Telnet proxy method and architecture separated from protocol stack, and medium
A protocol stack and heterogeneous technology, which is applied in the field of telnet proxy from the protocol stack to solve the problem of packet retransmission, increase security, and reduce CPU overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
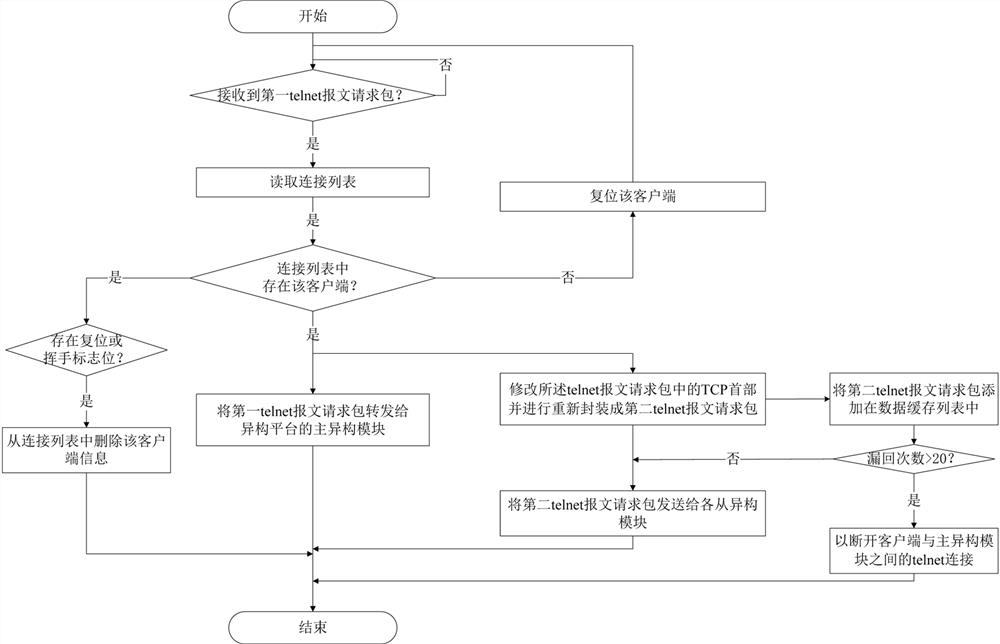
[0031] as attached figure 1 And attached image 3 Shown, a kind of telnet proxy method breaking away from protocol stack, described telnet proxy method breaking away from protocol stack comprises the following steps:
[0032] The input agent reads the connection list after receiving the first telnet message request packet, and judges whether the client sending the first telnet message request packet is registered in the connection list; if the client is registered in In the connection list, the first telnet message request packet is forwarded to the main heterogeneous module of the heterogeneous platform, and the TCP header in the first telnet message request packet is modified and repackaged into a second telnet message request packet. After requesting the packet, forward it to the slave heterogeneous module of the heterogeneous platform;
[0033] Build a data cache list, and register the second telnet message request packet forwarded to the slave heterogeneous module in th...
Embodiment 2
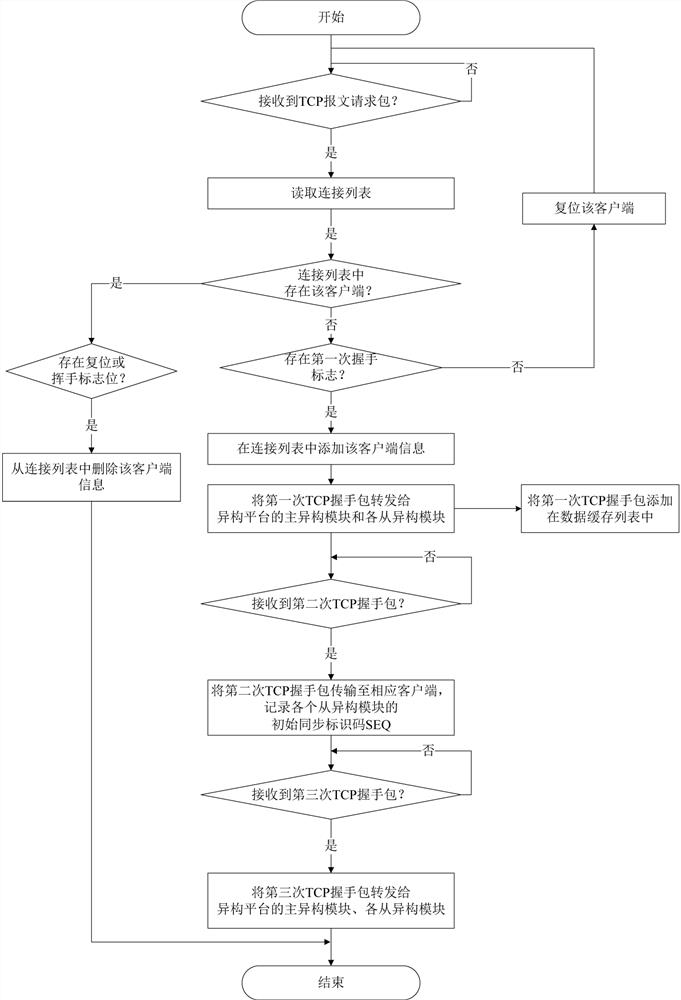
[0052] The difference between this embodiment and Embodiment 1 is that when modifying the TCP header in the first telnet message request packet and repackaging it into the second telnet message request packet, execute:
[0053] The input agent reads the initial synchronization identification code SEQ of the master heterogeneous module and the initial synchronization identification code SEQ of the slave heterogeneous module. Specifically, the master heterogeneous module corresponds to the initial synchronization identification code SEQ1, and the slave heterogeneous module 1 corresponds to the initial synchronization identification code SEQ2, corresponding to the initial synchronization identification code SEQ3 from the heterogeneous module 2, and so on; the initial synchronization identification code SEQ1 is randomly generated by the master heterogeneous module, and the initial synchronization identification code SEQ2 is randomly generated from the heterogeneous module 1 , the i...
Embodiment 3
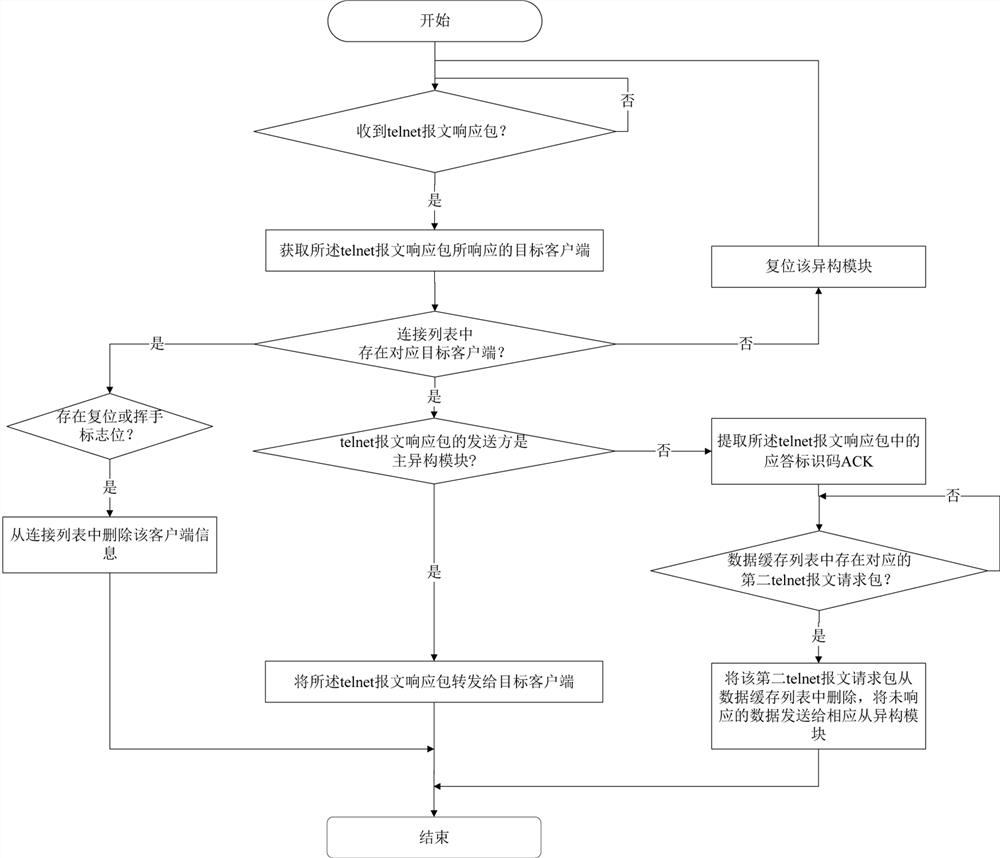
[0071] The difference between this embodiment and the foregoing embodiment is that, after registering the second telnet message request packet in the data cache list, execute:
[0072]Judging whether there is a second telnet message request packet that has not responded from the heterogeneous module in the data cache list, if there is a second telnet message request packet that has not responded from the heterogeneous module, then the corresponding slave Add 1 to the number of missed responses of the structural module, and retransmit the corresponding second telnet message request packet to the corresponding slave heterogeneous module, thereby solving the problem of message retransmission from the heterogeneous module.
[0073] It should be noted that, as attached Figure 4 As shown, the request data sent by the client is added to the data cache list. The data cache list has three operations: add / delete / find. According to the response identification code acknum of the data pac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com