high confidence output vector That is, there is a certain dimension value that is significantly higher than other dimensions. . The value is 0.8. like figure 2 As shown, based on this data, the attacker can construct k group training and test data, and training for each set of data to get a shadow model.
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com