Method and device for training risk identification model
A risk identification and model technology, applied in the field of training risk identification models, can solve problems such as network behavior security threats, and achieve the effect of saving computing resources and improving training efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0072] The solutions provided in this specification will be described below in conjunction with the accompanying drawings.
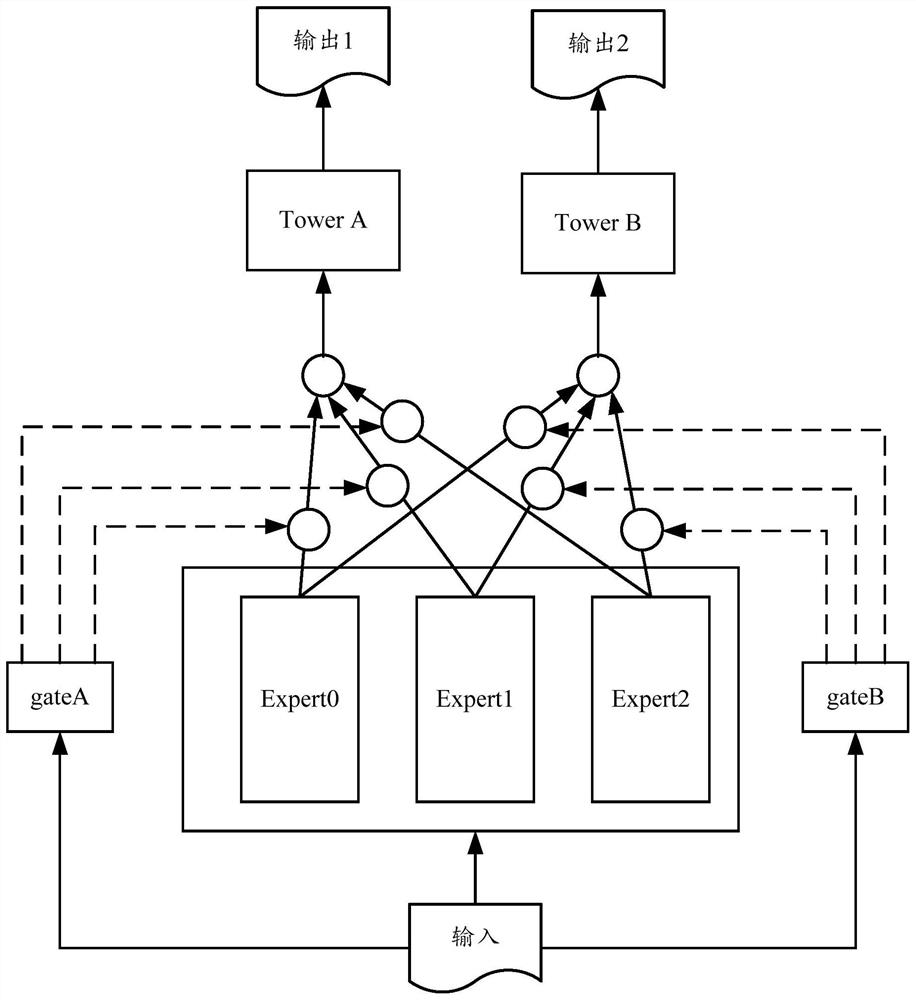
[0073] Risk identification usually divides risk domains or risk types based on business, such as fraud risk, misappropriation risk, cheating risk, gambling risk, money laundering risk, etc. Risk subjects include, for example, risk users, risk merchants, risk accounts, and so on. Although the levels and nature of risk are different, there are some common characteristics. If the experience and knowledge of various risk types can be used to share algorithms and models, it will effectively improve the efficiency of model training and effectively save computing resources.
[0074] The specific implementation of the above idea is described below.
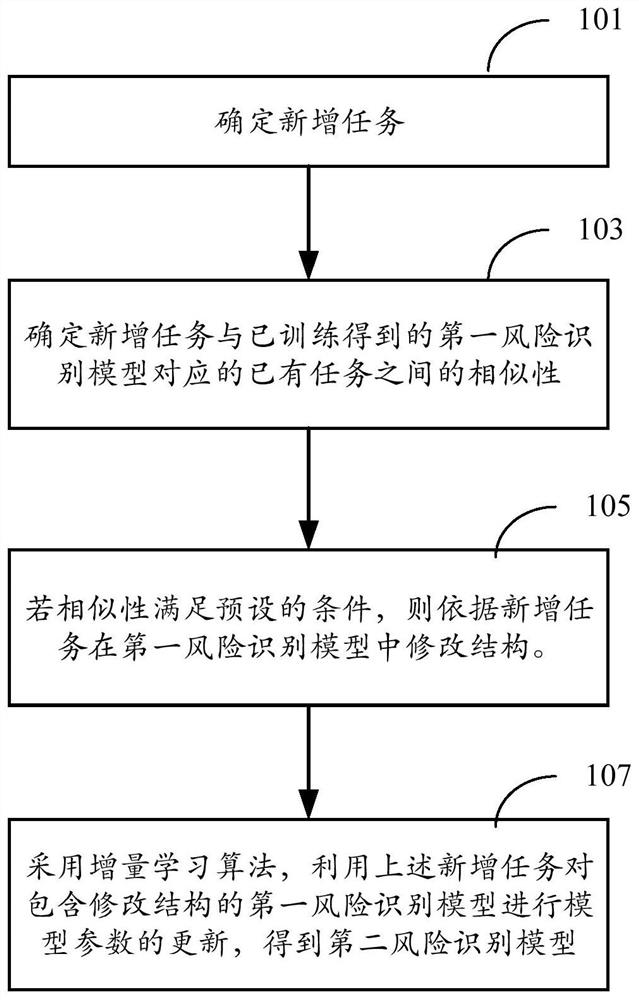
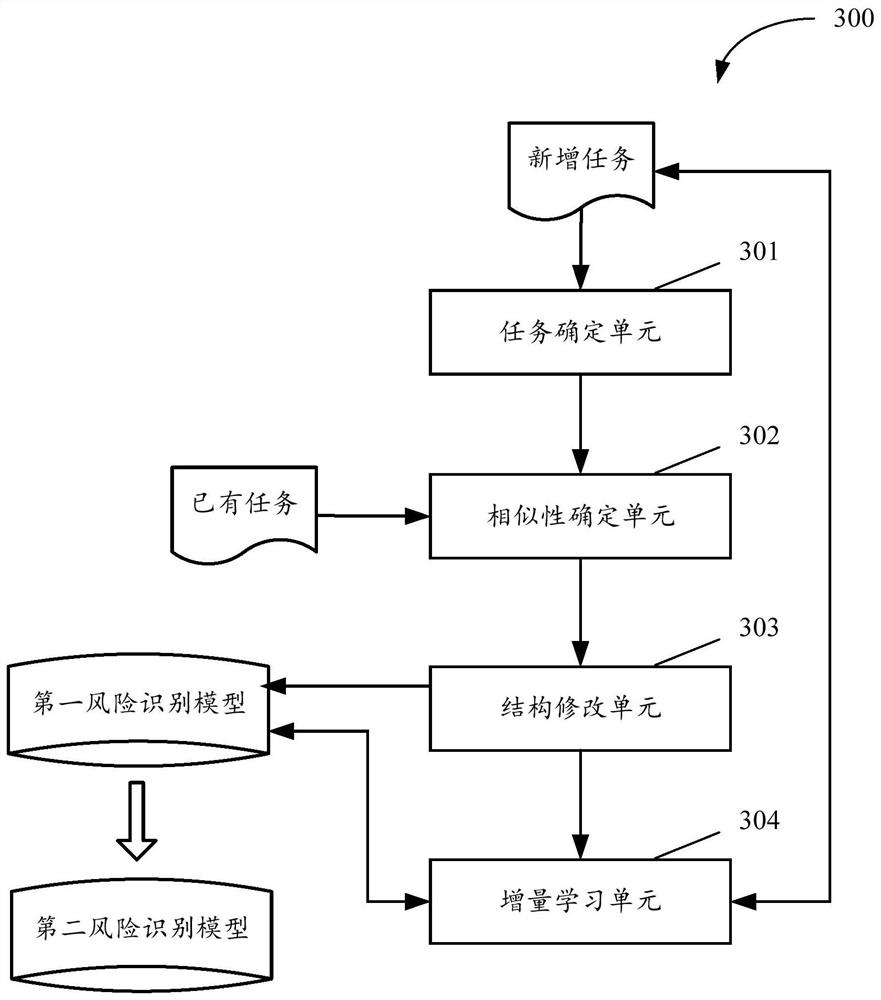
[0075] figure 1 A flowchart of a method for training a risk identification model according to an embodiment is shown. It can be understood that the method can be executed by any device, device, platform, or devi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com