Fine-grained access control method and system based on double block chains
An access control and fine-grained technology, which is applied in the field of data security technology and blockchain, can solve problems such as difficult to cope with data fine-grained access control requirements, and achieve the effects of high reliability, guaranteed interests, and guaranteed integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
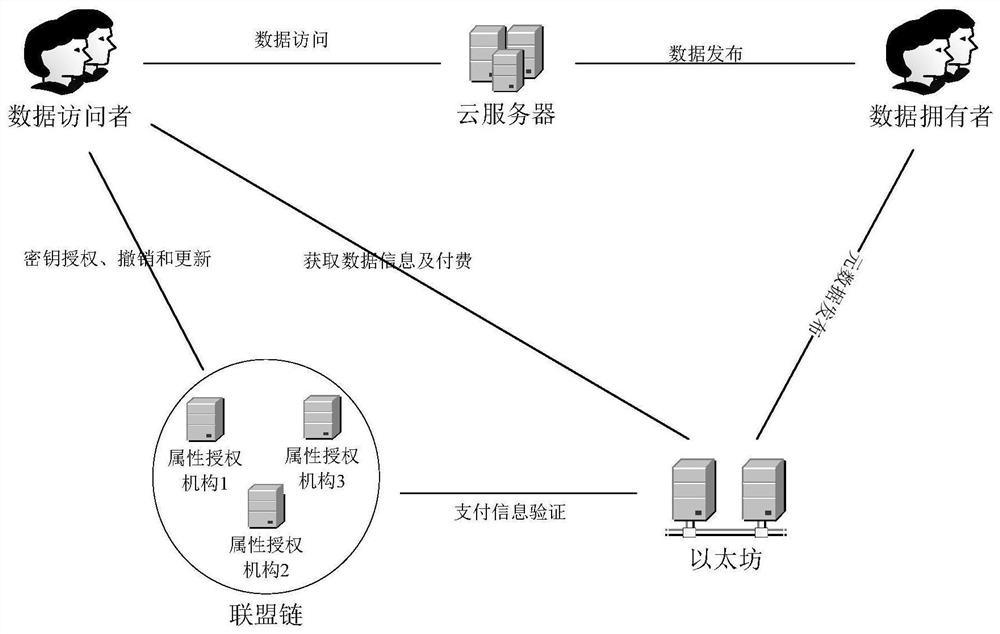
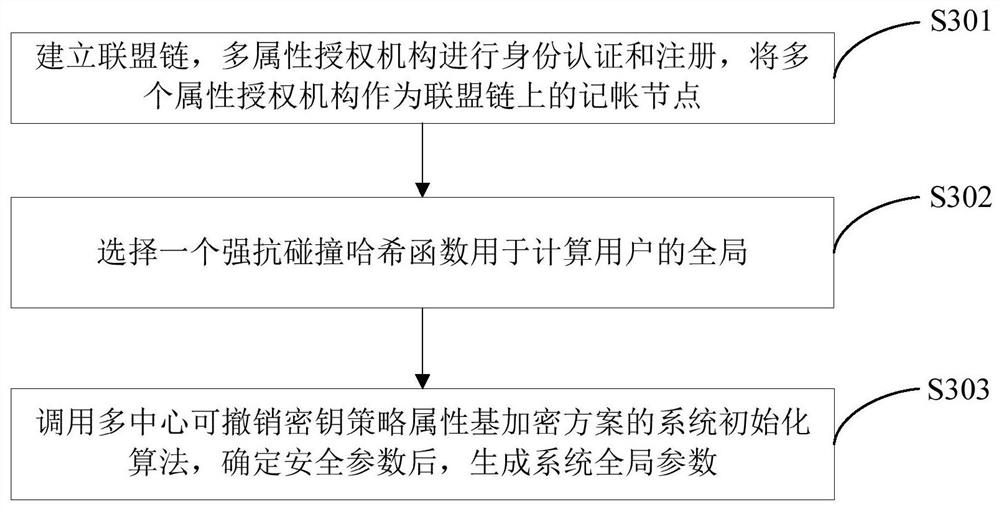
[0110] like figure 1 As shown, this embodiment provides a fine-grained access control system based on dual blockchains. The system includes six entities, namely alliance chain, Ethereum, data owner, data visitor, cloud server and multiple Attribute authority, the description of each entity is as follows:
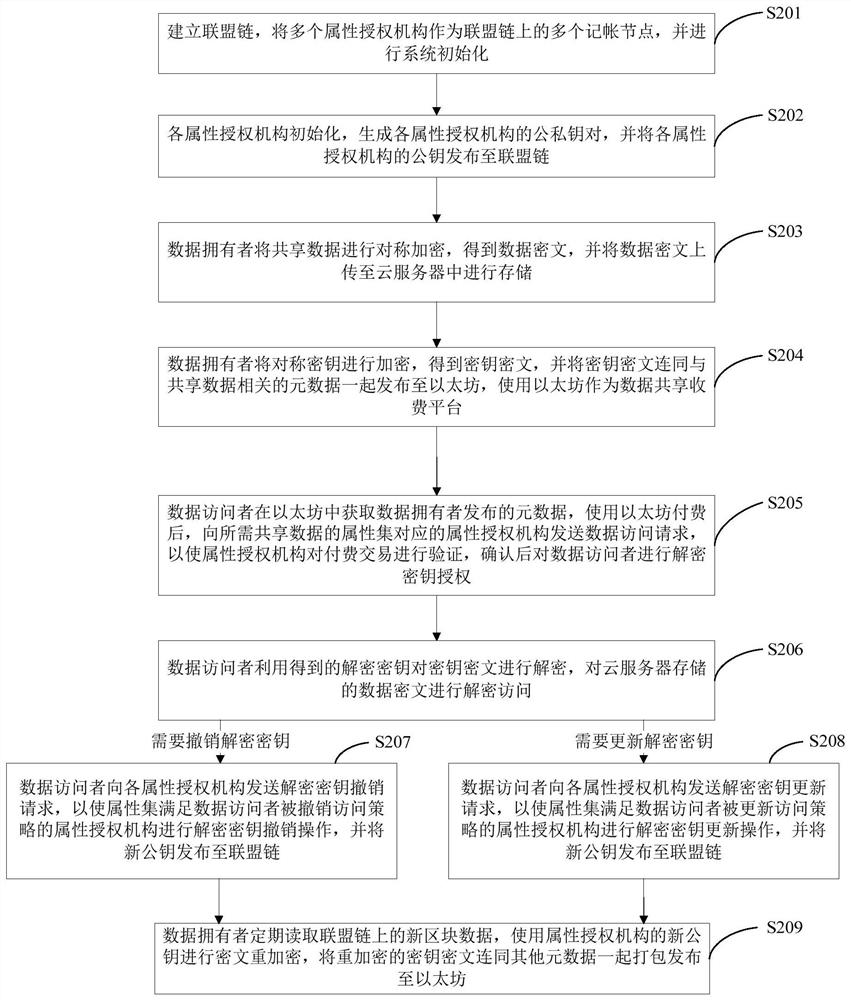
[0111] Data owner: An entity that shares the data it owns for a fee, such as a farming enterprise with big data on poultry farming; it is used to symmetrically encrypt the shared data to obtain data ciphertext, and upload the data ciphertext to the cloud server for storage ;Encrypt the symmetric key to obtain the key ciphertext, and publish the key ciphertext together with the metadata related to the shared data to Ethereum, and use Ethereum as the data sharing charging platform.
[0112] Data visitor: An entity that needs to access data, such as an institution that studies poultry farming or epidemic prevention and control; it is used to obtain the metadata released by the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com