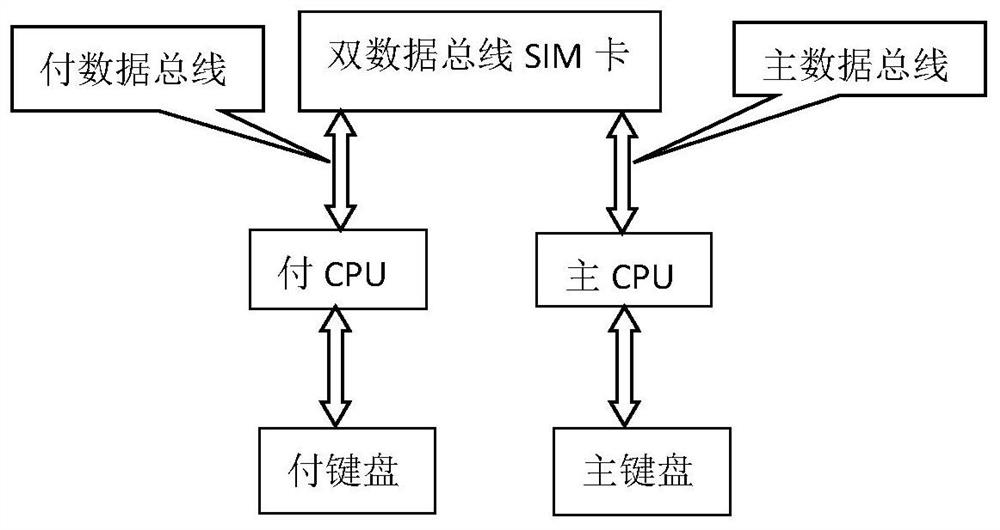
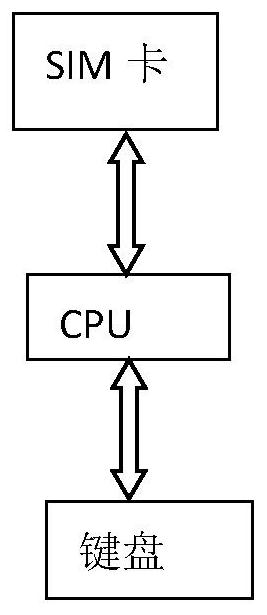
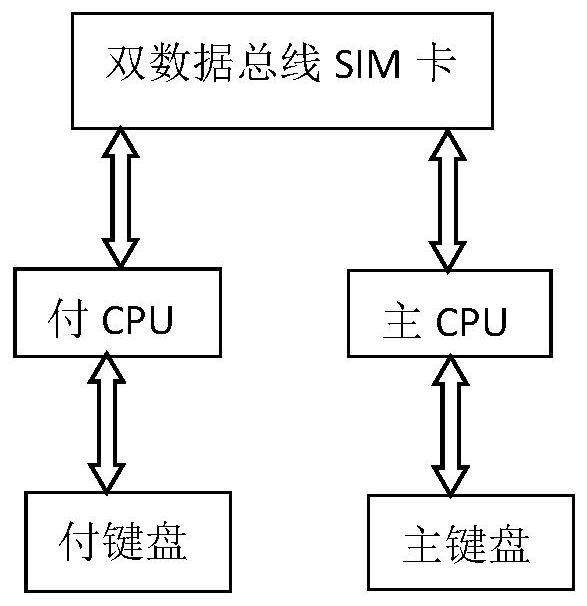
Information terminal with two keyboards
A technology of information terminals and keyboards, which is applied in the protection of internal/peripheral computer components, digital data protection, platform integrity maintenance, etc., and can solve problems that cannot be verified, cannot be falsified, and security holes cannot be repaired.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0026] figure 2 It is a schematic diagram of the current smart phone structure.
[0027] It should be noted that the current smart phone structure is far more than figure 2 The schematic diagram of is much more complicated. For example, the number of CPUs in smartphones is more than just one in the schematic diagram. But no matter how complicated the structure of the smart phone is, its CPU runs on the operating system, and the application system runs on the operating system. Each independent application system running on the operating system has its own independent core sensitive data. These core sensitive data, in figure 2 There are at least three leak directions on smartphones of
[0028] Direction 1: Security vulnerabilities in operating systems and application systems.
[0029] Direction 2: Smartphone CPU processes memory residual data of core sensitive data.
[0030] Direction 3: Unruly web applications, theoretically speaking, can also steal the installation of...
Embodiment 2
[0044] Figure 4 It is a schematic diagram of the current mobile network-based IoT terminal structure.
[0045] It should be noted that in reality, some of the various IoT terminals based on mobile networks are far more Figure 4 The structure in is much more complex. But as long as it is an IoT terminal based on the mobile network developed based on the operating system, it can basically be used Figure 4 structural expression. Figure 4 structure of the IoT terminal, compared to figure 2 The security defense situation of smart phones with different structures is even more pessimistic. There are two reasons:
[0046] Reason 1: The limited product budget makes it impossible for IoT terminals to invest too much resources in the design of technical protection solutions, and the protection effect is naturally limited. And this limited protective effect will become weaker and weaker as time goes by.
[0047] Reason 2: Most of the IoT terminals are unaccompanied during the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com