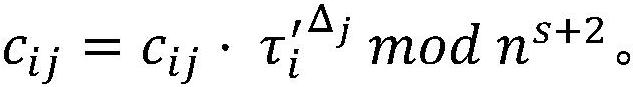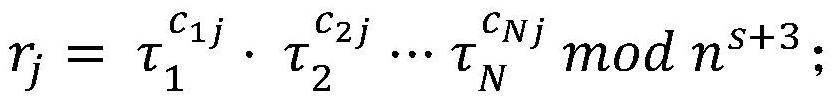Efficient remote service attack resistant outsourcing data storage and access method
A technology for outsourcing data and remote services, which is applied in the field of outsourcing data storage and access to efficiently resist remote service attacks, and can solve problems such as difficulty in resisting malicious remote server attacks, high communication overhead, and large client computing workloads.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
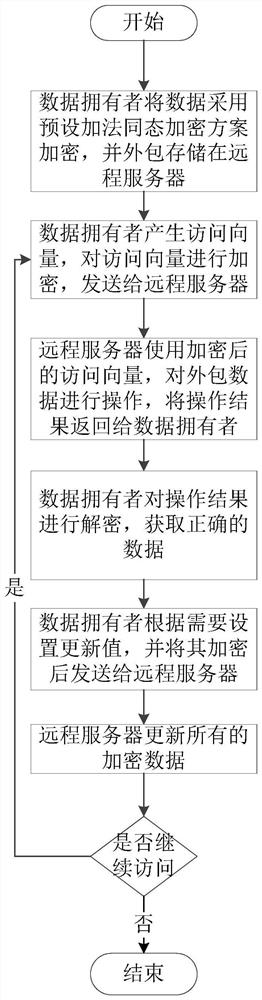
[0038] The present invention provides an outsourced data storage and access method that is highly effective against remote service attacks, such as figure 1 shown, including the following steps:
[0039] set up is a key generation function of a special additive homomorphic encryption scheme, κ is a security parameter, ε pk (s, m) is an encryption function, is the decryption function, where s is an encryption and decryption parameter whose type is a positive integer, m and c are the plaintext to be encrypted and the ciphertext to be decrypted respectively, pk and sk are the public key and private key of the additive homomorphic encryption scheme respectively key; the special additive homomorphic encryption scheme for Construction; let H() be a secure hash function with strong anti-collision; Encode ecc () and Decode ecc () is the coding function and the decoding function of the error correction code;
[0040] In practical applications, the security parameter λ can be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com