Patents
Literature
80results about How to "Solve the robustness problem" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
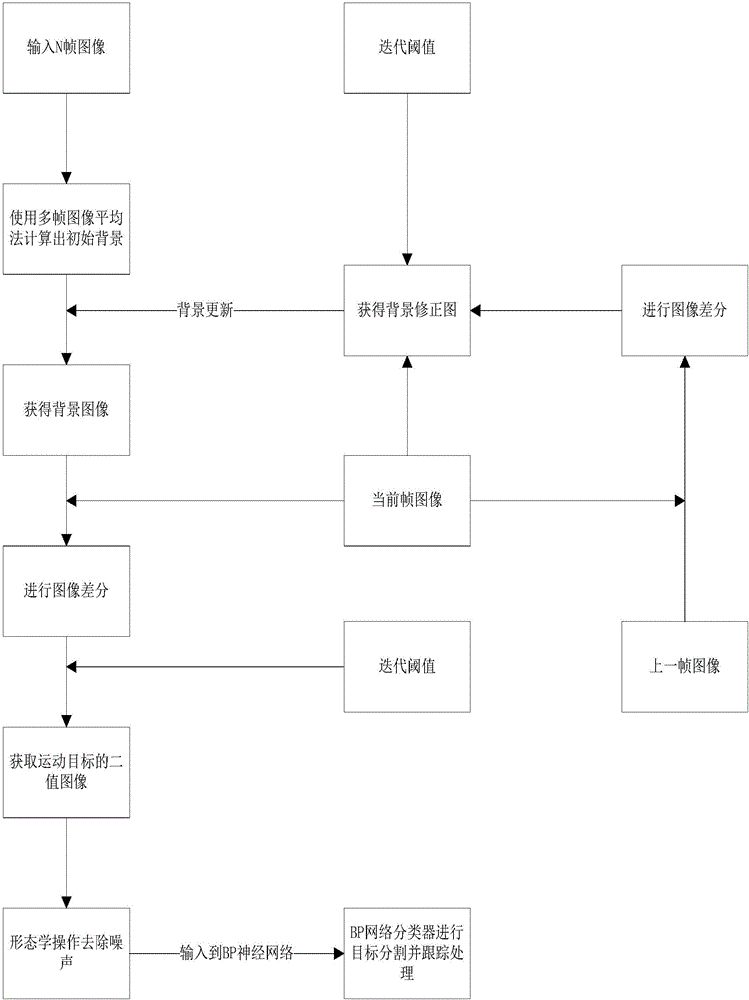
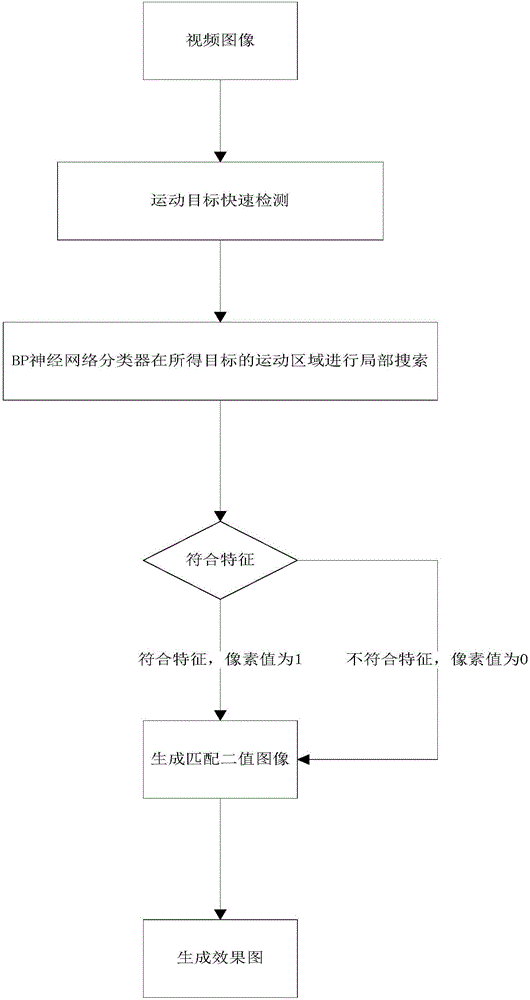
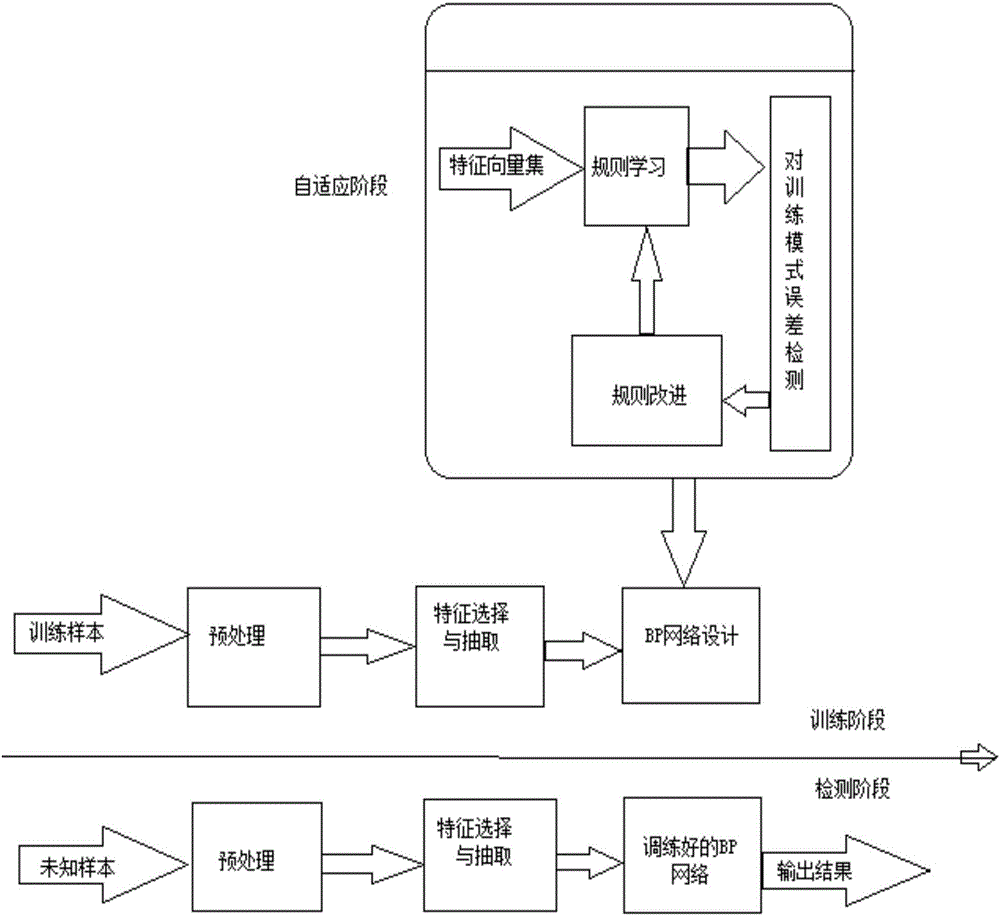
Multiple moving target tracking method based on BP neural network
InactiveCN106204646AStrong fault toleranceFast operationImage enhancementImage analysisFrame differenceVideo image
The invention discloses a multiple moving target tracking method based on a BP neural network and relates to the field of computer vision technologies. The method comprises the following steps of S1, performing fusion detection to obtain multiple moving targets based on the background difference method and the frame difference method; S2, subjecting a binarization image to further denoising, and inputting the processed image in the BP neural network for multiple target segmentation; and S3, performing multiple moving target tracking based on the BP neural network. The multiple moving target detection mainly comprises three steps of 1) establishing an initialization background model, 2) updating a background using the frame difference method and performing binarization, and 3) performing background difference using the background difference method, and then subjecting the image to binarization. The invention meets requirements for robustness and accuracy of the video image moving target detecting and tracking technology, reduces the computational complexity of neural network global search, and meets requirements for processing speed of the video image moving target detecting and tracking technology.
Owner:HUNAN VISION SPLEND PHOTOELECTRIC TECH
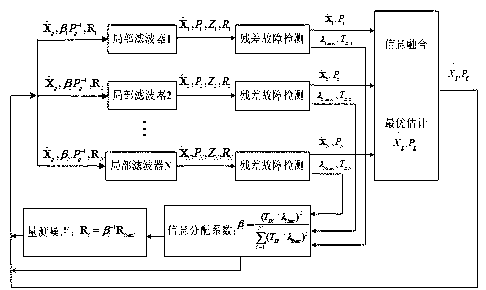
Robust federated filtering method based on time-variable measurement noise
ActiveCN103323007AImprove estimation performanceReduce the use of weightNavigational calculation instrumentsAviationFlight vehicle
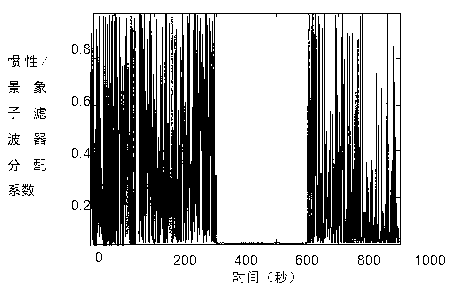
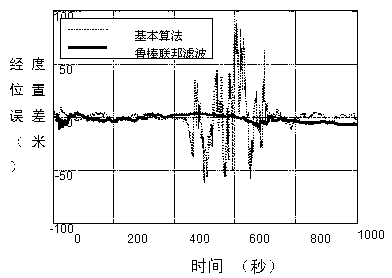
The invention discloses a robust federated filtering method based on time-variable measurement noise, belonging to the technical field of aircraft combined navigation. The method comprises the following steps of: firstly, establishing a fused reset federated filter of an airborne inertial navigation system and other navigation systems; constructing the time-variable measurement noise of various sub-filters according to a federated filtering information distribution coefficient; defining an optimal residual detection amount in a federated filtering sub-filter residual-chi-square fault detection method; on the basis, designing a dynamic federated filtering information distribution coefficient by virtue of the optimal residual detection amount of each sub-filter and a residual-chi-square fault detection threshold value; and finally, carrying out optimal estimation on an error state of inertial navigation by a robust federated filtering method.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Global positioning system satellite searching and scheduling method
ActiveCN101493511AImprove the odds of successImprove usabilityBeacon systems using radio wavesPosition fixationUrban forestSelf adaptive
The invention relates to the field of global satellite positioning and navigation, in particular to a satellite searching and dispatching method for a global positioning system (GPS); the method comprises three parts: a classifying satellite possibility dispatching method which comprises the steps as follows: the state of the satellite is judged by the obtained satellite information; each satellite is classified by the satellite state, thus presuming the searching scene further; according to the satellite classes and the searching scenes, different searching weights are arranged for each satellite so as to carry out the searching; a maintaining re-catching method for continuously searching the blocked satellites and a self-adaptive sensitiveness catching method which uses the catching methods of different sensitiveness by aiming at the satellites of different signal-noise-ratio. When the three methods are smartly used, the successful possibility of searching satellite is greatly improved, the time used for searching the satellite is reduced, the starting and positioning speed and the re-catching positioning precision are greatly improved, the power dissipation is reduced, and the problems of robustness and reliability in the satellite dispatching arithmetic are solved, thus improving the feasibility of the receiving machines in the urban forests where the blocking is severe, and greatly improving the experience of the user.
Owner:北京中科微知识产权服务有限公司
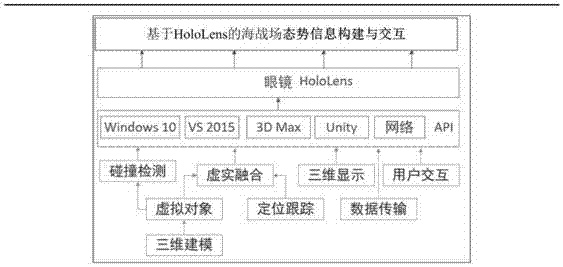
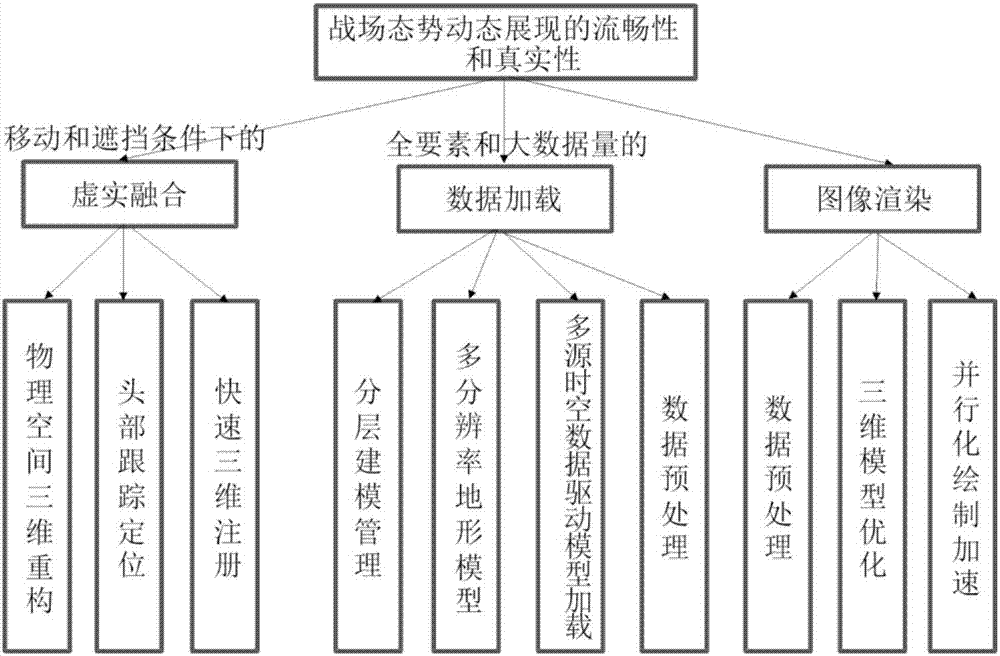
HoloLens-based battlefield situation construction and interaction implementation method
ActiveCN107479706AInteractive continuumAccurate interactionInput/output for user-computer interactionSpeech recognitionTerrainInteraction interface
The invention discloses a HoloLens-based battlefield situation construction and interaction implementation method. The method sequentially comprises the following steps of 1, firstly, sequentially constructing a terrain model, a three-dimensional object model and a three-dimensional military standard, and then adopting the mode of combining geometric characteristic optimization and grain optimization for performing model optimization; 2, sequentially achieving the purposes of battlefield situation dynamic showing fluency and authenticity and the purpose of three-dimensional virtual-real fusion; 3, performing user interaction. The method can achieve construction and interaction according to user identity roles, operation habits, interaction action tendencies and other natural human-machine interaction holographic battlefield situation electronic sand table information, the situation awareness fidelity and immersion can be enhanced, the method can intelligently and efficiently provide the imaginable and visual battlefield situation and visualized information interaction interface for commanders and the staff, and the method is used for supporting construction of intelligent information service systems of future advanced command posts with different fight persons and different operation patterns.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
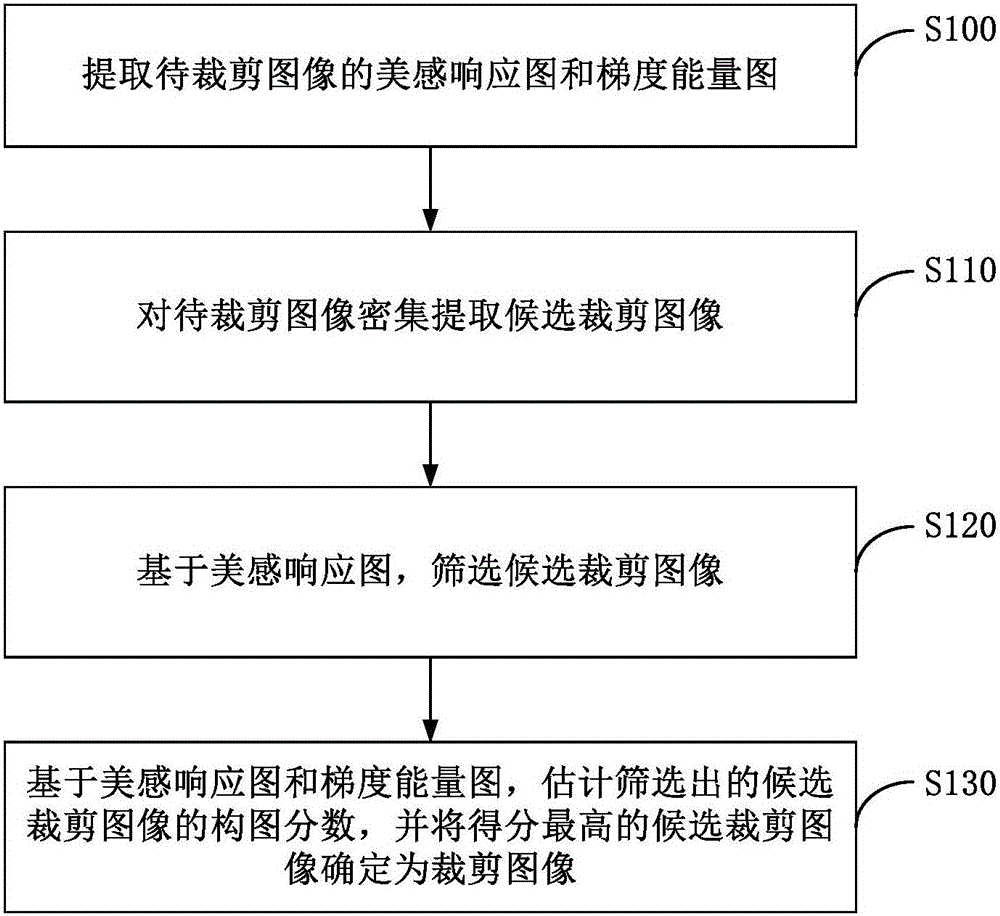
Image automatic cutting method
ActiveCN106650737ASolve the robustness problemPreserve high aesthetic qualityCharacter and pattern recognitionNeural learning methodsComputer visionEnergy analysis
The invention relates to an image automatic cutting method. The method comprises the following steps: extracting an aesthetic response graph and a gradient energy graph of an image to be cut; intensively extracting candidate cutting images from the image to be cut; based on the aesthetic response graph, screening the candidate cutting images; and based on the aesthetic response graph and the gradient energy graph, estimating composition fractions of screened candidate cutting images and determining that a candidate cutting image with the highest score is a cutting image. According to the scheme, an aesthetic influence area of a picture is studied by use of the aesthetic response graph, an aesthetic reservation portion is determined by use of the aesthetic response graph, high aesthetic quality of the cutting image is better reserved to be greatest extent, at the same time, a gradient distribution rule is analyzed by use of the gradient energy graph, and the composition fraction of the cutting image is evaluated based on the aesthetic response graph and the gradient energy graph. The image automatic cutting method provided by the embodiment of the invention makes up for the defect of image composition expression and solves the problem of how to improve the robustness and precision of image automatic cutting.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Course control system and method for unmanned surface vehicle
InactiveCN105775092AFast control dynamic responseSmall overshootSteering ruddersControllers with particular characteristicsUnmanned surface vehicleEngineering
The invention relates to the field of unmanned control methods, in particular to a course control system and method for an unmanned surface vehicle. The control system comprises an upper computer, a transmission station and a lower computer. The control method includes the set steps that an expected course is input in a human-computer interaction interface of an upper computer operating deck and transmitted to the lower computer through the transmission station; information is acquired and transmitted, wherein unmanned surface vehicle comprehensive information acquired by the lower computer is transmitted into the upper computer through the transmission station; and control is conducted, wherein the upper computer conducts calculation and processing according to the received unmanned surface vehicle comprehensive information, a rudder angle delta is output and transmitted to the lower computer, and the rudder direction is automatically changed through a course control device, so that the course of the unmanned surface vehicle is adjusted. The system and method have the beneficial effects that maneuverability is high, robustness is strong, a stepping motor and a bevel gear wheel are simultaneously adopted for driving the steering course control device, the control accuracy is higher, steering is more accurate, and the application prospect is good.
Owner:WUHAN NIWEI INTELLIGENT TECH CO LTD
Classification model evaluation method and device
PendingCN110363243ASolve the robustness problemCharacter and pattern recognitionPattern recognitionTest sample
The invention relates to a classification model evaluation method and device. The method comprises the steps of obtaining a to-be-tested sample, wherein the to-be-detected sample comprises a normal sample and a corresponding adversarial sample; inputting the to-be-tested sample into the classification model to obtain a prediction result output by the classification model, wherein the prediction result comprises a sample category and a corresponding prediction confidence coefficient; obtaining a confidence coefficient vector of a normal sample and a confidence coefficient vector of an adversarial sample; determining confidence similarity according to respective confidence vectors of the normal sample and the adversarial sample; and obtaining an evaluation result of the classification modelaccording to the confidence similarity. According to the scheme provided by the invention, the problem that the robustness of the classification model to the adversarial sample cannot be evaluated dueto the fact that the internal structure and related parameters cannot be known can be solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
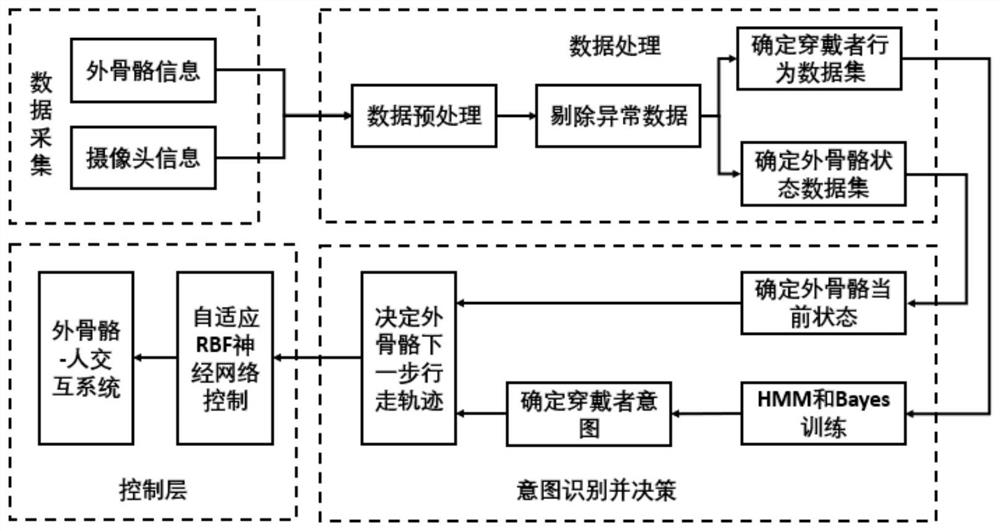
Neural network control system of exoskeleton robot based on intention recognition
InactiveCN111631923AAvoid inconvenienceEasy to controlProgramme-controlled manipulatorWalking aidsHuman bodyExoskeleton robot
The invention provides a neural network control system of an exoskeleton robot based on intention recognition. The system comprises: an intention classification module used for classifying intention of a wearer; an action and track planning module used for setting rehabilitation training actions of a patient, collecting lower limb electromyographic signals of a human body, collecting gait data when the human body walks, and planning a motion track in a joint space of the lower limb exoskeleton robot; and an exoskeleton state judgment module used for collecting state information of the exoskeleton and processing and analyzing the information to obtain current state information of the exoskeleton. According to the invention, the problem of system unknown items in calculation moment control based on model control is solved, and the real-time performance and robustness of control during conversion of different states are achieved. A wearer does not need to learn a complex exoskeleton operation method, the rehabilitation process is more suitable for the patient, man-machine interaction is enhanced, and the rehabilitation effect can be effectively improved.
Owner:INST OF ADVANCED TECH UNIV OF SCI & TECH OF CHINA
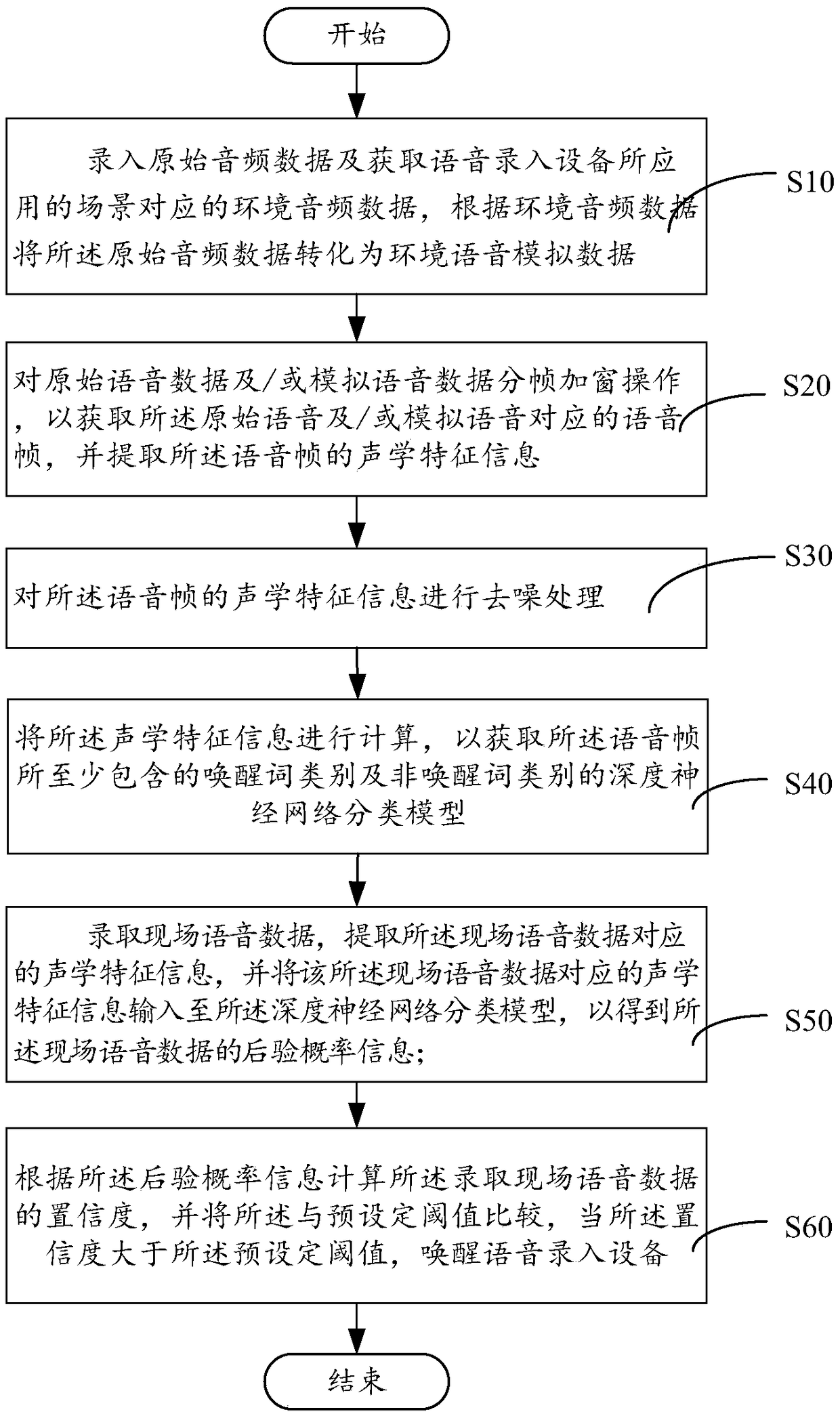
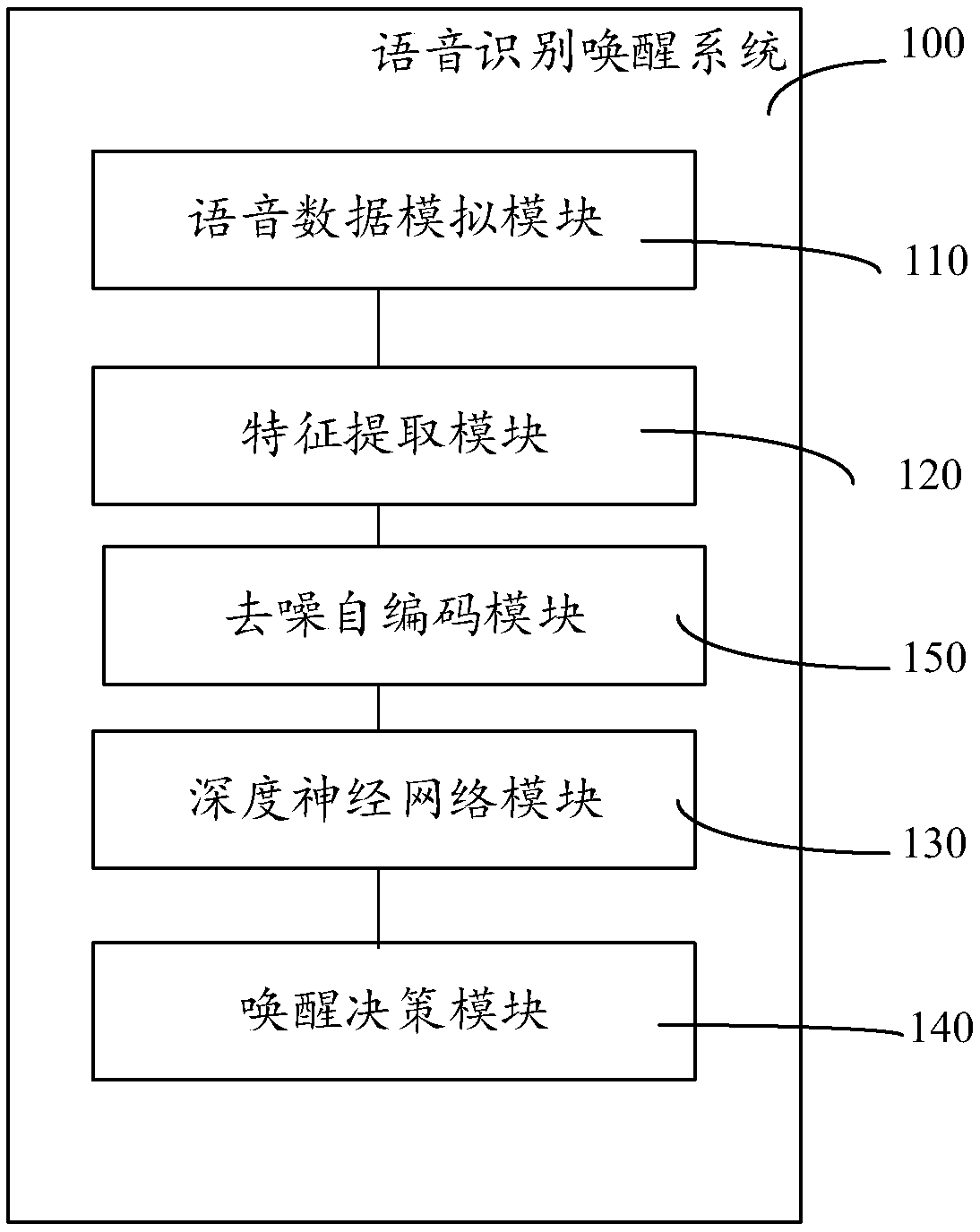
Voice waking-up method and system thereof
InactiveCN109036412AImprove adaptabilitySolve the robustness problemSpeech recognitionRate of speechVoice data
The invention relates to a voice waking-up method and a system thereof, wherein the method comprises the following steps of performing an enframing windowing operation on original voice data for acquiring a voice frame which corresponds with original voice, and extracting acoustic characteristic information of the voice frame; calculating the acoustic characteristic information for obtaining a deep neural network classification model; recording field voice data, extracting the acoustic characteristic information which corresponds with the field voice data, and inputting the acoustic characteristic information which corresponds with the field voice data into the deep neural network classification model, thereby obtaining posterior probability information; and comparing the posterior probability information with a preset threshold, and when the confidence is higher than the preset threshold, waking up voice recording equipment. The voice waking-up method and the system thereof have advantages of effectively improving waking-up performance in a noise scene, performing simulation such as voice speed, pitch and sound volume on the original data, and effectively improving adaptability ofthe waking-up system to different speakers.
Owner:苏州奇梦者科技有限公司
Method for three-dimensional reconstruction of straight-line optical flow field based on intelligent optimization algorithm
InactiveCN101697236ASolve the robustness problemTroubleshoot rebuild issuesGenetic modelsBiological neural network modelsMathematical modelPhysical model
The invention relates to a method for the three-dimensional reconstruction of a straight-line optical flow field based on an intelligent optimization algorithm, which is characterized by comprising the following steps of: shooting at least three continuous frames of images of an object in a scene by a fixed camera to form an image sequence, extracting the straight-line profile of the object in the scene and taking a straight line as a characteristic; under a perspective projection model, eliciting a relationship between the motion parameter of the straight-line profile of a moving rigid object in a 3D space and a two-dimensional straight-line optical field on a projection image of the moving rigid object, expressing the relationship by a straight-line optical flow equation group and constructing a physical model and a mathematical model of a three-dimensional reconstruction algorithm. The invention has the advantages of realizing the three-dimensional reconstruction and the moving target division of an object with a straight-line profile in a scene quickly, solving the problems of robustness of the three-dimensional reconstruction algorithm and reconstruction of a shielding boundary of the scene effectively and enhancing the accuracy of three-dimensional reconstruction effectively.
Owner:NANCHANG HANGKONG UNIVERSITY
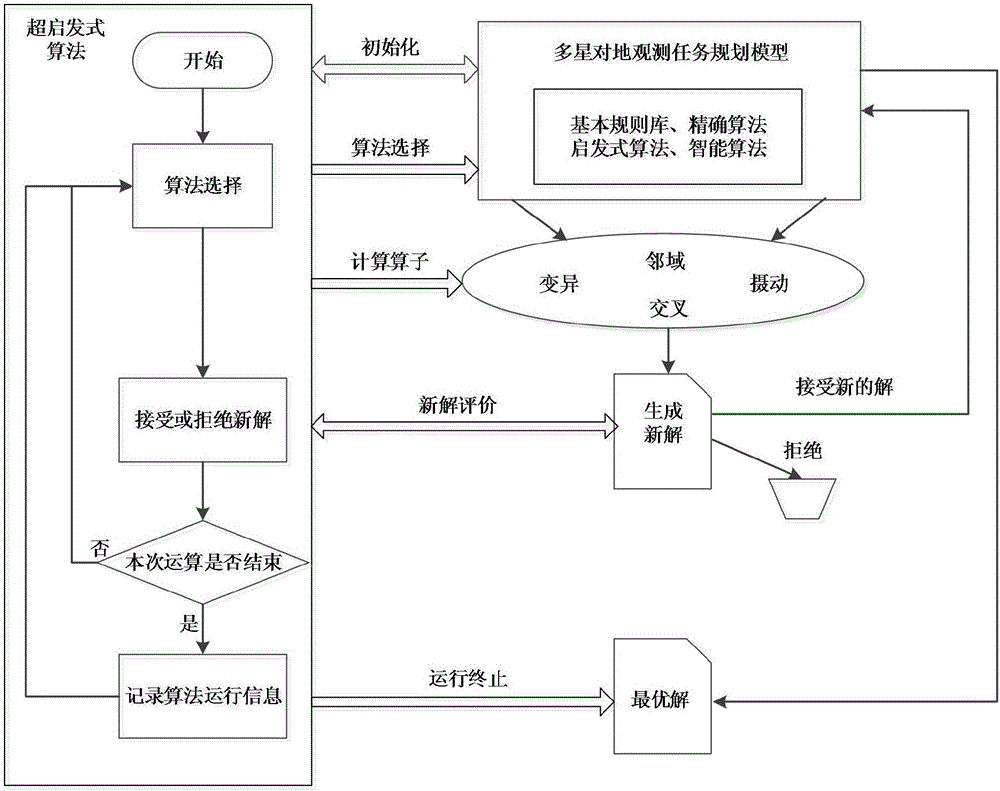
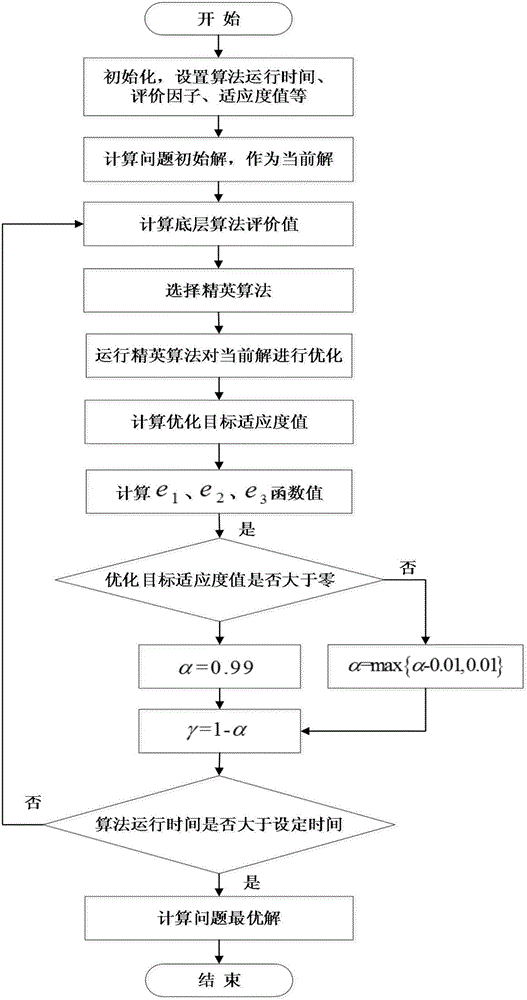
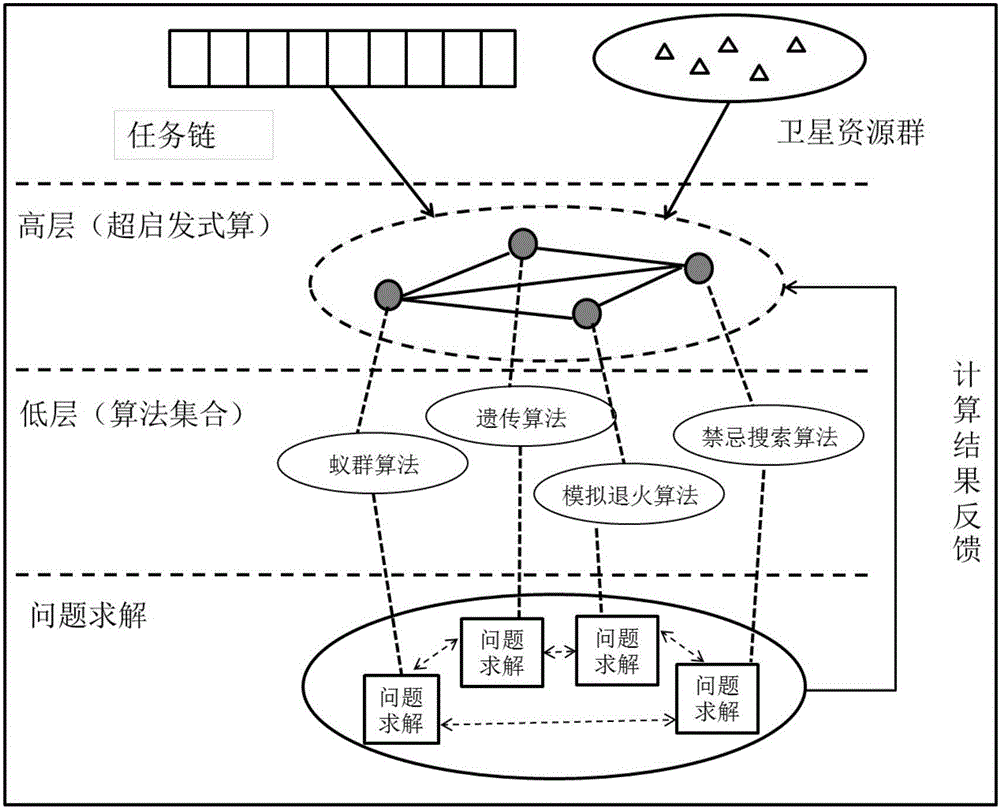
Hyper-heuristic algorithm-based multi-satellite earth observation task planning and scheduling method
ActiveCN106529826ASolve difficult-to-solve problems at different scalesImprove distribution efficiencyResourcesEarth observationAlgorithm
The present invention discloses a hyper-heuristic algorithm-based multi-satellite earth observation task planning and scheduling method. The method comprises the steps of 1, conducting the initialization setting; 2, generating the initial solution of a problem and adopting the initial solution as a current solution; 3, calculating the evaluation value of each algorithm in an underlying algorithm set; 4, selecting one algorithm maximum in evaluation value out of all algorithms in the underlying algorithm set as an elite algorithm; 5, applying the elite algorithm to optimize the current solution of the multi-satellite cooperative earth observation task planning problem so as to obtain a novel solution and the running time of the elite algorithm; 6, calculating the fitness value of an optimized target and adopting the new solution as a current solution; 7, modifying the e1(h1), e2 (hk, hi) function; 8, modifying an algorithm running efficacy evaluation factor and an algorithm selection evaluation factor; 9, judging whether the running time of the hyper-heuristic algorithm reaches a preset maximum running time or not; if not, jumping to the step 3; otherwise, adopting the current solution as the planning optimum solution of the multi-satellite synergistic earth observation task. The method is applied to examples of different scales for solving the multi-satellite task planning and scheduling problem. Based on the method, the better problem solving efficiency and the better problem solving effect are realized.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP +1
DWT-DCT (Discrete Wavelet Transform-Discrete Cosine Transform) and Logistic Map-based medical image robust watermarking method
InactiveCN102945543AStrong resistance to conventional attacksStrong ability to resist geometric attacksImage data processing detailsThird partyFeature vector
The invention relates to a DWT-DCT (Discrete Wavelet Transform-Discrete Cosine Transform) and Logistic Map-based medical image robust watermarking method, which belongs to the field of multimedia signal processing. The method comprises preprocessing of a watermark and embedding of the watermark, wherein the preprocessing of the watermark and embedding of the watermark comprise the following steps of: (1) obtaining an encryption matrix by using a Logistic Map; (2) obtaining an encrypted watermark; (3) performing DWT on an original image, performing DCT on an approximation sub-image and extracting the vector of a characteristic; (4) obtaining a corresponding two-valued logic sequence by using the characteristic vector and chaotically encrypted watermark, storing the two-valued sequence at a third party, and then extracting and reducing the watermark, wherein the extraction and the reduction of the watermark comprise the following steps of: (5) performing operation similar to the step (3) on an image to be tested to solve one characteristic vector; (6) extracting the encrypted watermark; (7) generating a two-valued encryption matrix by using the Logistic Map; and (8) solving the reduced watermark. According to the method, the secrecy of information of a patient can be protected.
Owner:HAINAN UNIVERSITY
Robust adaptive autopilot control algorithm for navigation simulator
InactiveCN101615000AImprove convergence rateSolve nonlinear problemsNeural learning methodsAdaptive controlLow speedWater model
The invention relates to a robust adaptive autopilot control algorithm for a navigation simulator. Aiming at various ship models in navigation simulator training, a nonlinear mathematic model for ship motion is obtained based on half theoretical calculation and half experimental result, and the nonlinear mathematic model considers the interferences of wind, wave, current, and the like and relates to a low-speed shallow-water model. The designed autopilot algorithm is based on a closed-loop gain shaping simple robust control algorithm and is a new ship autopilot robust adaptive control algorithm having robustness and adaptability by combining a neurotic network direct controlling training method. The robust adaptive autopilot control algorithm has adaptability by considering the robustness of a ship motion control algorithm as well as the complexity of ship navigation and solves the problem that the prior algorithm has either robustness or adaptability and can not have both.
Owner:DALIAN MARITIME UNIVERSITY
Time-domain blind separating method for in-line natural voice convolution mixing signal
InactiveCN1909064ASolve the robustness problemReduce complexityDigital technique networkSpeech recognitionTime domainHardware implementations
The related unsupervised learning algorithm to on-line treat speech signal for speech interactive front-end process comprises: with sufficient respect to time-domain relevance and non-stationary of natural speech signal, constructing a group of adaptive feed-forward filter networks to separate speech signal from multiple sources. This invention enhances speech signal, reduces algorithm complexity for hardware implementation, and has wide application.
Owner:FUDAN UNIV
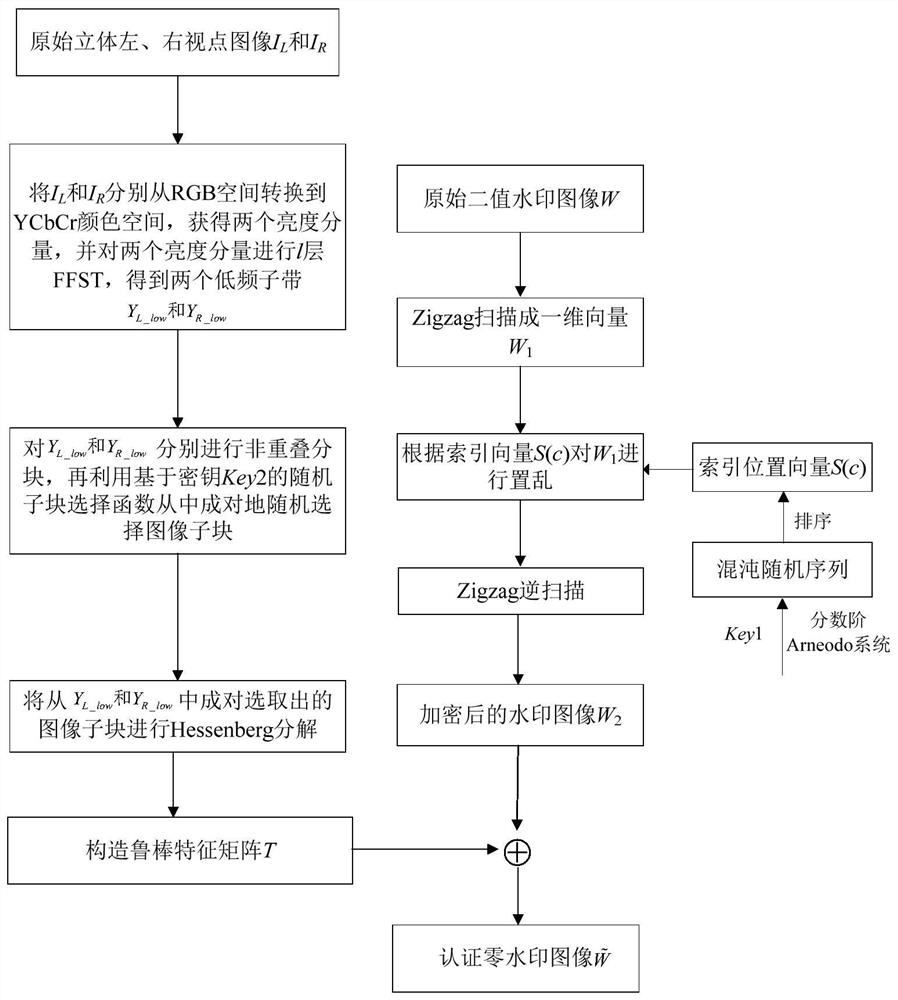
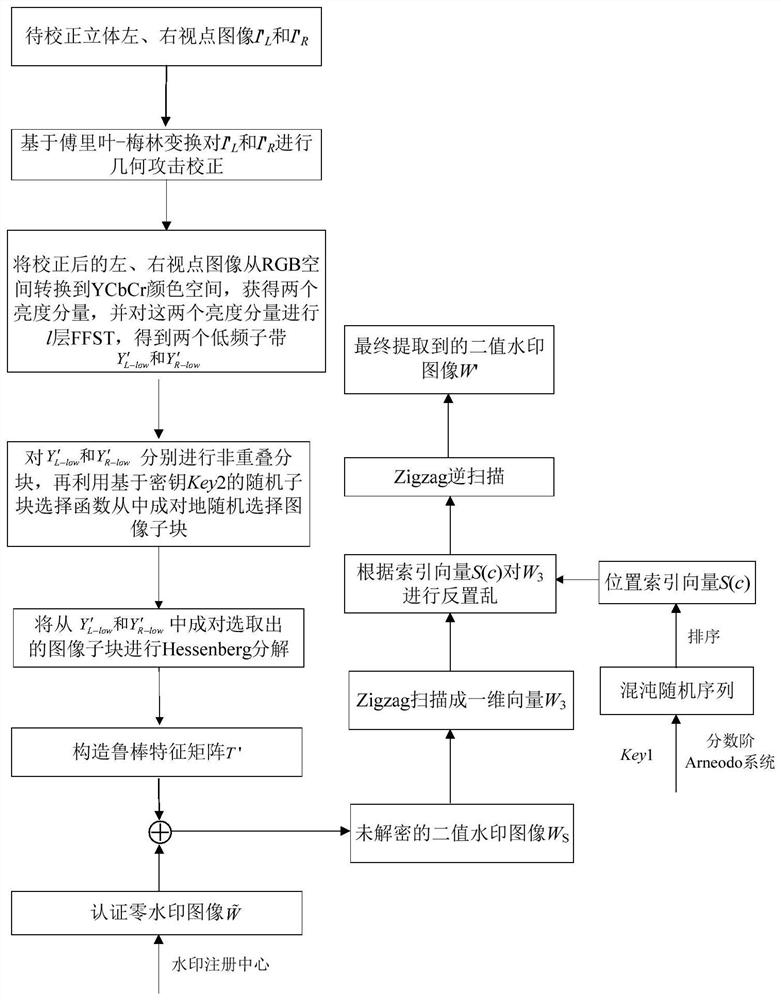
RST attack resistance stereo image zero watermark method based on FFST and Hessenberg decomposition
ActiveCN112381701AGood translation invarianceIncrease embedding capacityImage data processing detailsImaging processingAlgorithm
The invention relates to an RST attack resistance stereo image zero watermark method based on FFST and Hessenberg decomposition. The method comprises a zero watermark generation part and a zero watermark detection part. An authentication zero watermark of a three-dimensional image is constructed by utilizing the double-viewpoint characteristic of the three-dimensional image and utilizing the sizerelation between absolute values of elements at the upper left corners in respective coefficient sub-blocks after paired random image blocks are decomposed in low-frequency sub-bands after fast finiteshear wave transformation (FFST) of the left viewpoint image and the right viewpoint image, and the method is simple, novel and high in robustness. Meanwhile, a fractional order Arnodo chaotic systemis adopted to generate a random sequence, and encryption of an original binary watermark image is achieved. Before watermark extraction, geometric attack correction is carried out on a to-be-authenticated three-dimensional image by using an image matching method based on Fourier-Merlin transform. Experimental results show that the method provided by the invention has good robustness for resistingvarious common image processing attacks such as noise addition, filtering, JPEG compression, shearing, rotation, zooming, translation (RST) attacks and the like.
Owner:CIVIL AVIATION UNIV OF CHINA
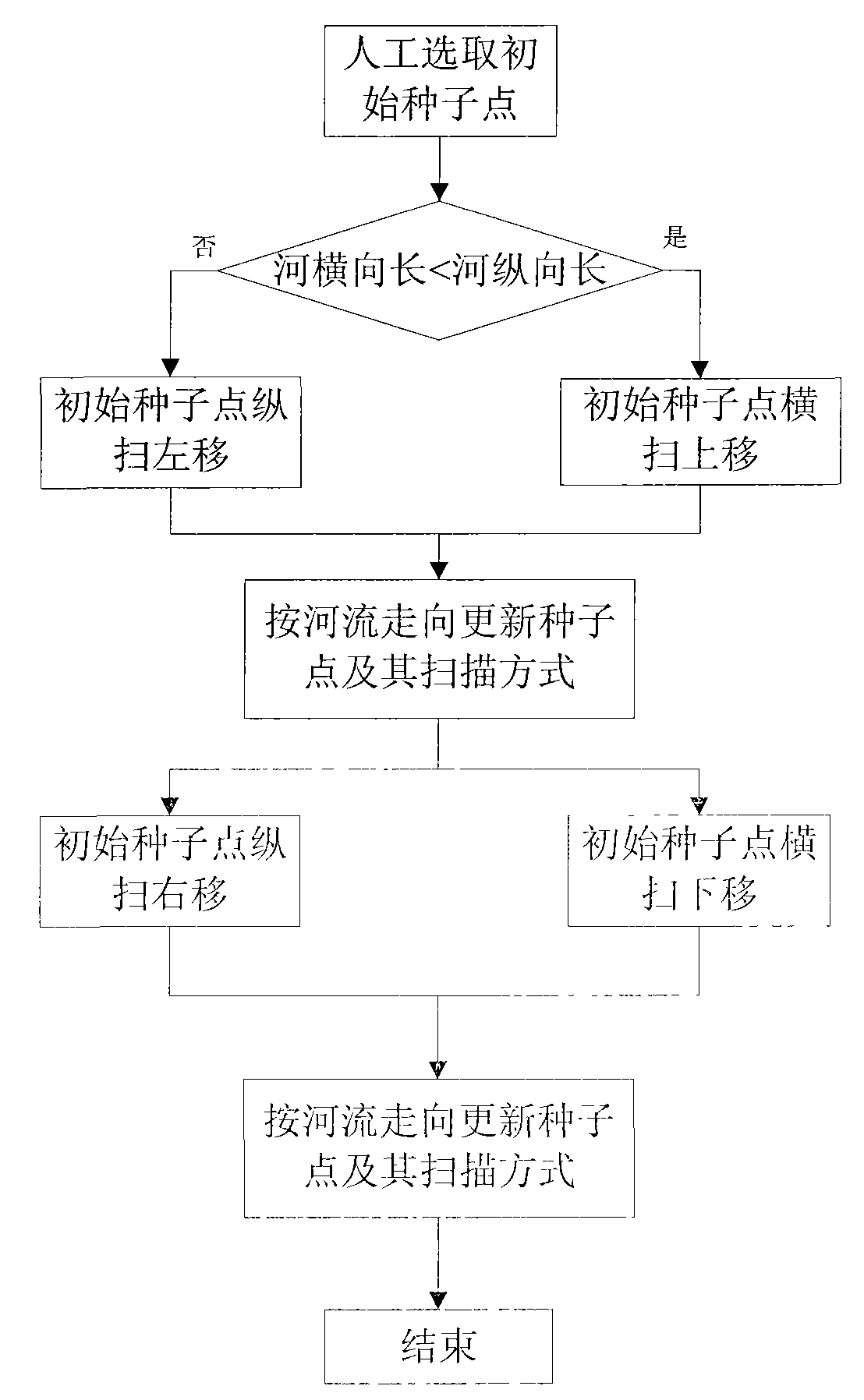
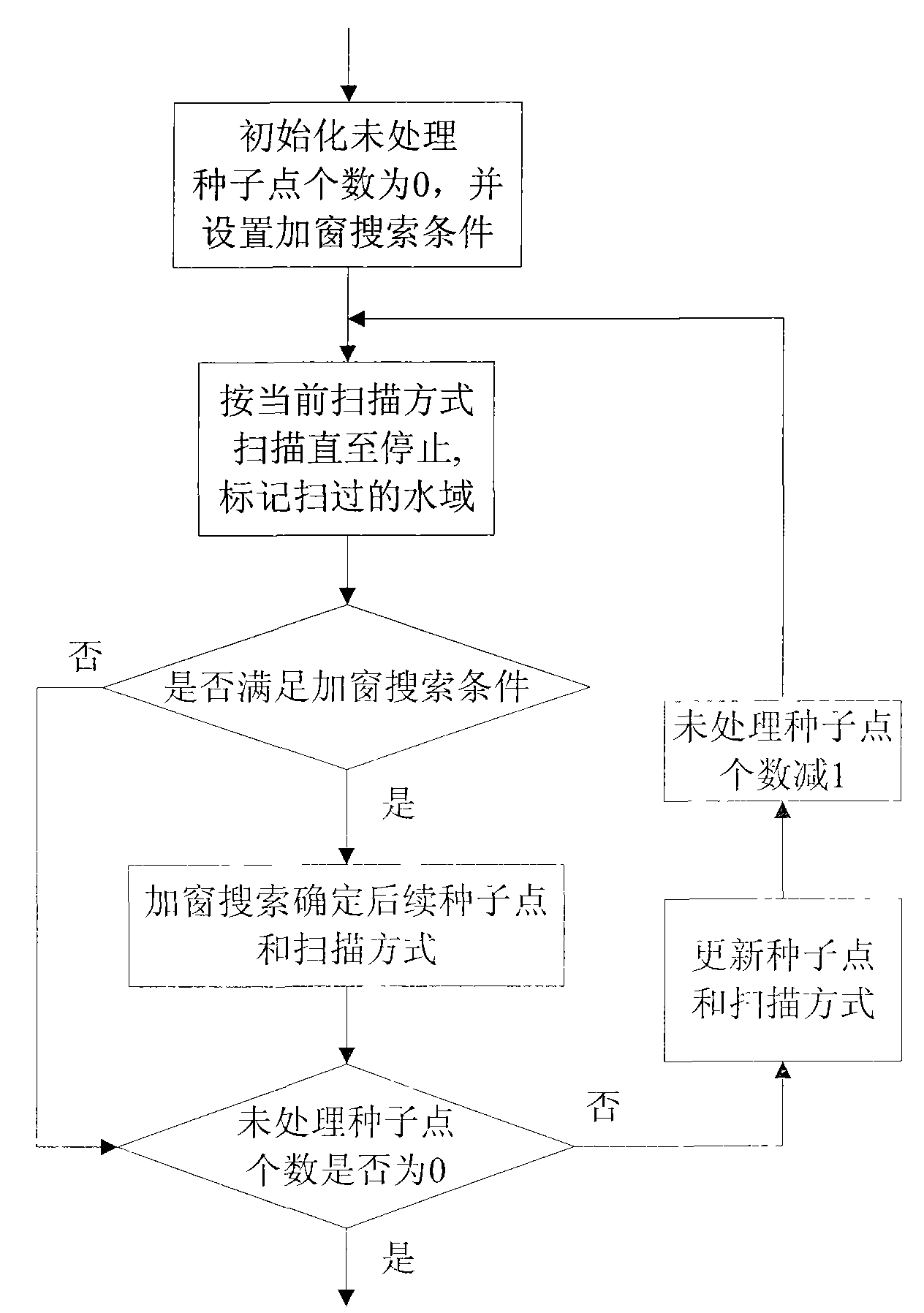
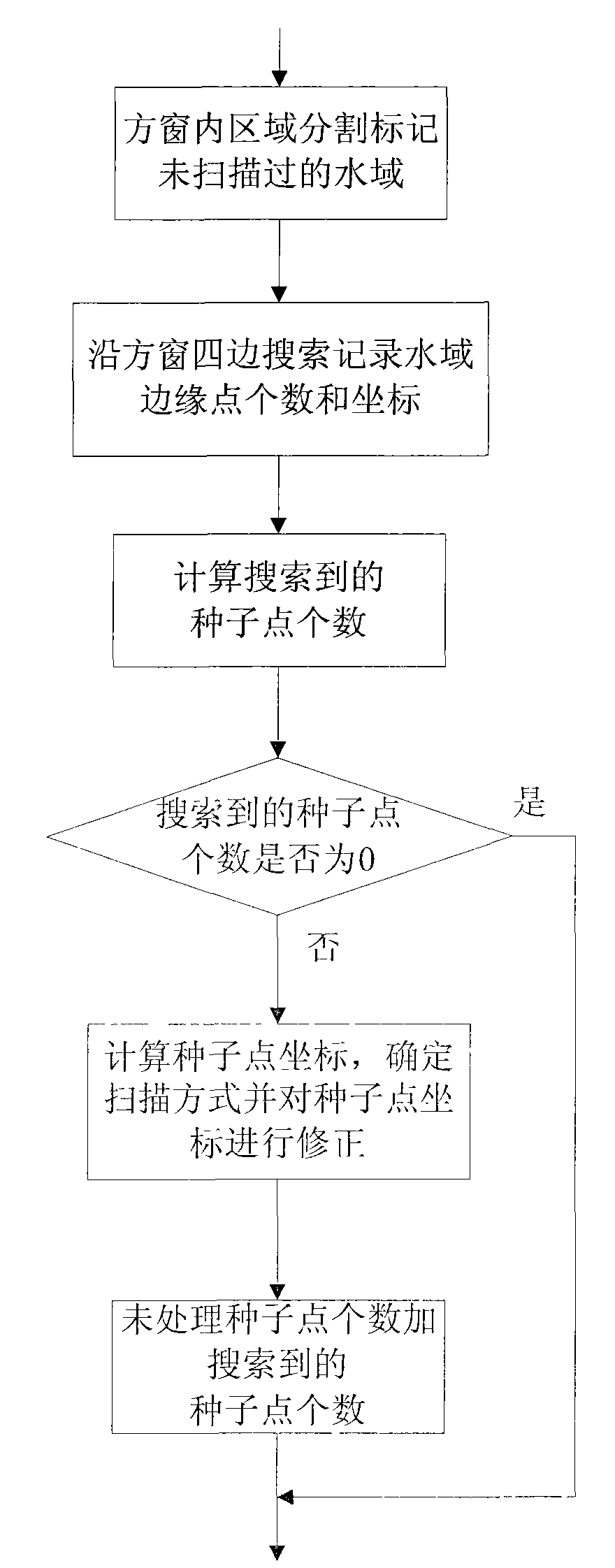
Method of quickly extracting rivers from remote sensing image
InactiveCN101576957AHigh speedReal-time processingCharacter and pattern recognitionElectromagnetic wave reradiationImage extractionLarge size
The invention discloses a method for quickly extracting rivers based on seed point scanning, and relates to the technical field of multispectral remote sensing image processing. The method mainly solves the problem that the prior method cannot extract rivers quickly from a large-size remote sensing image. The method comprises the following steps: carrying out manual selection of original seed points and automatically dividing a river into two parts according to the different positions of the original seed points; and scanning the two parts from the original seed points, constantly updating the seed points and a scanning mode thereof according to the flow direction of the river, and carrying out the scanning till the river scanning is completed. During the scanning, if a branch of the river appears or the flow direction changes or the river is cut off by a bridge, subsequent seed points and scanning mode are determined through windowed searching. The method can extract rivers quickly from an image with the size exceeding 50 million pixels, and has the advantage of high precision; therefore, the method can be used for quick extraction of river areas, bridge detection and water target detection from a multispectral remote sensing image.
Owner:XIDIAN UNIV
Channel information feedback method and device
ActiveCN107888264ASolve the robustness problemSolve efficiency problemsSpatial transmit diversityWireless communicationComputer scienceHigh transmission
The invention provides a channel information feedback method and device. The method comprises the following steps: determining a channel measurement resource set, wherein the channel measurement resource set comprises M channel measurement resources, and M is a positive integer; carrying out channel measurement on the M channel measurement resources; selecting N channel measurement resources fromthe M channel measurement resources according to a channel measurement result, wherein N is a positive integer and is smaller than or equal to M; and sending feedback on indication information of theselected N channel measurement resources. The method and device provided by the invention has the advantages that the problem in the relevant art that low system robustness and low transmission efficiency are caused because multiple corresponding routes cannot be obtained in the channel measurement resource selection technology, so that the multiple corresponding routes can be obtained during channel measurement resource selection, and the effects of higher system robustness and higher transmission efficiency are further achieved.
Owner:ZTE CORP
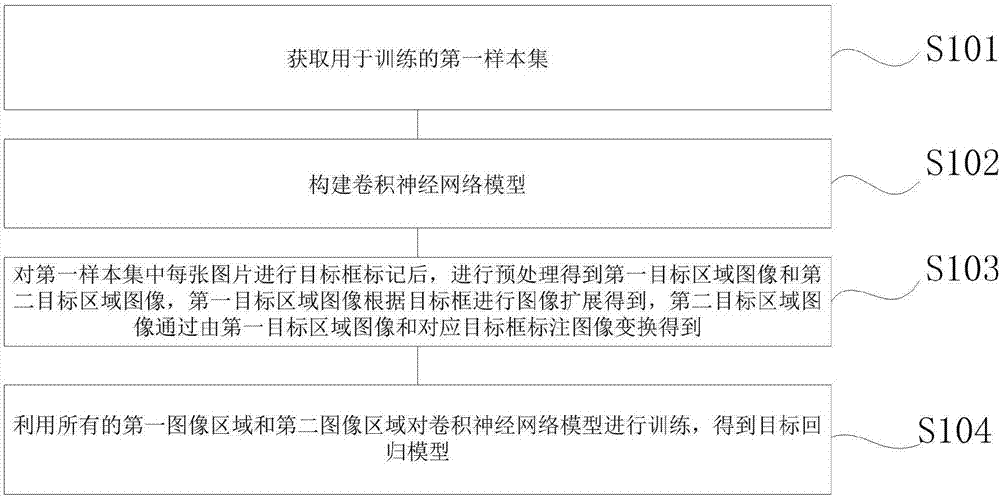
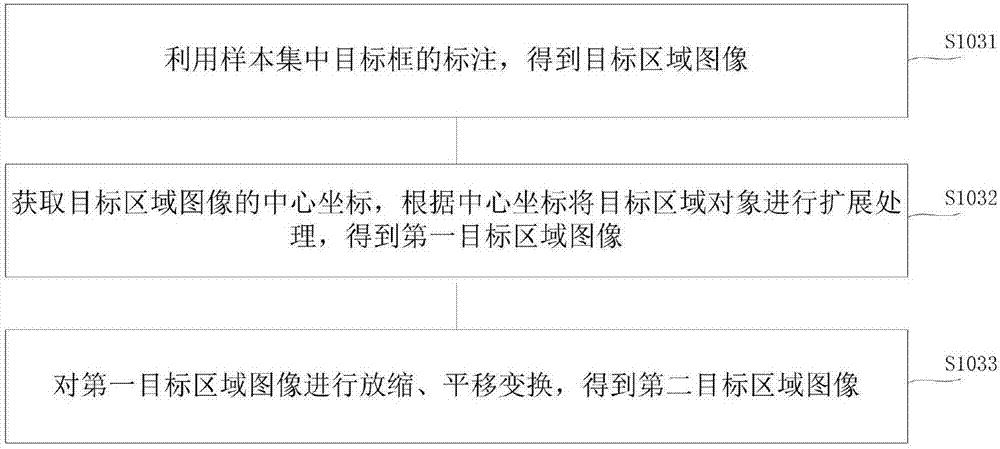
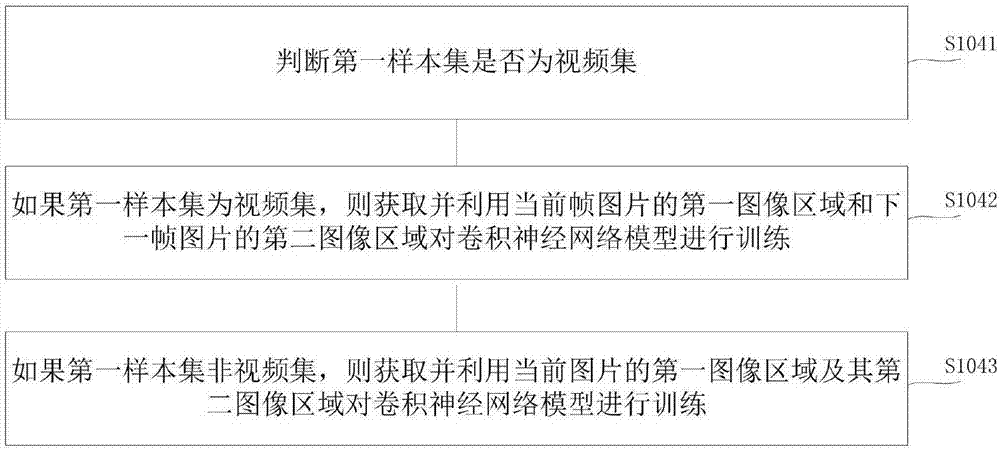
Construction method of image tracking classifier and face tracking method applying same
InactiveCN107273933ASolve the robustness problemSolve balance problemsImage enhancementImage analysisNetwork modelImage tracking
The present invention discloses a construction method of an image tracking classifier and a face tracking method applying the same. The construction method of the image tracking classifier comprises the following steps: obtaining a first sample set for training; constructing a convolution neural network model; after performing target frame marking of each image in the first sample set, performing preprocessing to obtain a first target area image and a second target area image, wherein the first target area image is obtained through image expansion according to a target frame, and the second target area image is obtained through transformation of the first target area image and a corresponding target frame marking image; and employing all the first image areas and all the second image areas to perform training of the convolution neural network model to obtain a target regression model. Through adoption of features extracted by the convolution neural network method based on deep learning, the construction method of the image tracking classifier and the face tracking method applying the same effectively solve the problem of balance of robustness and accuracy, have higher robustness in the rapid movement and illumination fuzzy changing, are small in calculation and improve the tracking speed.
Owner:北京飞搜科技有限公司
Fingerprint recognition method based on SIFT
InactiveCN104933407ASolve the robustness problemCharacter and pattern recognitionPattern recognitionScale space
The invention discloses a fingerprint recognition method based on SIFT. The method includes following steps: extracting the main characteristic component of fingerprints in a large sample fingerprint database based on SIFT, producing hash values of the main characteristic component via MD5 harsh, and generating a hash table of all the fingerprints in the database; performing the same processing of the fingerprints logged during identity verification, and enabling the fingerprints to generate an MD5 hash value; and comparing the hash value during verification with the hash table, and searching the fingerprint matched with the hash value in the large sample fingerprint database. According to the fingerprint recognition method based on SIFT, local characteristics in fingerprint images are detected and described via SIFT, key characteristic points are searched in the scale space, descriptors of the key characteristic points are extracted, the main characteristic component is extracted via the descriptors of the fingerprints, and the problem of robustness of fingerprint characteristic extraction caused by factors such as finger deformation and rotation etc. during fingerprint characteristic extraction is solved to some extent.
Owner:成都佳发安泰教育科技股份有限公司
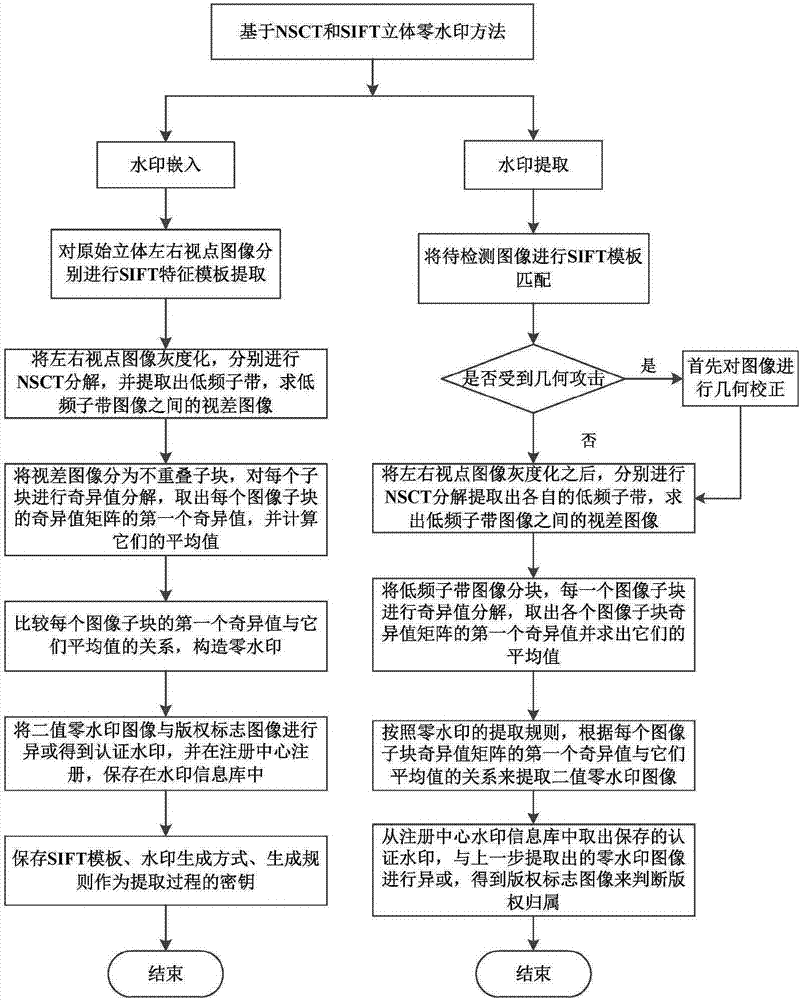
Stereo image zero-watermarking method based on NSCT and SIFT
ActiveCN107507122AImprove robustnessIncrease capacityImage data processing detailsStereo imageSingular value decomposition
The invention provides a stereo image zero-watermarking method based on NSCT and SIFT, and belongs to the technical field of image encryption and image processing. The stereo image zero-watermarking method based on NSCT and SIFT includes the steps: extracting the low frequency sub-band images of the left and right view point image NSCT transformation domains of a stereo image, taking the parallax image between the low frequency sub-band images as the carrier for extracting the watermarking, performing singular value decomposition on the carrier image, making rules for zero-watermarking extracting, performing XOR on the extracted two-value zero-watermarking image and the copyright sign watermarking image to obtain an authorized zero-watermarking image, and enabling the stereo image to be under protection of the watermarking technique after saving the zero-watermarking image at a registration center. The stereo image zero-watermarking method based on NSCT and SIFT can preferably resist conventional attack, such as various noises, filtering and compression, and especially improves the capability of resisting geometrical attack, so that zero-watermarking embedding cannot change the original image and the quality of image can be guaranteed. Besides, during the watermarking extracting process, the original image is not demanded, so that the stereo image zero-watermarking method based on NSCT and SIFT provides convenience for practical application and can effectively protect the copyright of the stereo image.
Owner:JILIN UNIV
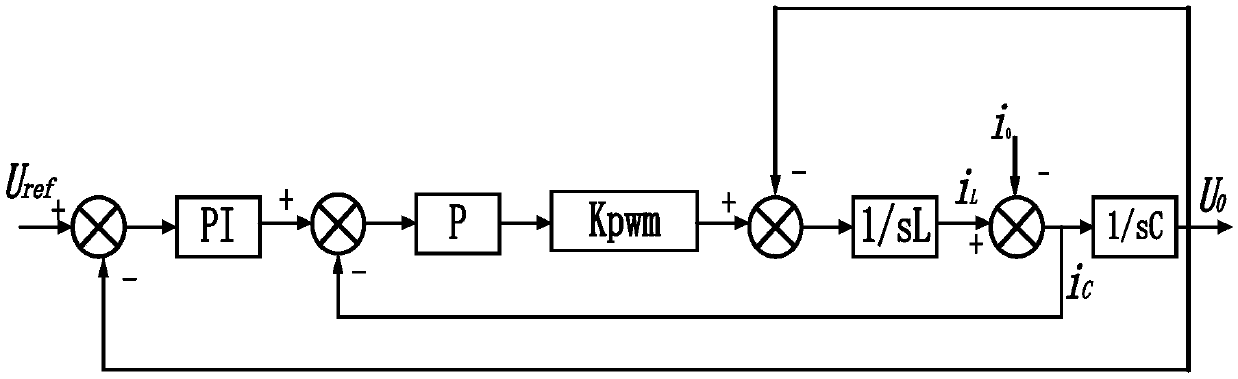
Inverter parallel control method based on improved droop control
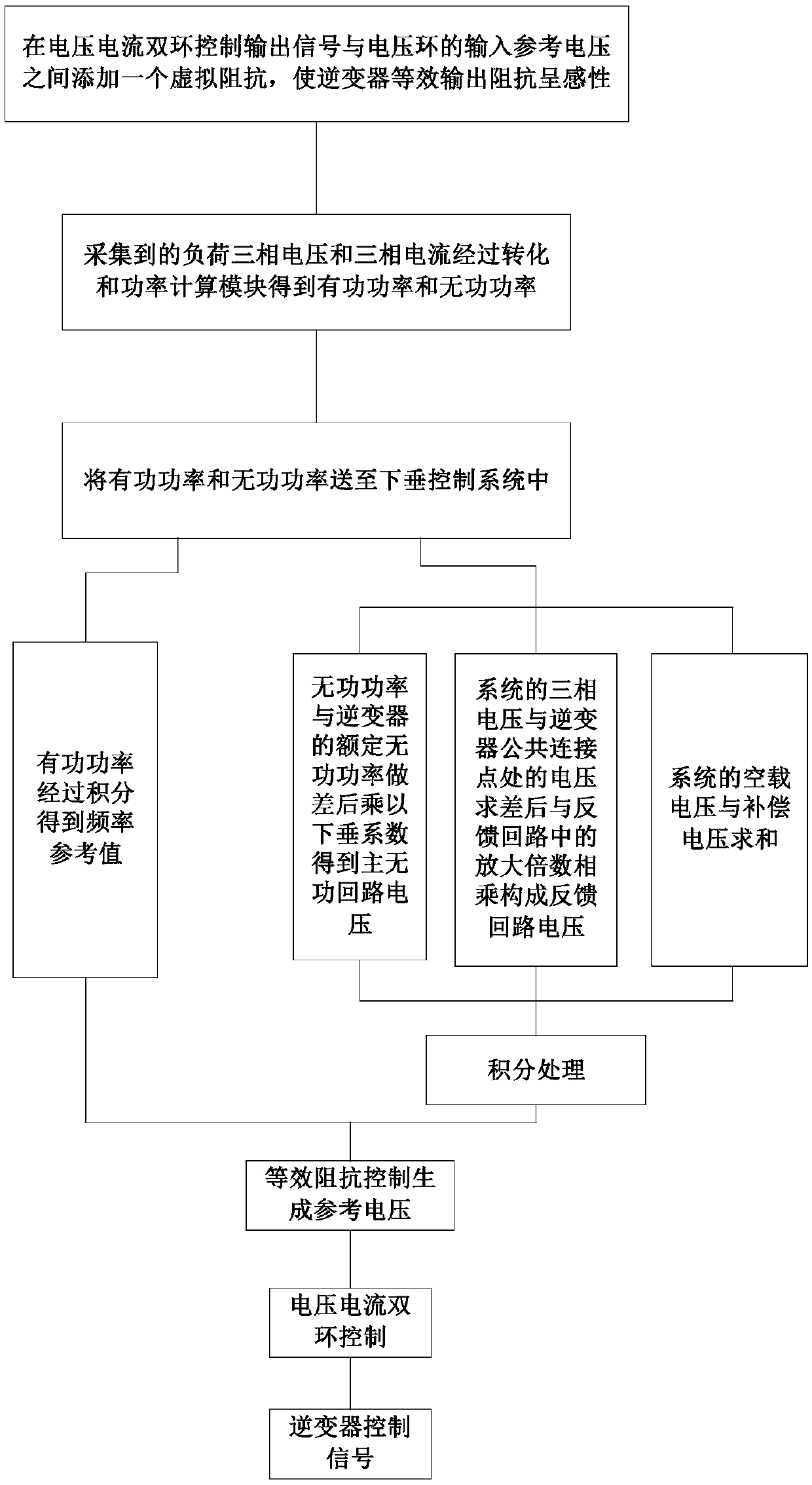
ActiveCN109256808AAvoid stabilitySolve the robustness problemSingle network parallel feeding arrangementsMicrogridInterference resistance
The invention relates to an inverter parallel control method based on improved droop control, belonging to the field of microgrid inverter control. The invention solves the problems of weak anti-interference ability to the system and low system power distribution precision in the prior control method. In the reactive power loop of the sag control system of the present invention, the main reactivepower loop voltage is obtained by multiplying the difference between the reactive power Q and the rated reactive power Q0 of the inverter by the dropping coefficient kq, the three-phase voltage V0 ofthe system and the voltage E* at the common connection point of the inverter are multiplied by the amplification multiple Ke in the feedback loop to form the feedback loop voltage, After the no-load voltage U0 and compensation voltage Ucmp of the system is summed up, the voltage reference value is obtained by integrating the difference between the no-load voltage U0 and compensation voltage Ucmp and the voltage of the main reactive power loop and the feedback loop. The invention improves the anti-interference ability of the system, restrains the circulating current of the system, and improvesthe accuracy of the power distribution of the system.
Owner:HARBIN UNIV OF SCI & TECH
Robust watermarking method for medical images on basis of Arnold scrambling transformation and DWT (discrete wavelet transform)-DFT (discrete Fourier transform)
InactiveCN102938133ASolve the quickness problemImplement secondary encryptionImage data processing detailsThird partyFeature vector
The invention discloses a robust watermarking technology for medical images on the basis of Arnold scrambling transformation and DWT (discrete wavelet transform)-DFT (discrete Fourier transform), and belongs to the field of multimedia signal processing. The robust watermarking technology includes embedding watermarks and then extracting the watermarks, and particularly includes steps of (1), performing Arnold transformation for watermarks to be embedded; (2), performing DWT for a medical image, performing DFT for approximation sub-images of the medical image, and extracting vectors of a feature; (3), generating a binary logic sequence via a Hash function by the vectors of the feature and the preprocessed watermarks so as to complete the process for embedding the watermarks; (4), performing DWT for a medical image to be measured, performing DFT for approximation sub-images of the medical image to be measured and extracting vectors of a feature; (5), extracting watermarks by the aid of the Hash function and a binary logic sequence stored in a third party; and (6), obtaining the original watermarks via Arnold inverse transformation so as to complete the process for extracting the watermarks. The robot watermarking technology has an important significance in protecting information of patients during remote medical treatment.
Owner:HAINAN UNIVERSITY
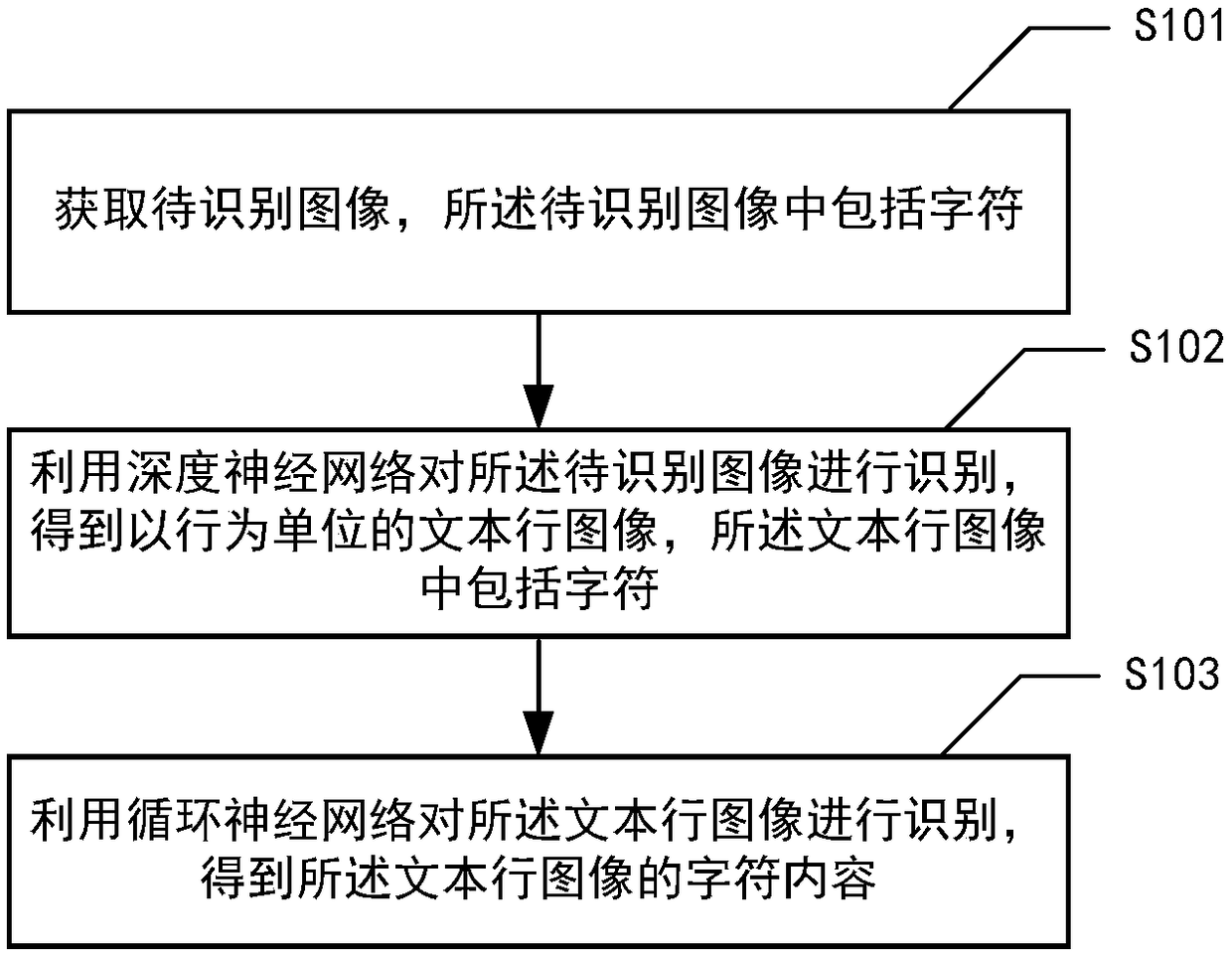
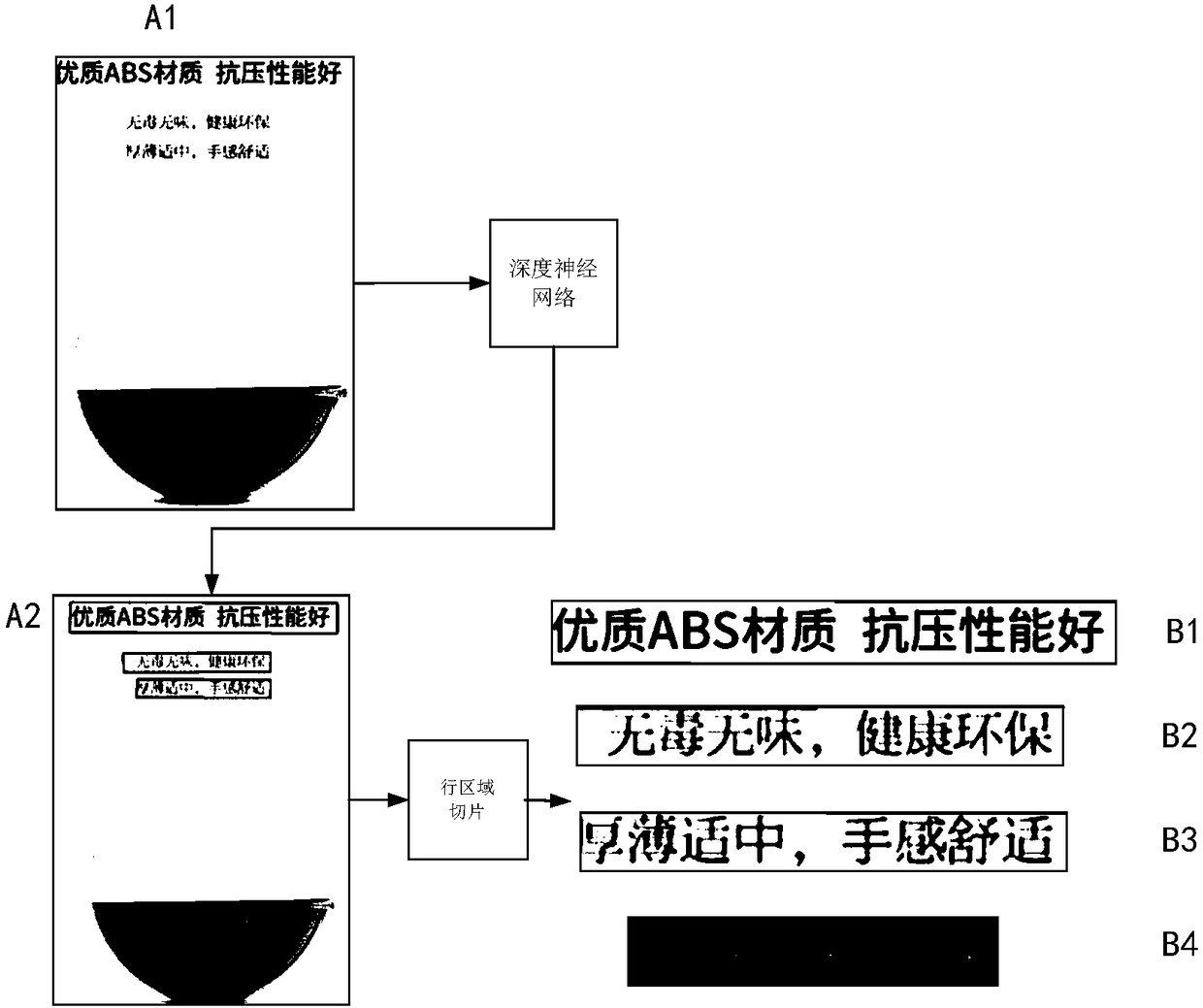
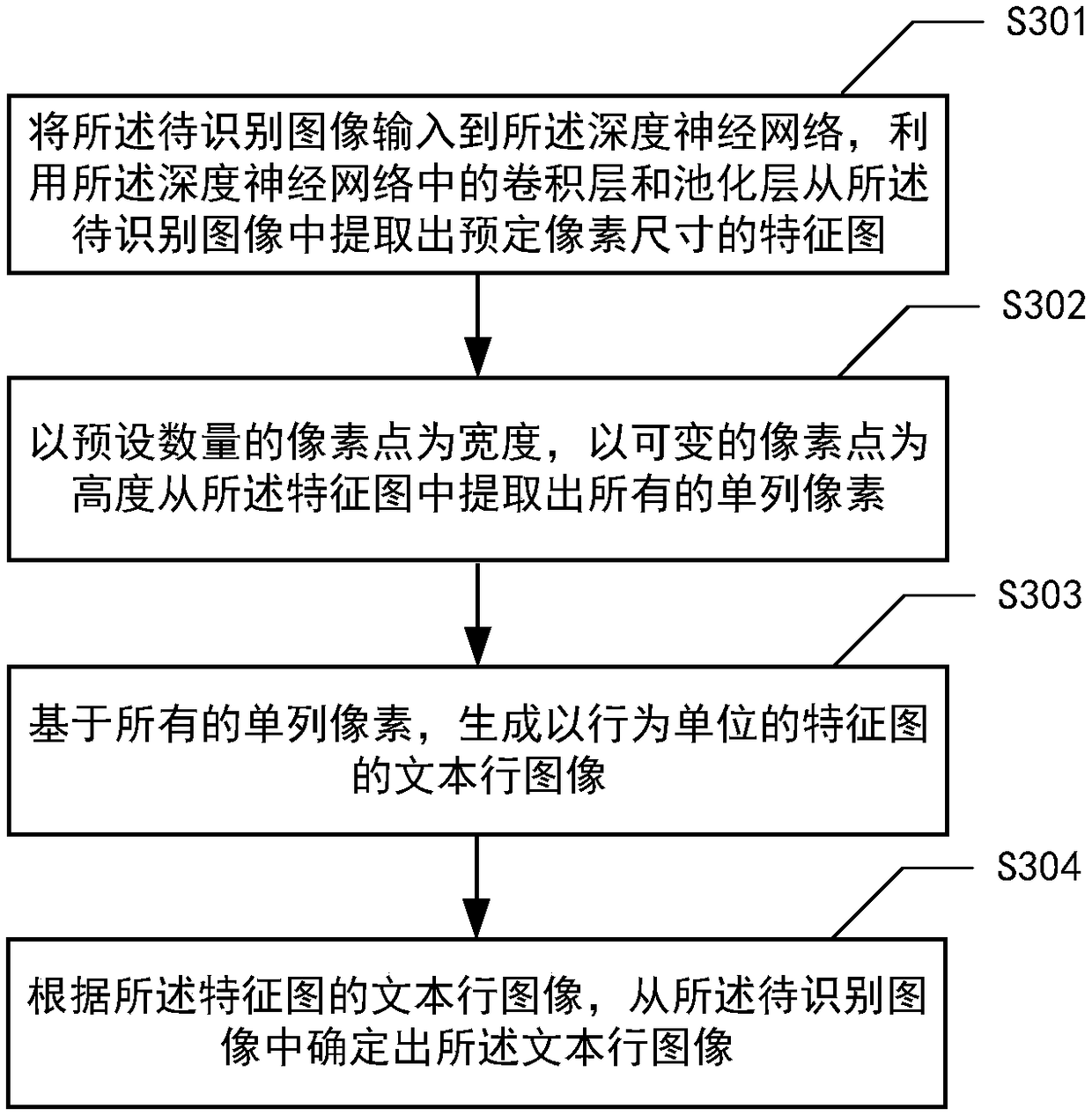
Method, device and medium for identifying characters in image
ActiveCN108596168ASolve the robustness problemResolve accuracyNeural architecturesCharacter recognitionPattern recognitionComputer vision
The invention provides a method for identifying characters in an image. The method comprises the following steps: acquiring an image to be identified, wherein the image to be identified comprises thecharacters; identifying the image to be identified by using a deep neural network to obtain a text line image taking a line as a unit, wherein the text line image comprises the characters; and identifying the text line image by using a recurrent neural network to obtain character contents of the text line image. The invention further provides a device and medium for identifying the characters in the image.
Owner:JINGDONG TECH HLDG CO LTD
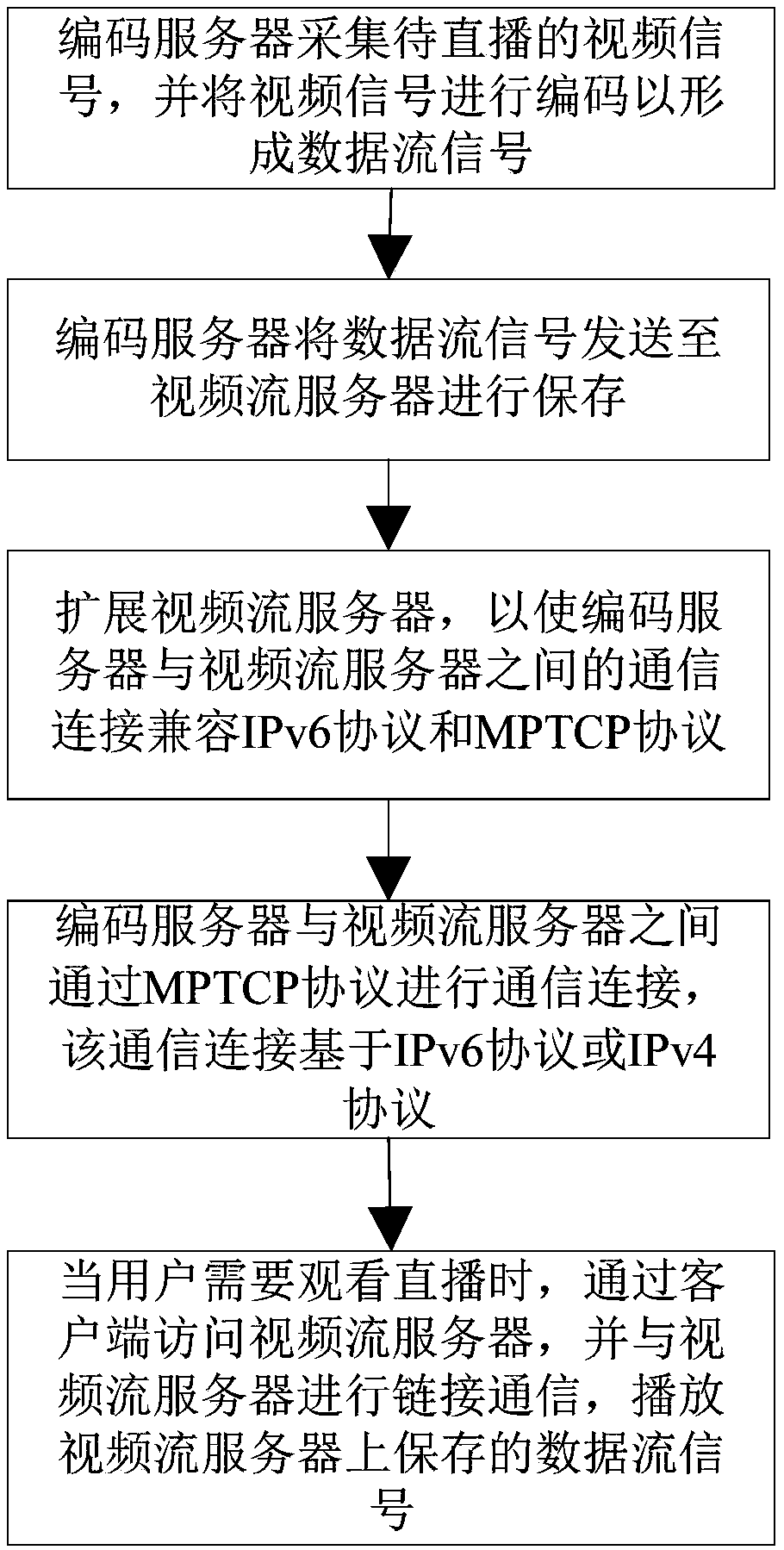
Network live broadcast method and system based on multipath transmission
ActiveCN109257620AFully smooth switchingSolve the load problemDigital video signal modificationTransmissionUser needsData stream
The invention discloses a network live broadcast method based on multipath transmission and a system thereof, which relate to the network technical field. The network live broadcasting method comprises the following steps: an encoding server collects a video signal to be live broadcasted and encodes the video signal to form a data stream signal. The encoding server sends the data stream signal tothe video stream server for storing. Extending the video stream server to make the communication connection between the encoding server and the video stream server compatible with the IPv6 protocol and the MPTCP protocol; When the user needs to watch the live broadcast, the user accesses the video stream server through the client, and performs link communication with the video stream server to play the data stream signal stored on the video stream server. The invention carries out parallel data transmission of a plurality of network paths through a link between an encoding server, a video stream server and a client. It solves the problem of load balancing and robustness of traditional single-path transmission with low cost.
Owner:HAINAN UNIVERSITY
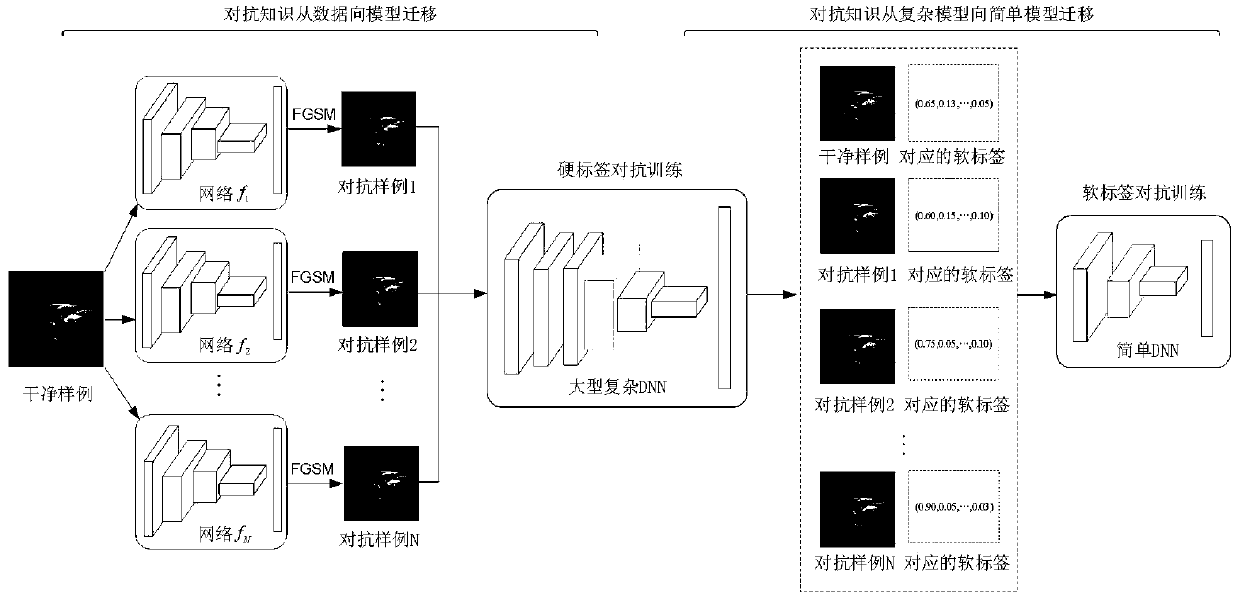
Adversarial example defense method based on two-stage adversarial knowledge migration
PendingCN111047054ASolve the robustness problemAlgorithm convergence is goodKernel methodsNeural architecturesNetwork onEngineering
The invention belongs to the technical field of artificial intelligence safety, and discloses an adversarial example defense method based on two-stage adversarial knowledge migration. The method comprises the steps: firstly migrating adversarial knowledge from data to a large-scale complex DNN (deep neural network) through heterogeneous multi-source adversarial training, and completing the first-stage adversarial knowledge migration; then, a soft label of an adversarial sample is adopted, an adversarial extraction technology is provided, adversarial knowledge is migrated from a complex DNN toa simple DNN, and adversarial knowledge migration in the second stage is achieved. According to the two-stage adversarial knowledge migration method provided by the invention, the simple neural network on the edge equipment can obtain robustness close to that of a large complex network, and the problem of robustness of the simple network which cannot be solved by pure adversarial training is better solved. The adversarial extraction proposed by the invention has good algorithm convergence, can stably improve the performance and robustness of a simple network model and accelerate convergence, and well solves the problem of instability of the model performance and robustness in integrated adversarial training.
Owner:ZHEJIANG UNIVERSITY OF SCIENCE AND TECHNOLOGY +1
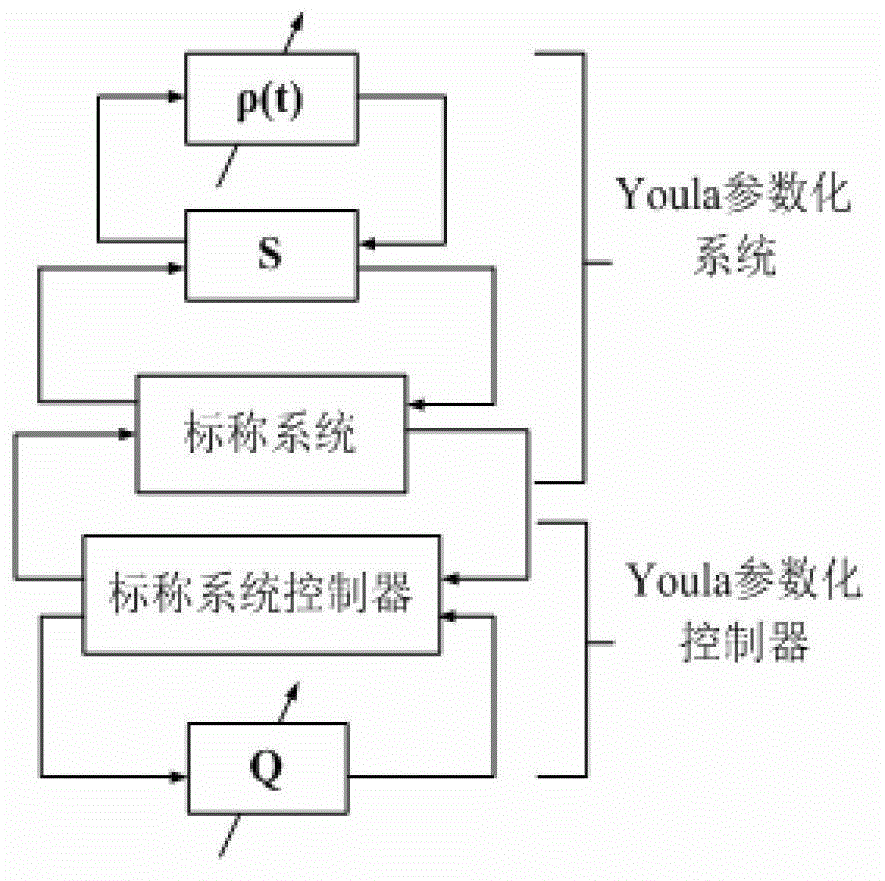
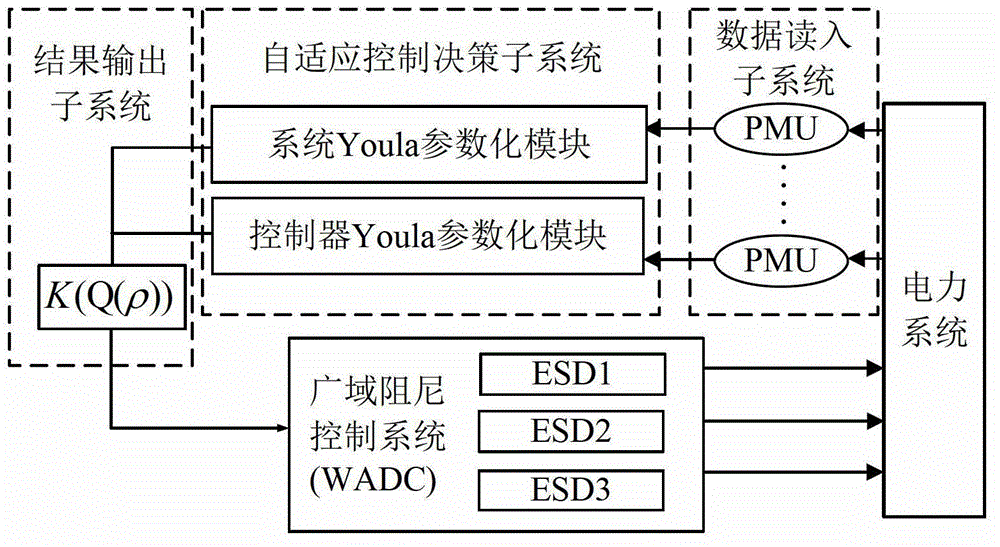
Damping adaptive control system based on Youla parameterization and control method
ActiveCN103337865AAddress effectivenessSolve the robustness problemPower oscillations reduction/preventionPower system stability controlControl system
The invention discloses a damping adaptive control system based on Youla parameterization and a control method. The damping adaptive control system comprises a data read-in subsystem, a self-adaptive control decision subsystem and a result output subsystem which are sequentially connected, wherein the self-adaptive control decision subsystem comprises a system Youla parameterization module and a controller Youla parameterization module, the system Youla parameterization module determines an operation state of a dynamic electric power system through updating system Youla parameters, the controller Youla parameterization module realizes online update of Youla parameters of a controller according to the updated system Youla parameters, and the self-adaptive controller which is suitable for the operation state of a present electric power system is acquired. The damping adaptive control system solves problems of lack of validity and robustness existing in a wide area damping control system in the prior art under an unknown disturbance condition.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
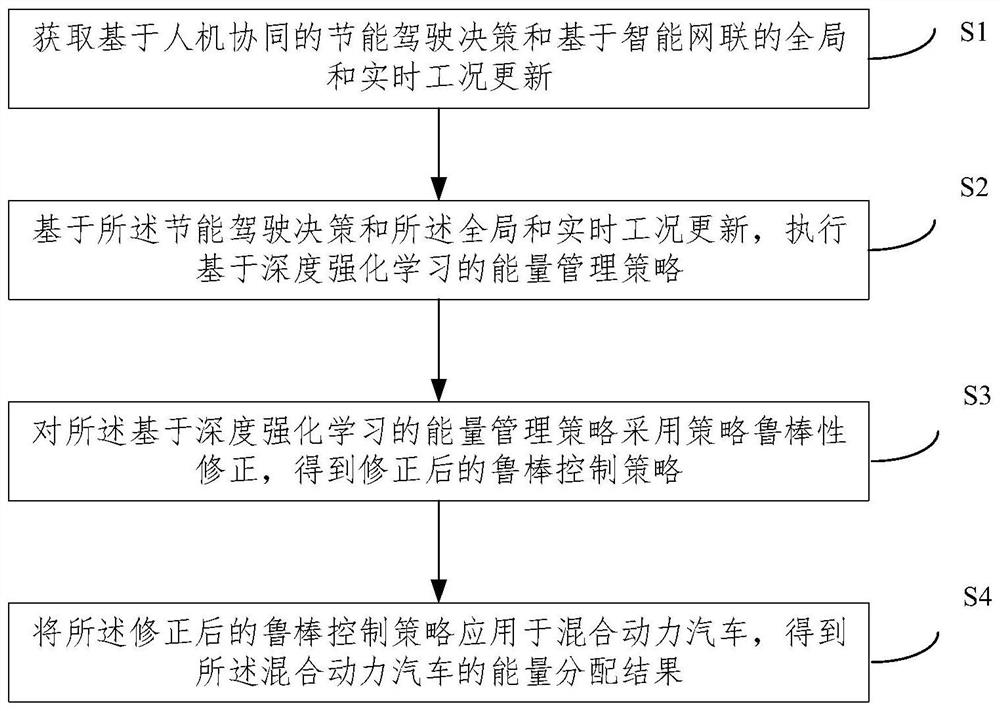
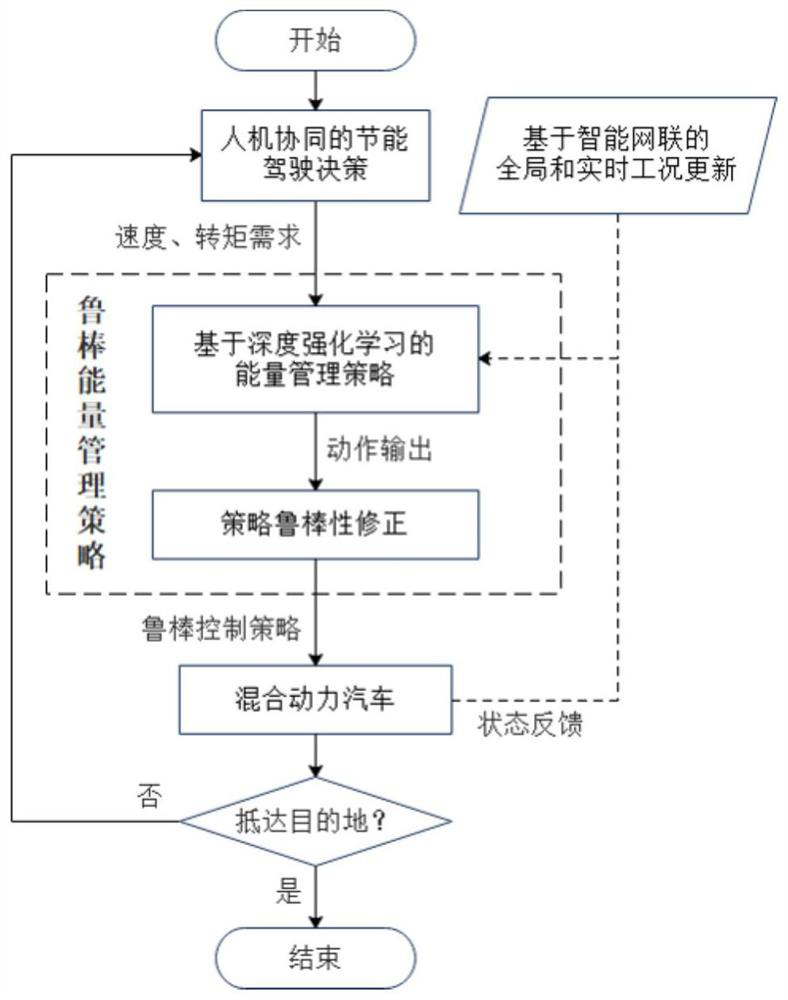
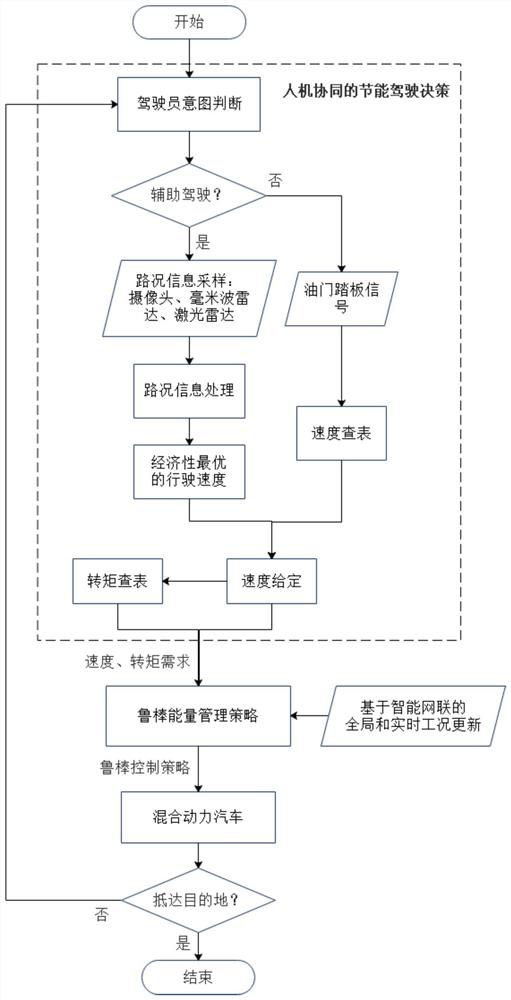
Robust energy management method and system for intelligent networked hybrid electric vehicle
ActiveCN112498334AGood energy saving effectSolve the robustness problemHybrid vehiclesIntelligent NetworkControl engineering
The invention provides a robust energy management method and system for an intelligent networked hybrid electric vehicle. The method comprises the steps of obtaining an energy-saving driving decisionbased on man-machine cooperation and global and real-time working condition updating based on intelligent network connection; executing an energy management strategy based on deep reinforcement learning based on the energy-saving driving decision and the global and real-time working condition update; performing strategy robustness correction on the energy management strategy based on deep reinforcement learning to obtain a corrected robustness control strategy; and applying the corrected robust control strategy to the hybrid electric vehicle to obtain an energy distribution result of the hybrid electric vehicle. According to the robust energy management method for the intelligent networked hybrid electric vehicle, the robustness problem of the deep reinforcement learning energy managementstrategy is effectively solved, the energy-saving effect of the hybrid electric vehicle in the networked environment is improved, and the method has good engineering application value.
Owner:TSINGHUA UNIV
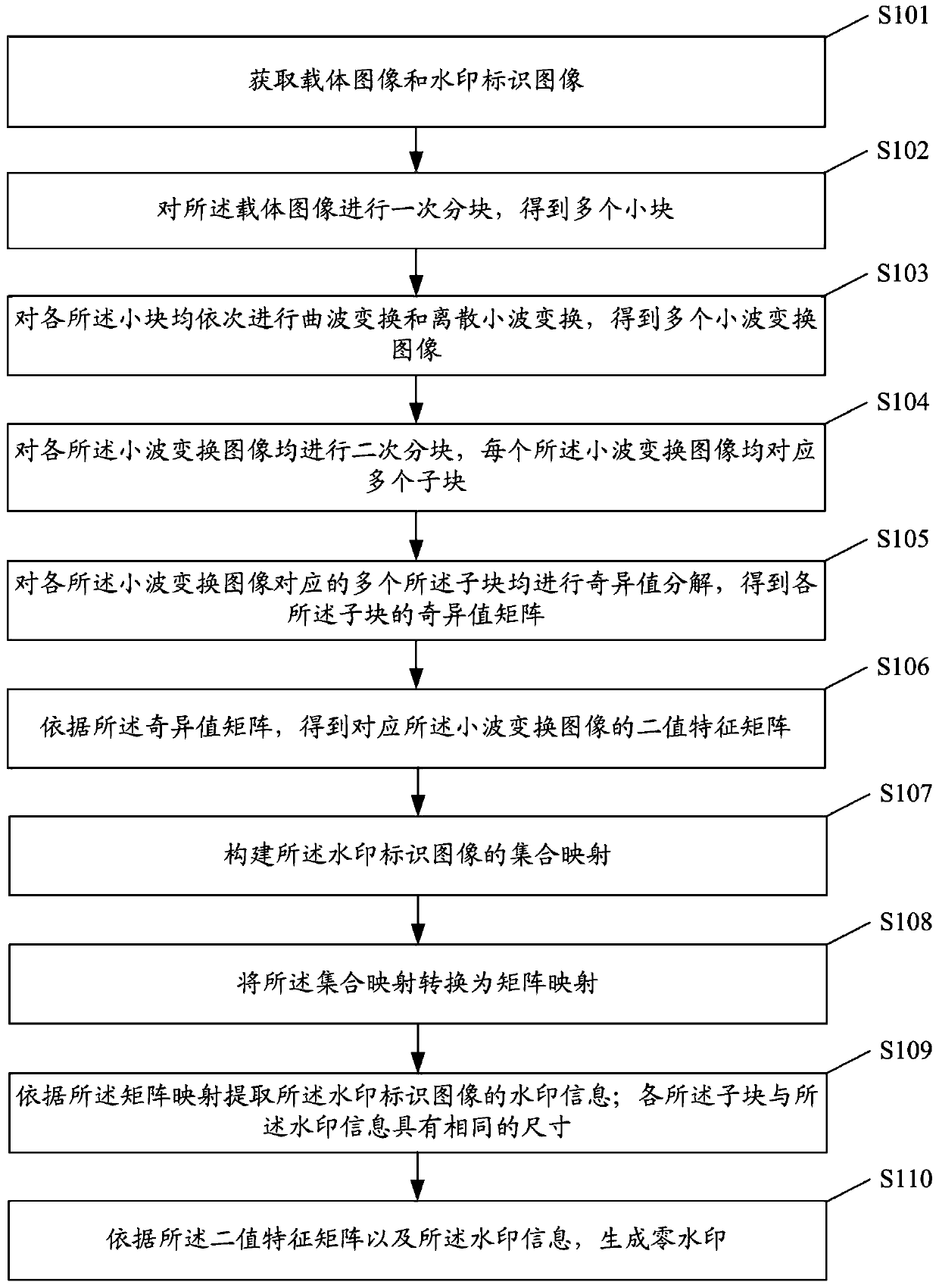
Zero watermark generation method and system and zero watermark extraction method and system
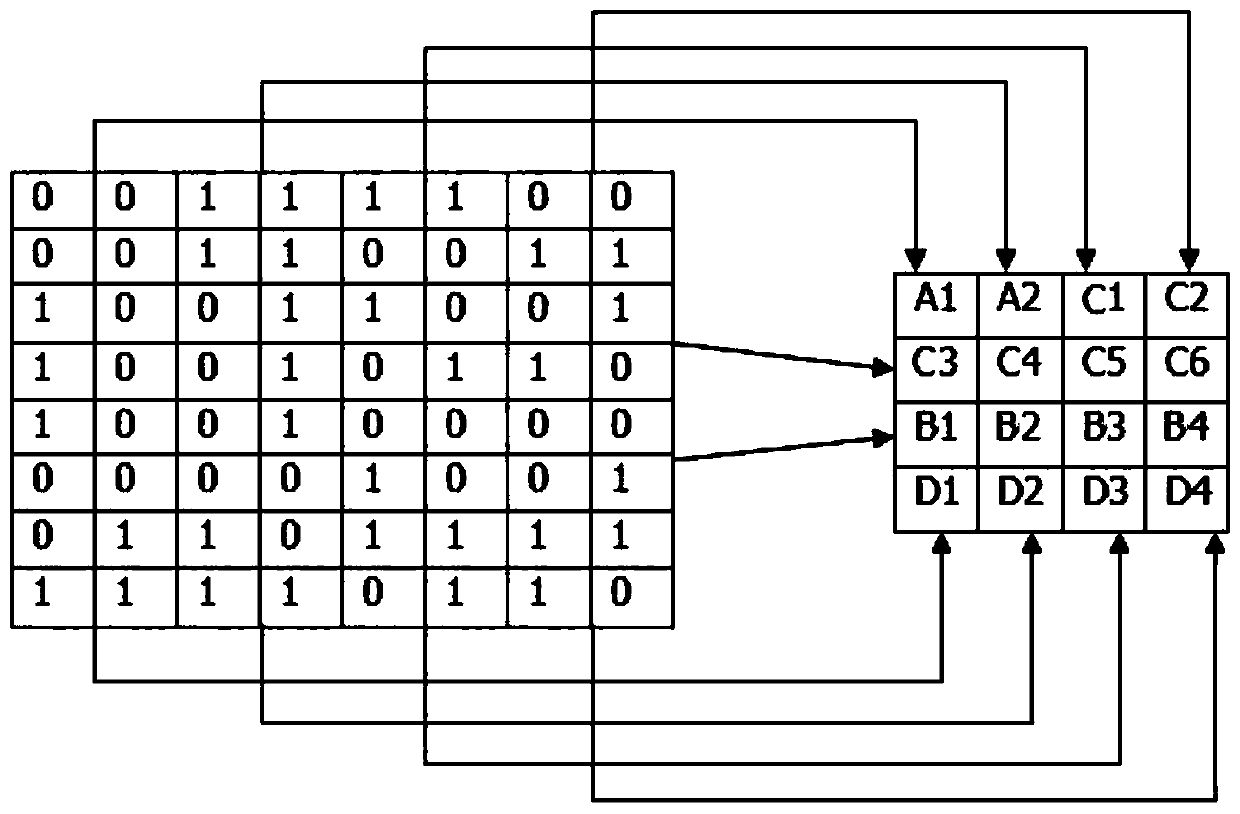
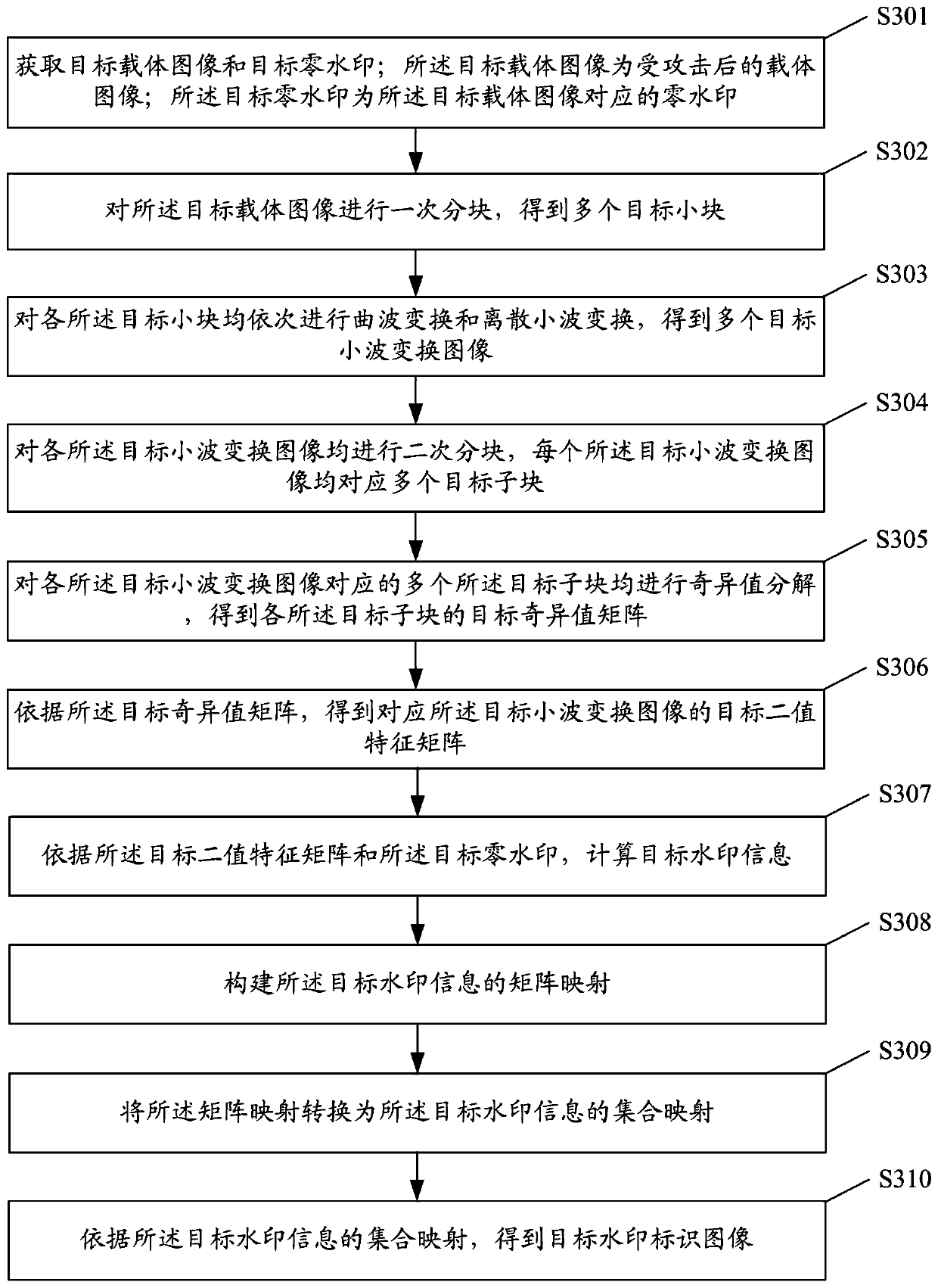
ActiveCN109727179AImprove stabilityReduce contact areaImage data processing detailsSingular value decompositionCharacteristic matrix
The invention discloses a zero watermark generation method and system and an extraction method and system. The zero watermark generation method comprises the following steps: obtaining a carrier imageand a watermark identification image; Carrying out primary blocking on the carrier image to obtain a plurality of small blocks; Performing curvelet transformation and discrete wavelet transformationon each small block in sequence to obtain a plurality of wavelet transformation images; Performing secondary partitioning on each wavelet transform image to obtain a plurality of sub-blocks; Performing singular value decomposition on the plurality of sub-blocks corresponding to each wavelet transform image to obtain a singular value matrix of each sub-block; Obtaining a binary feature matrix corresponding to the wavelet transform image according to the singular value matrix; Constructing set mapping of watermark identification images; Extracting watermark information of the watermark identification image according to the set mapping; And generating a zero watermark according to the binary feature matrix and the watermark information. The copyright protection of the carrier information canbe realized under the condition that the copyright identifier is not embedded, and the robustness and the stability of the zero watermark can be improved.
Owner:YANSHAN UNIV
Webpage text extraction method based on deep learning
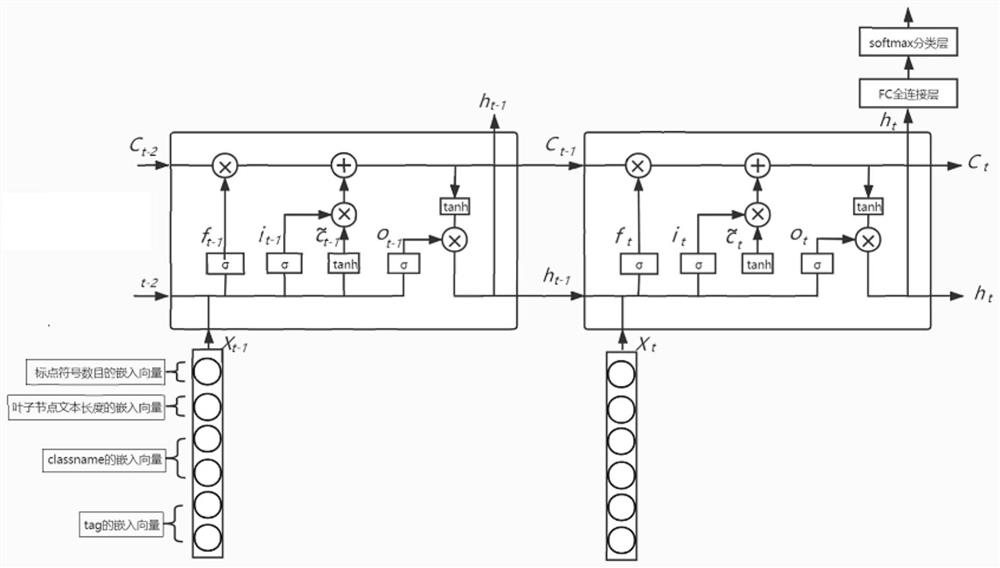
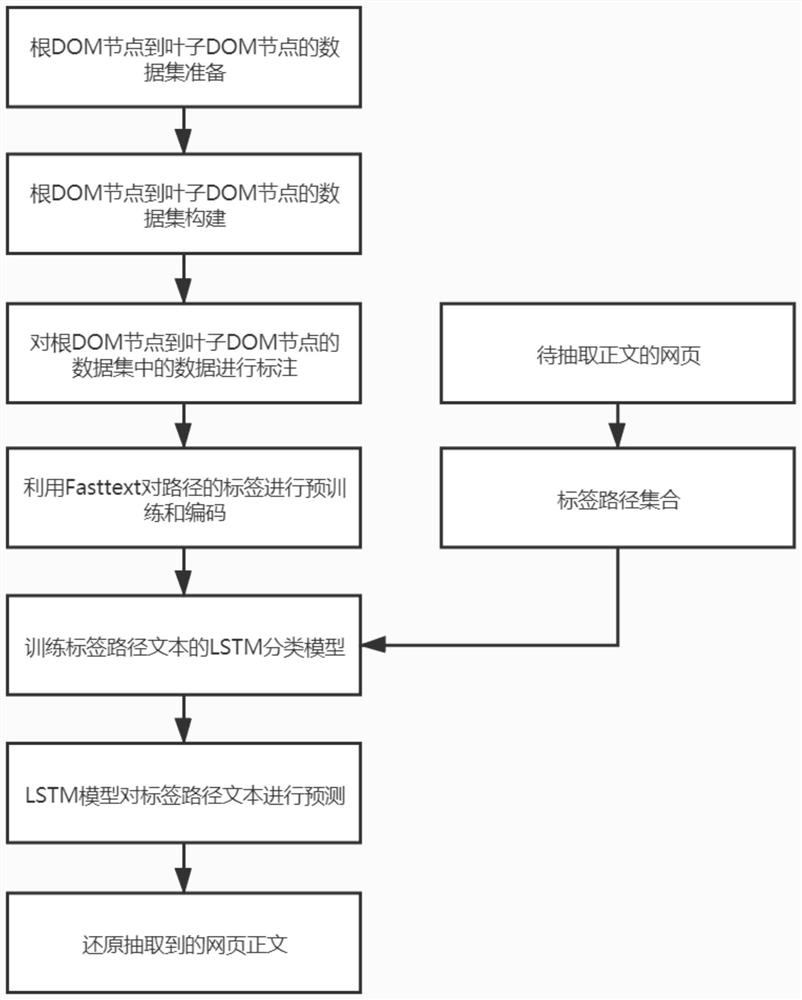
ActiveCN112667940AImprove the cost of manual labelingLow costNeural architecturesNeural learning methodsPathPingData set
The invention discloses a webpage text extraction method based on deep learning. The method comprises the following steps: 1) preparing a data set from a root DOM node to a leaf DOM node; 2) constructing a data set from a root DOM node to a leaf DOM node; 3) labeling data in a data set from the root DOM node to the leaf DOM node; 4) utilizing Fasttext to carry out pre-training and encoding on the label of the path; 5) training an LSTM classification model of the label path text; 6) enabling the LSTM model to predict the label path text; and 7) restoring the extracted webpage text. The invention belongs to the technical field of the Internet, and particularly relates to a webpage text extraction method based on deep learning, which improves the accuracy of resume webpage text extraction.
Owner:GUANGDONG ELECTRONICS IND INST
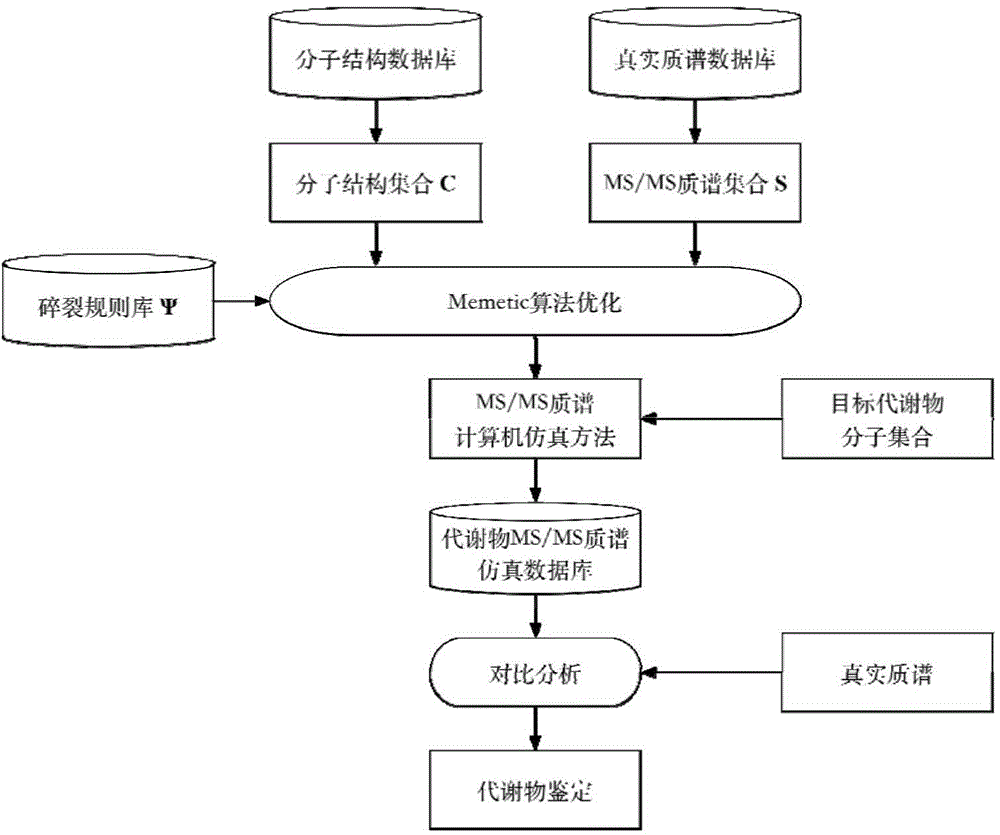
Metabolin MS/MS mass spectra computer simulation method
InactiveCN104834832AReduced prior knowledge requirementsAvoiding Design Methods That Are Not OptimalSystems biologySpecial data processing applicationsMemetic algorithmMass spectrometry
The invention discloses a metabolin MS / MS (mass spectra) computer simulation method. According to the method, optimization design is conducted on a fragmentation rule through an efficient Memetic algorithm, and the molecule mass spectra specificity serves as the fitness function value of an optimizing individual, so that the formed simulation method has the theoretically global optimum mass spectra distinguishing ability, and the accuracy of the metabolin identification can bee improved effectively. In the optimizing process, a sparse fitness function value is added to be used for guiding the optimizing individual, and it can be guaranteed that the formed fragmentation operation tree can be provided with the minimum redundancy. Accordingly, in the less molecule operation steps, the identification mass spectra with higher specificity is obtained, and robustness brought by the complex analysis process in an existing algorithm is avoided effectively. Finally, the method is not dependent on the real mass spectra and molecule data input particularly, and the formed simulation mass spectra data have the generality and can be used for establishing a general metabolin identification data base.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL +4
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com