Timed task-based data increment static desensitization implementation method and system
A technology of timed tasks and implementation methods, applied in the field of big data security, can solve problems such as hidden security risks, incremental data sensitivity and privacy cannot be protected in a timely manner, and achieve security privacy, data privacy and sensitivity. The effect of protection, robust security cycle
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
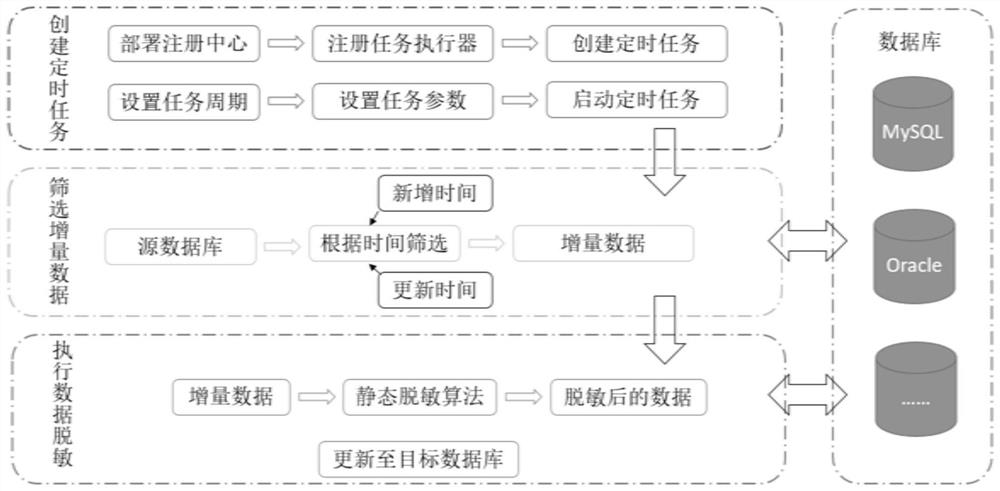
[0043] as attached figure 1 As shown, the method for implementing static desensitization of data increments based on timed tasks of the present invention is specifically as follows:
[0044] S1. Create a scheduled task: deploy a scheduled task registration center, configure a scheduled task executor and register to the registration center, create a scheduled task at the same time, set the execution cycle and task parameters of the scheduled task, and start the scheduled task;
[0045] S2. Filter incremental data: regularly filter out incremental data by scheduled tasks;
[0046] S3. Execute data desensitization: the scheduled task periodically calls the API interface for performing incremental data desensitization to realize incremental desensitization.
[0047] The timing task in this embodiment is based on the xxl-job open source framework for secondary development. It is deployed as a timing task executor through configuration items and sends a registration request to the ...
Embodiment 2
[0061]The data incremental static desensitization system based on timing tasks of the present invention is developed using Java technology, implemented based on the SpringBoot framework, and releases the timing incremental desensitization function as an API interface, allowing front-end developers and application services to call; front-end Developers are used to develop web front-end pages, develop static pages and functional functions based on jsp and js related technologies in web technology, and support customers to freely choose the options of full desensitization, incremental desensitization, timing execution and manual execution to realize database and The selection of data tables supports MySQL, Oracle, Sqlserver and DB2 relational databases; the system includes,
[0062] Create a module for deploying the scheduled task registration center, configure the scheduled task executor and register to the registration center, create a scheduled task at the same time, set the ex...
Embodiment 3
[0076] An embodiment of the present invention also provides a computer-readable storage medium, in which a plurality of instructions are stored, and the instructions are loaded by a processor, so that the processor executes the XXXX method in any embodiment of the present invention. Specifically, a system or device equipped with a storage medium may be provided, on which a software program code for realizing the functions of any of the above embodiments is stored, and the computer (or CPU or MPU of the system or device) ) to read and execute the program code stored in the storage medium.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com