Enhancing cybersecurity and operational monitoring with alert confidence assignments
A confidence and alarm technology, applied in the direction of probabilistic network, computer security device, biological neural network model, etc., can solve the problem of attacking data integrity and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
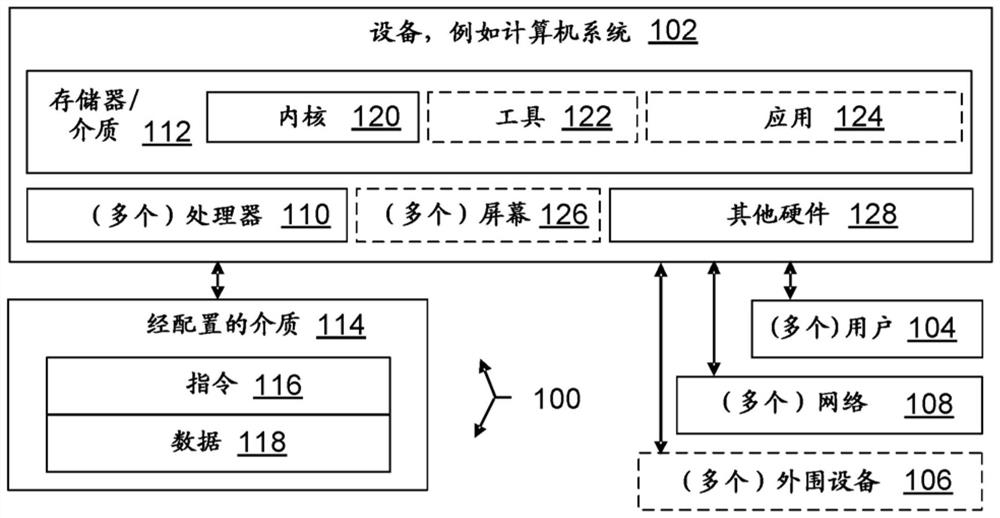
[0024] overview
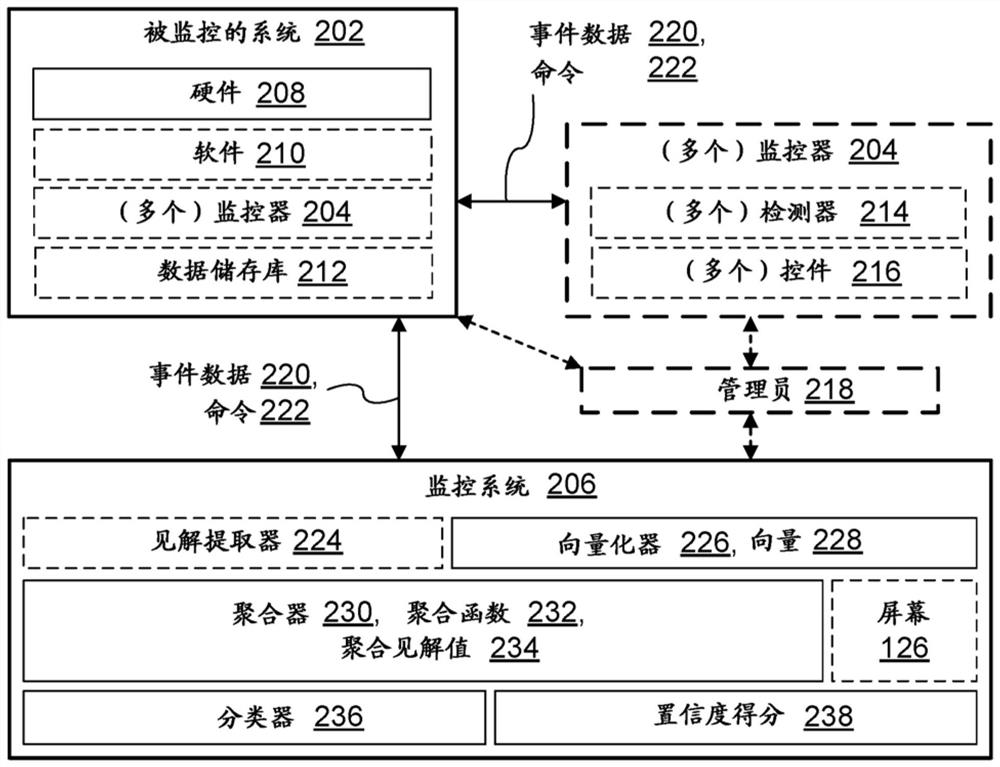
[0025] An innovation can go beyond its origin, but understanding its origin can help people understand that innovation more fully. In the present context, system monitoring innovations have emerged in the context of inventors seeking ways to improve system security. Computing systems are vulnerable to different types of attacks. To improve system security, organizations often track ongoing events in order to catch potential threats. Because false positives are common, security analysts sometimes investigate suspicious events further. These analysts examine different characteristics of a given event and based on these characteristics determine whether the event is malicious. The analyst's decision is used to trigger an alert to the system customer.
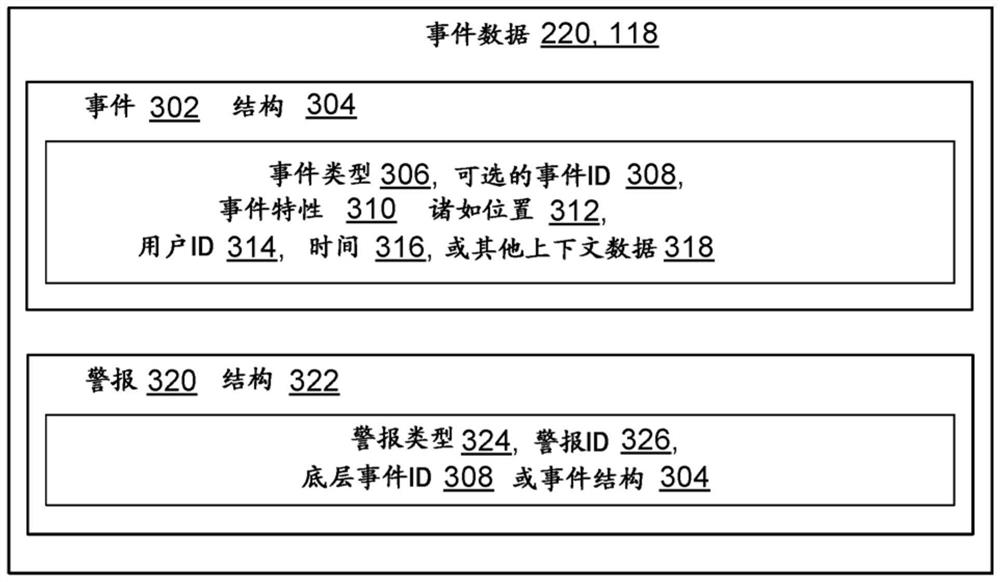
[0026] To track events in progress, intrusion detection systems and other security tools monitor individual machines, computer networks, and other computing systems for events. These tools can generate alerts...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com