Heap object Use-Afer-Free vulnerability detection method based on identifier consistency
A vulnerability detection and identifier technology, applied in platform integrity maintenance, instrumentation, computing, etc., can solve problems such as lack of and inability to detect Use-After-Free vulnerabilities, and achieve improved accuracy, low runtime overhead, and low memory. effect of overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
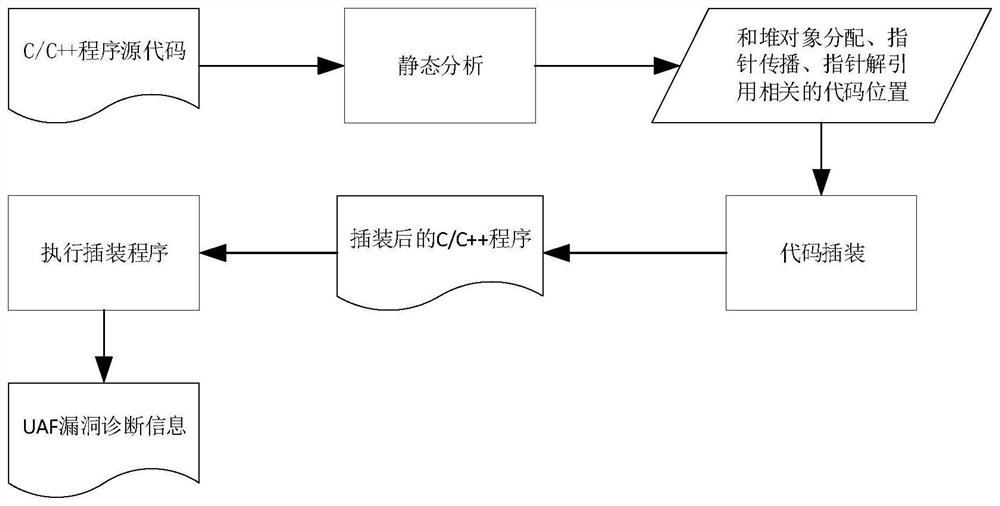
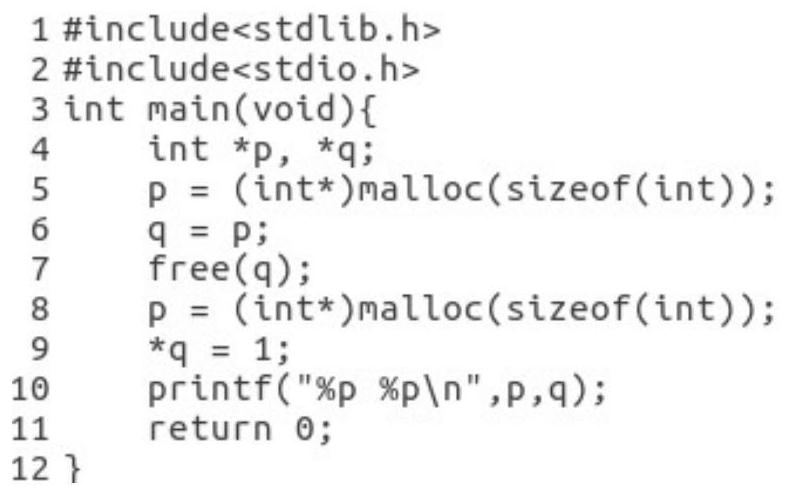
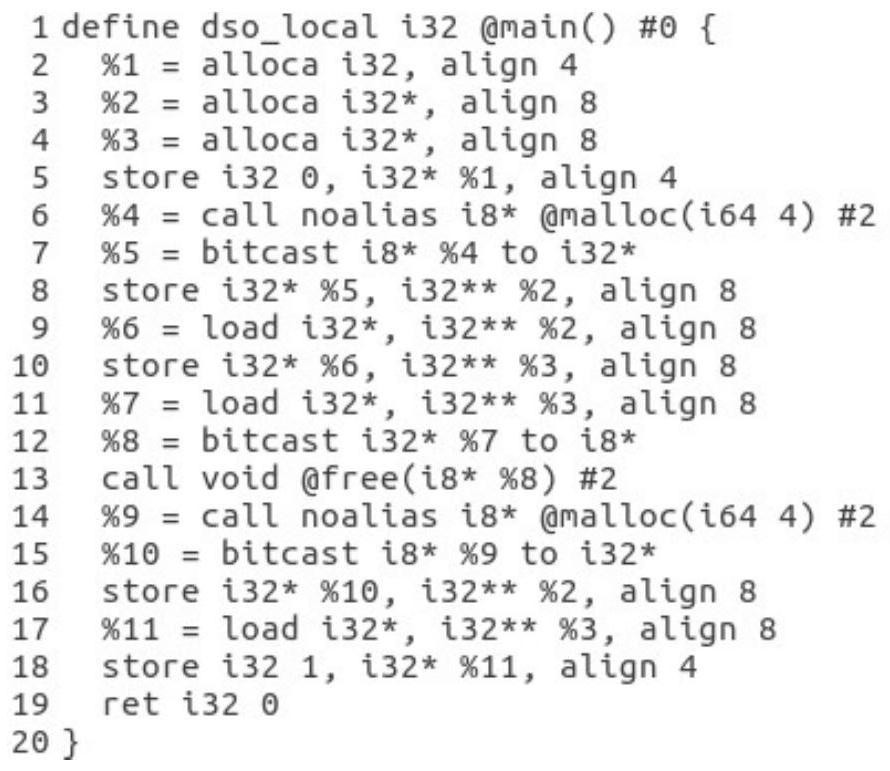
[0037]The invention is a heap object Use-After-Free vulnerability detection method based on identifier consistency, which takes the source code of C / C++ program as input and uses the detected heap object Use-After-Free vulnerability as output. In order to detect the heap object Use-After-Free vulnerability, first statically analyze the input C / C++ program to find the location of the code related to heap object allocation, pointer propagation and pointer dereferencing; after that, locate the relevant code location , perform code instrumentation on the C / C++ program to assign the same unique identifier to each allocated heap object and all pointers to that object and insert memory checks for pointer dereferences; finally, run the instrumented program , when the program is running, the instrumentation code will be executed to compare whether the object identifier of the pointer matches the identifier of the current object actually pointed to by the pointer, so as to detect whether...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com