Man-machine identification method based on sliding puzzle verification code
A human-machine identification and verification code technology, which is applied in the fields of digital data authentication, computer security devices, instruments, etc., can solve the problem that the traditional graphic verification code is not enough to provide security guarantee, etc., so as to achieve the difficulty of cracking and increase the cost, and improve the verification efficiency. and experience, the effect of increased difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
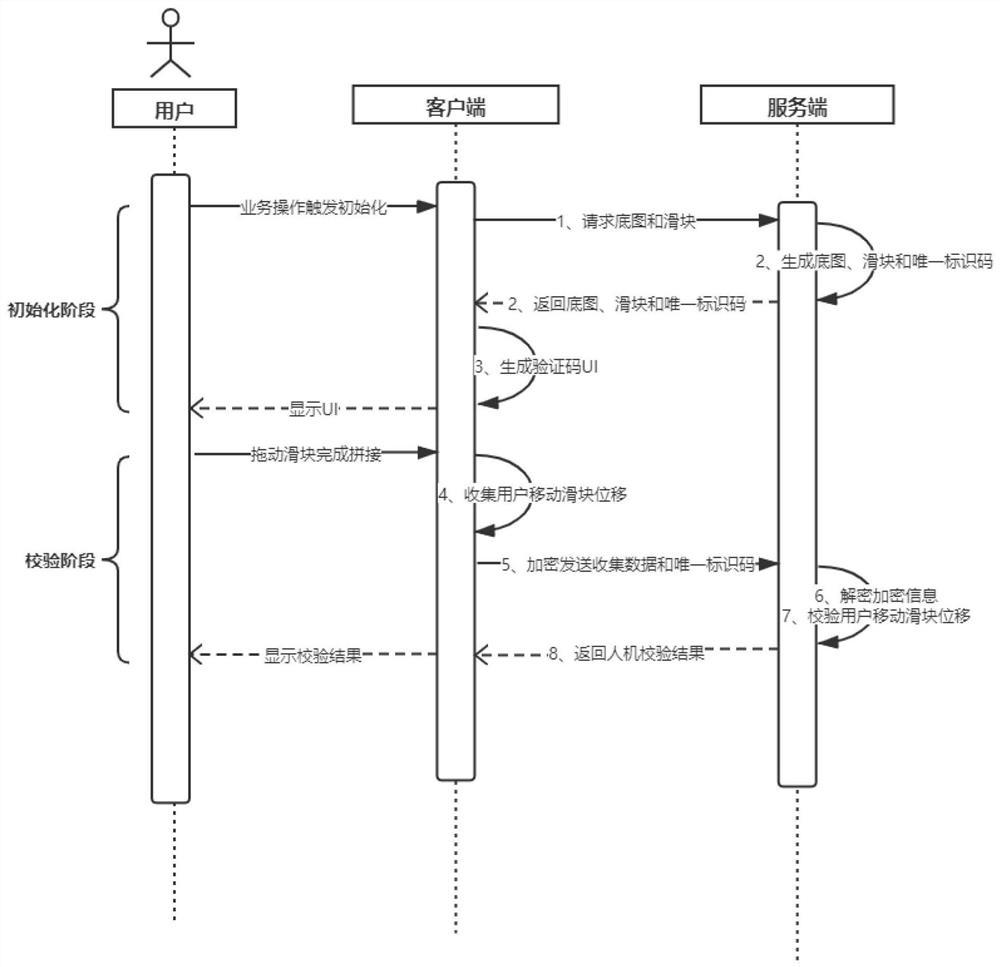
[0029] Example 1, such as figure 1 As shown, the present invention provides a kind of human-computer identification method based on sliding puzzle verification code and comprises the following steps:
[0030] Initialization phase:
[0031] (1) The client requests the base map and slider of the server;
[0032] Specifically, the client includes PC and mobile device browsers, WeChat applets, and terminal applications; requests include HTTP requests or TCP requests; the base map is the original image of the coding pattern at a random position; pattern.
[0033] (2) The server generates the base map, slider and unique identification code and returns them to the client;
[0034] Specifically, the original image and the slider are loaded into the memory from the hard disk when the container is initialized; the lower left corner of the original image is taken as the origin of the Cartesian coordinate system, and the width and height are the maximum values of the coordinate axes,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com