5G communication security test method and system
A communication security and testing system technology, applied in the field of wireless communication security, can solve the problems of complex challenges, inability to test, no hardware platform test device, etc., to achieve stable and reliable performance, improved security, and a wide range of applications.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the present invention will be further described below in conjunction with specific illustrations.
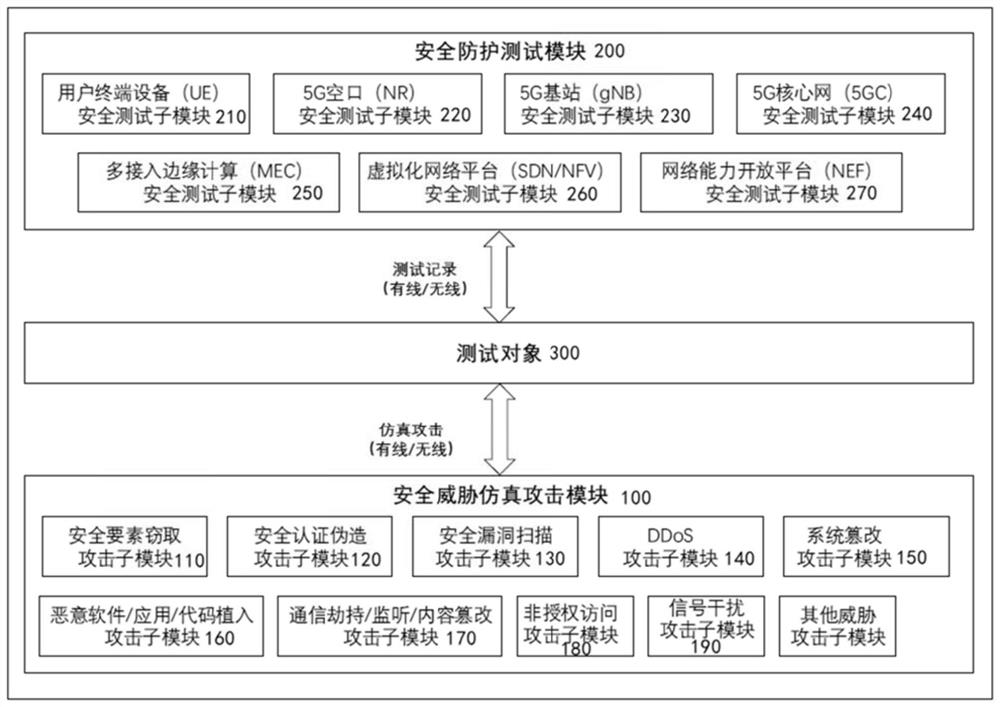
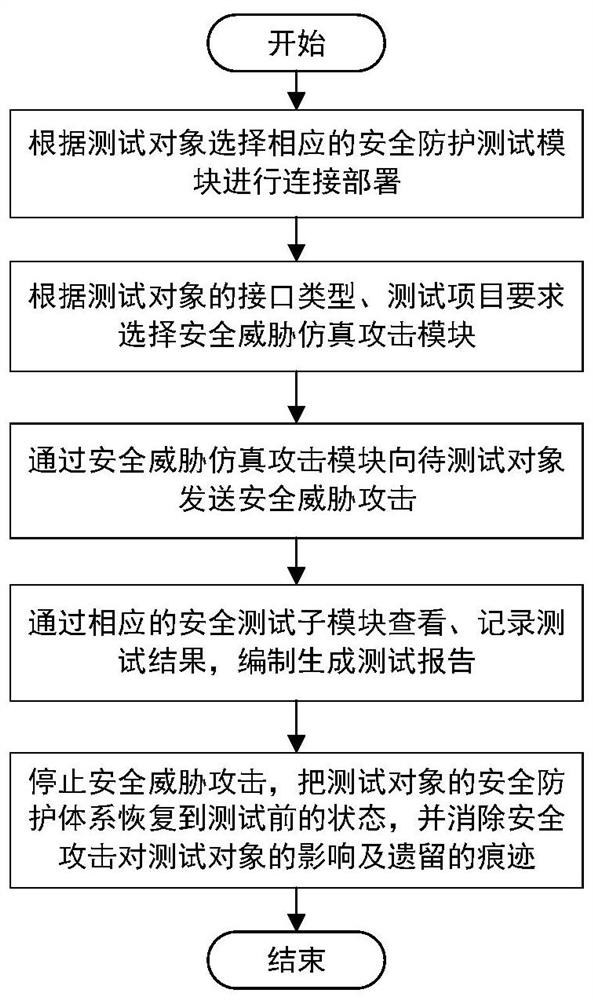
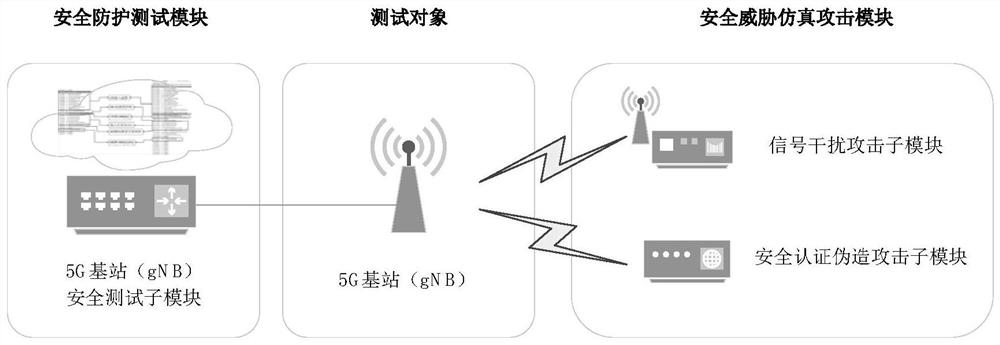
[0045] In order to comprehensively and efficiently test the security of 5G communication security, this solution simulates the security threat simulation attack according to the interface type of the test object and the test project requirements, and sends the security threat simulation attack to the test object in the normal working state. This simulates the situation where the object under test is attacked by a security threat;
[0046] At the same time, evaluate whether the security protection system of the test object is perfect and effective according to the reaction of the test object after being attacked and the effect of the attack.
[0047] Accordingly, this solution provides a 5G communication security test system to realize the above-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com