Web attack protection method and system based on SQL injection
A rule and database technology, applied in the field of network security, can solve the problems of inaccurate results, low efficiency, large processing, etc., and achieve the effect of improving network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Hereinafter, preferred embodiments of the present invention will be described in detail with reference to the accompanying drawings. It should be understood that the preferred embodiments are only for illustrating the present invention, but not for limiting the protection scope of the present invention.
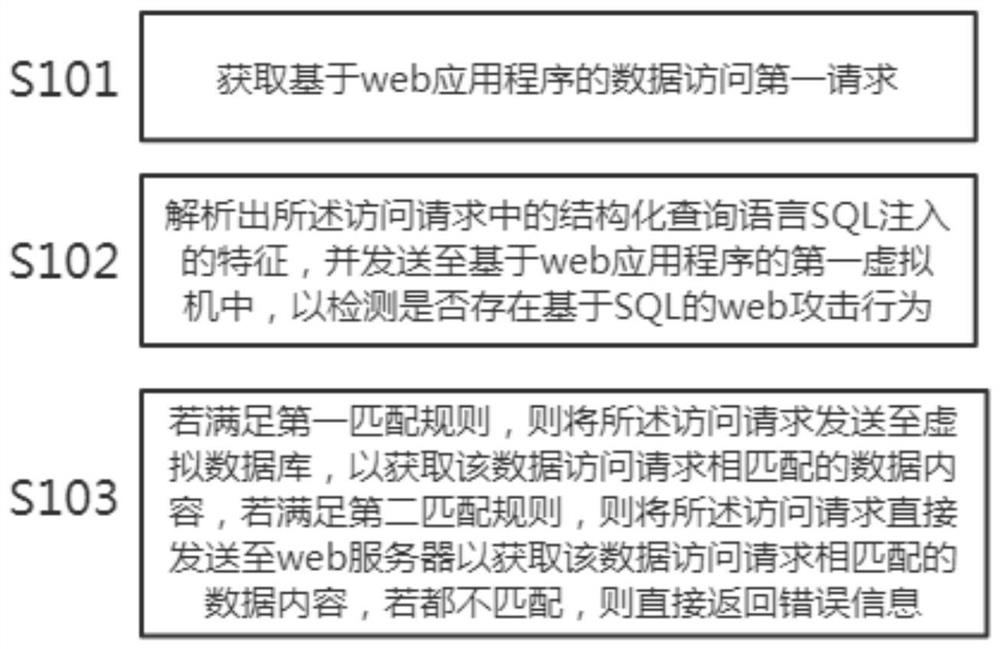
[0035] Such as figure 1 As shown, the present invention proposes a kind of web attack protection method based on SQL injection, and this method specifically comprises:
[0036] Step S101: Obtain a first request for data access based on a web application.
[0037] SQL injection vulnerability is a vulnerability generated in the process of Internet data transmission based on website security. When the web application transmits SQL queries to the backward database, if the attacker can modify the syntax or meaning of the SQL statement, SQL injection may occur. Attackers can conduct SQL attacks through web form data, malicious IP address attacks, parameter modification of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com