Lateral movement attack detection method and system based on heterogeneous graph network
A lateral movement, attack detection technology, applied in neural learning methods, biological neural network models, digital data authentication, etc., can solve problems to be studied, high false alarm rate, high concealment, etc. The effect of reporting
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] In order to better understand the technical solutions in the embodiments of the present invention, the objects, features and advantages of the present invention can be further understood, and the techniques of the present invention will be further detailed in connection with the accompanying drawings and examples. instruction of.
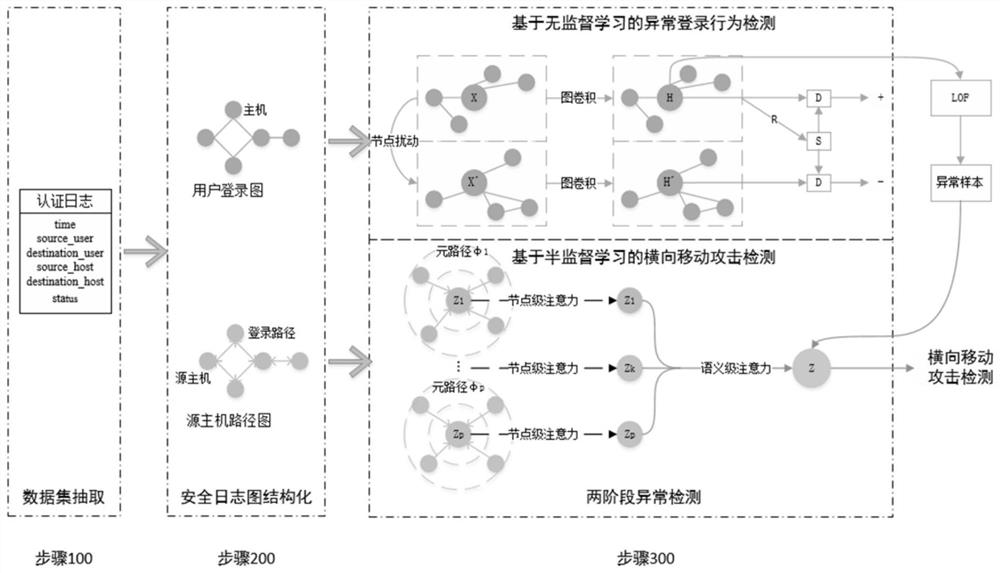
[0034] In the present invention, a method of detecting a transverse moving attack based on a heterogeneous diagram network is disclosed, such as figure 1 As shown, this method is mainly composed of data acquisition, safety log chart, and is based on unwaver login behavior detection and the four parts: the main steps based on the horizontal mobile attack detection of semi-supervising learning. The main steps are as follows:
[0035] Step 100 is extracted for data set, that is, collecting the authentication log generated by the network device for a period of time, constitutes a data set.
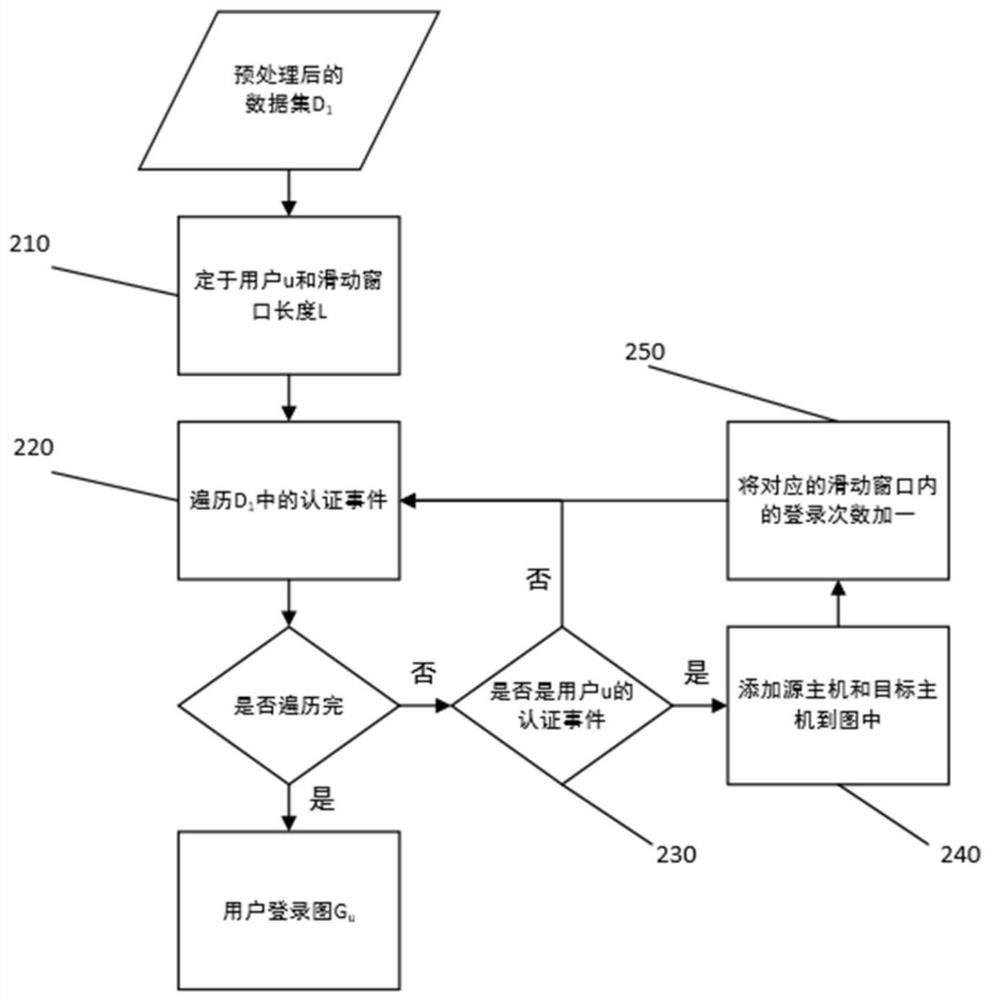
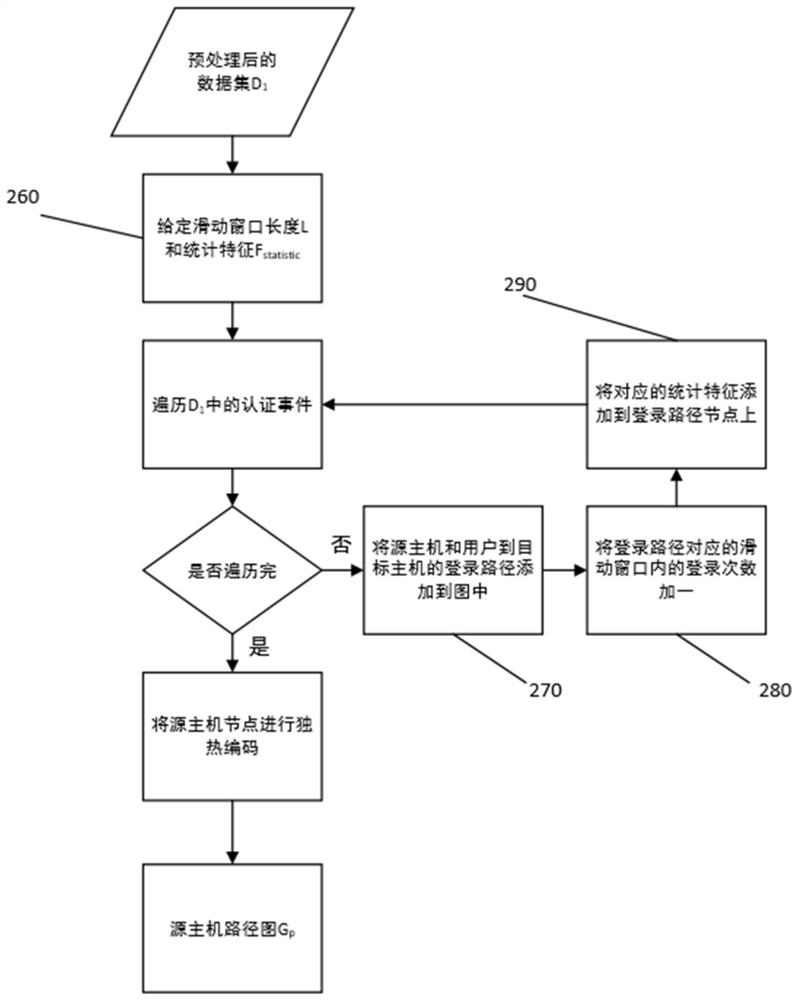
[0036] Step 200 is structured for the security log chart, m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com