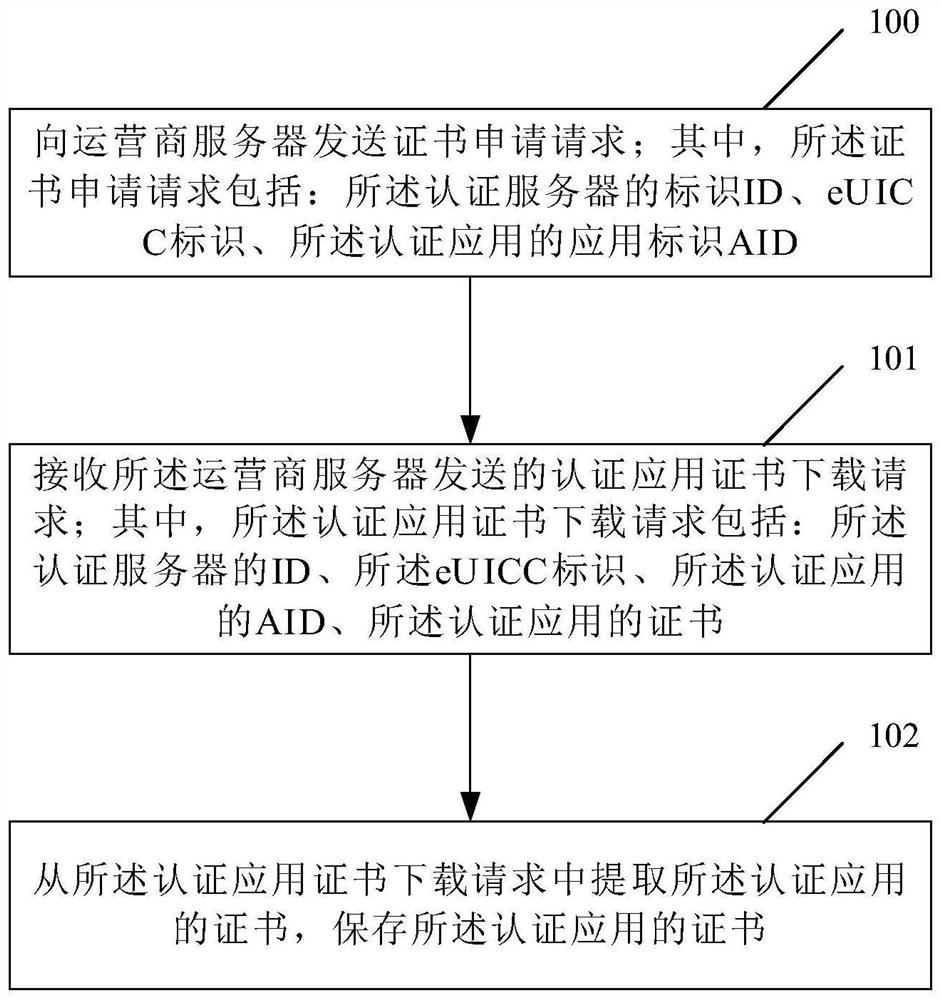
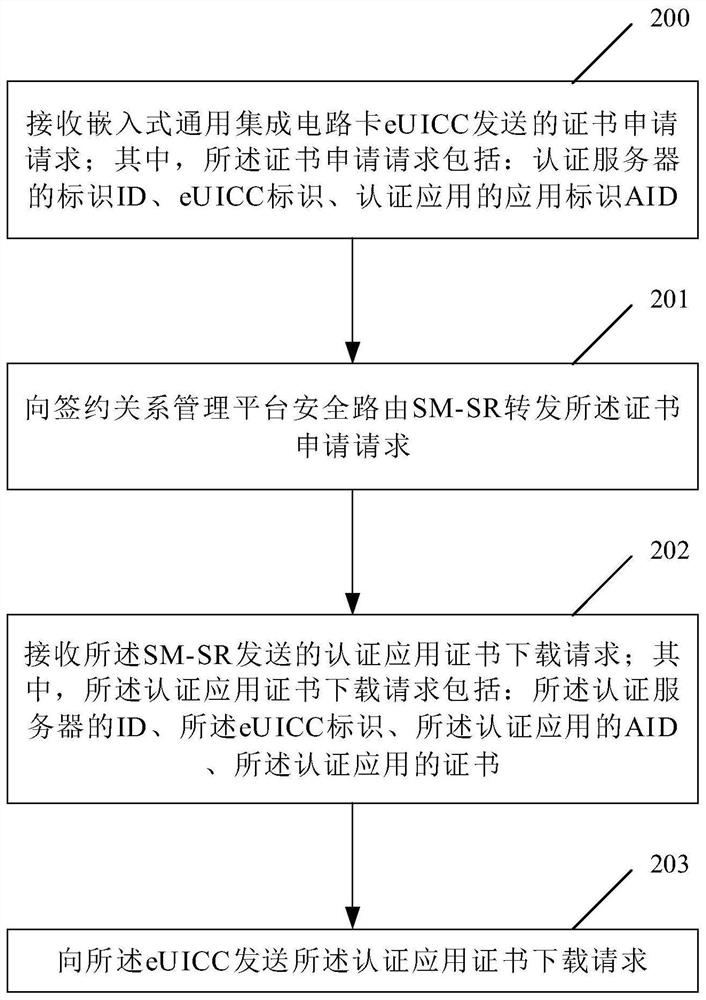
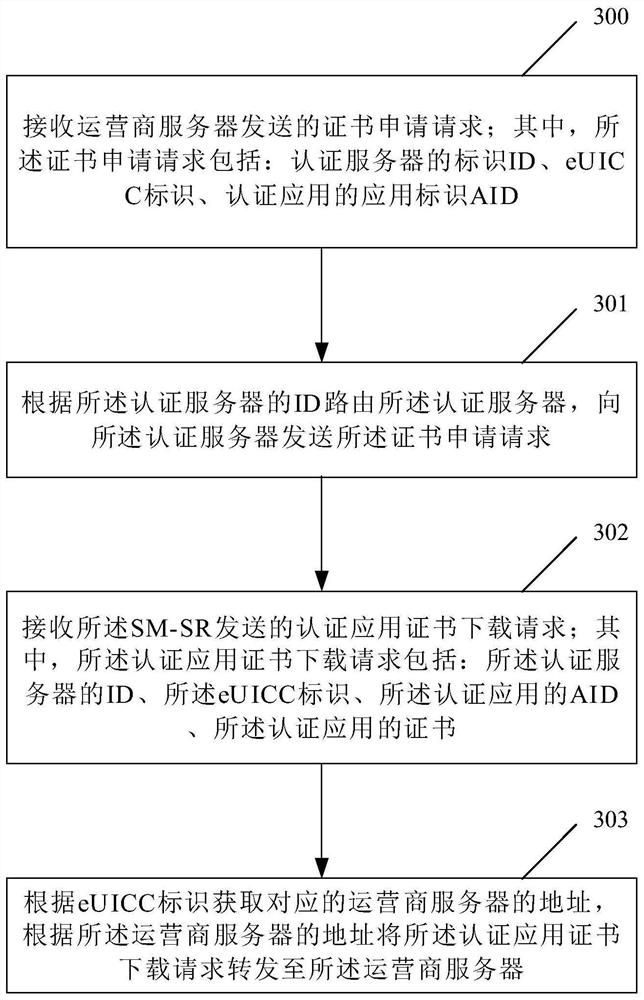
Method, device and system for managing and authenticating application certificate
A certificate and application identification technology, applied in the field of information security, can solve problems such as business models, product types, audience user restrictions, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0222] Initial conditions:
[0223] 1) This process can be combined with the download and installation process of the authentication application (such as an applet). Before the start of this process, the MNO-SD of the currently activated profile of the eUICC has obtained the authentication application through presetting or downloading and installing.
[0224] 2) Before the start of this process, the authentication application has obtained the public key PK.AuServer of the authentication server through preset or configuration.
[0225] Such as Figure 5 As shown, the method flow for downloading the authentication application certificate includes:
[0226](1) The authentication application generates the public-private key pair of the authentication application: the public key PK1.AuApplet of the authentication application and the private key SK1.AuApplet of the authentication application generate RC (ie RC1), and use the public key PK.AuServer of the authentication server to T...
example 2
[0255] Initial conditions:
[0256] 1) Before the start of this process, the MNO-SD of the currently activated profile of the eUICC has obtained the authentication application, the private key SK.AuApplet of the authentication application, and the certificate CERT1.AuApplet of the authentication application through presetting or downloading and installing.
[0257] 2) Before the start of this process, the authentication application has obtained the public key PK.AuServer of the authentication server through preset or configuration.
[0258] Such as Image 6 As shown, the method flow for updating the authentication application certificate includes:
[0259] (1) The authentication application generates a new public key PK2.AuApplet and a new private key SK2.AuApplet of the authentication application according to its own certificate update requirements or receives a certificate update command from the authentication server, and generates a new RC (ie RC2), use the public key PK...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com