RST attack resistance stereo image zero watermark method based on FFST and Hessenberg decomposition
A stereoscopic image and zero watermark technology, applied in image data processing, image data processing, instruments, etc., can solve the problems of poor robustness, certified zero watermark structure and detection time, unable to resist rotation, etc. The method is simple , good translation invariance, and the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0047] The anti-RST attack stereo image zero watermarking method based on FFST and Hessenberg decomposition provided by the present invention comprises the following steps carried out in order:
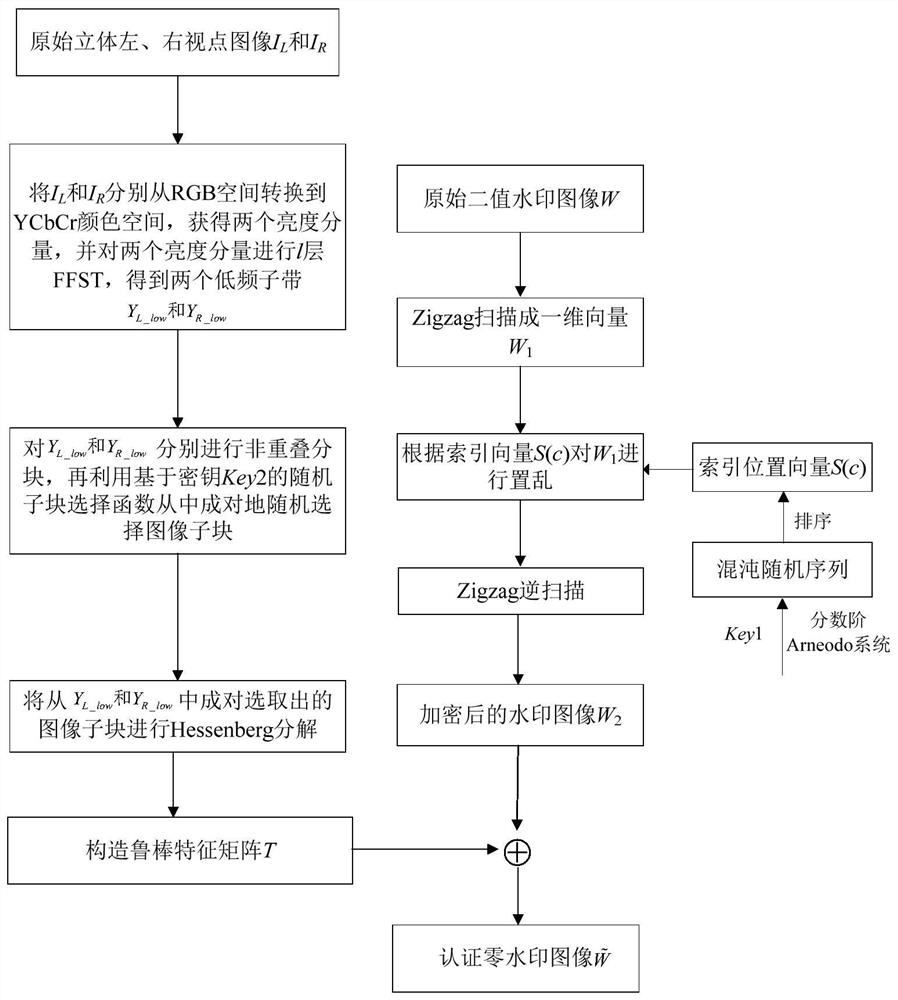
[0048] Step 1: If figure 1 As shown, the zero watermark is generated according to the feature information of the original stereo image;
[0049] Step 1.1: Zigzag-scan the original binary watermark image W of size n×n into a one-dimensional vector W 1 , and then use the fractional order Arneodo chaotic system to generate the length L(L=n 2 ) of three chaotic random sequences {P k |k=X, Y, Z}, the specific expression of the fractional order Arneodo chaotic system is as follows:
[0050]
[0051] Among them, b 1 , b 2 , b 3 , b 4 is the fractional order Arneodo chaotic system and control parameters, x 0 ,y 0 ,z 0 is the fractional order Ar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com