A Distributed Security State Reconfiguration Method Based on Double-layer Dynamically Switching Observers
A safe state and observer technology, applied in safe communication devices, digital transmission systems, electrical components, etc., to reduce the possibility of collapse, ensure safe reconstruction, and contain the effect of impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
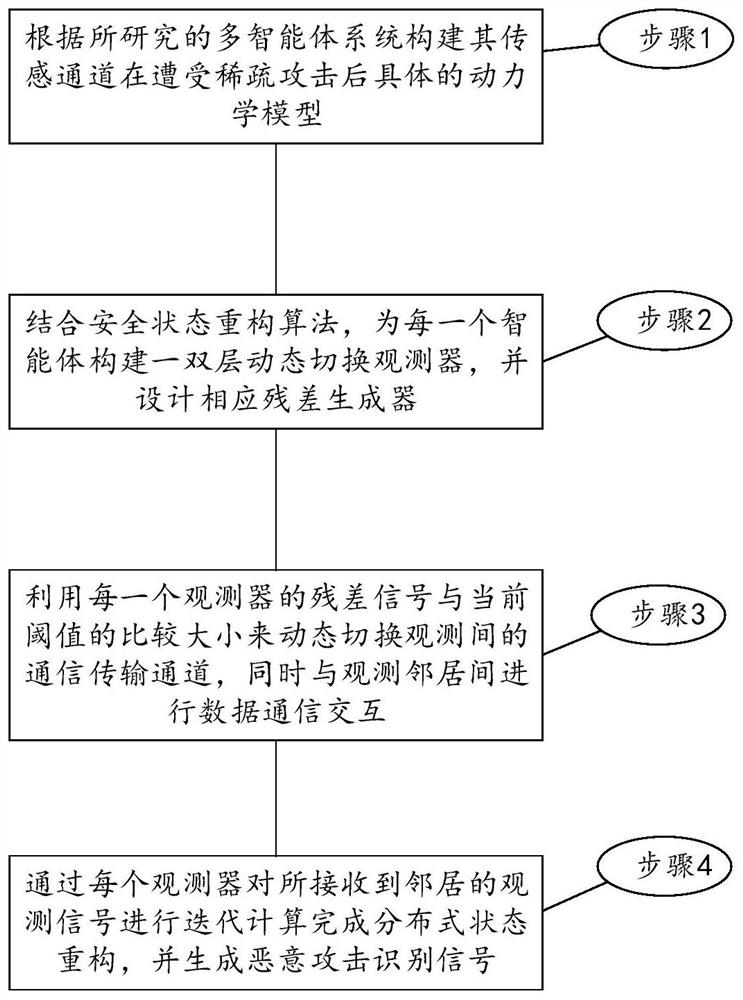
[0066] Step 1. For a multi-agent system consisting of 5 unmanned vehicles, the dynamic model is as follows:
[0067]
[0068] The attacker randomly selects the sensor transmission channels of 2 cars for attack injection every 5s, and the bad data injection function is d i (t)=(-ip i 0.5e t / 20 ) T .
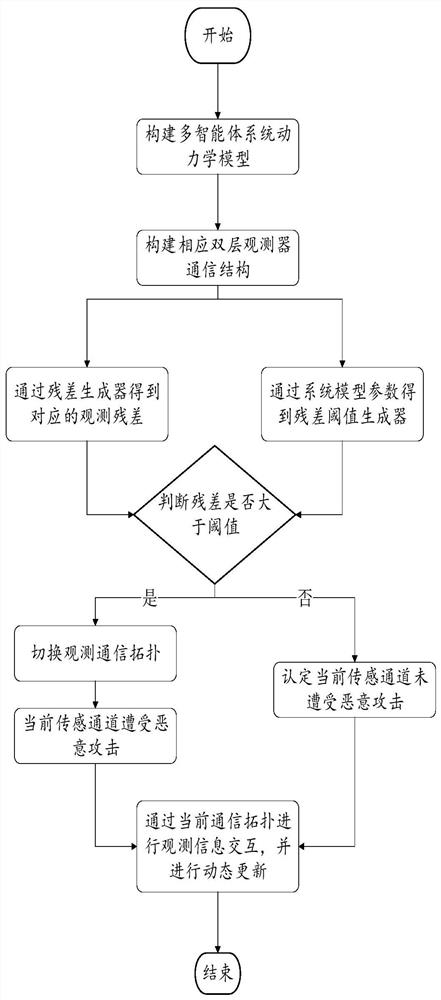
[0069] Next, according to figure 2 The described process is used to solve the corresponding parameters to realize the distributed security state observation of multi-agents.
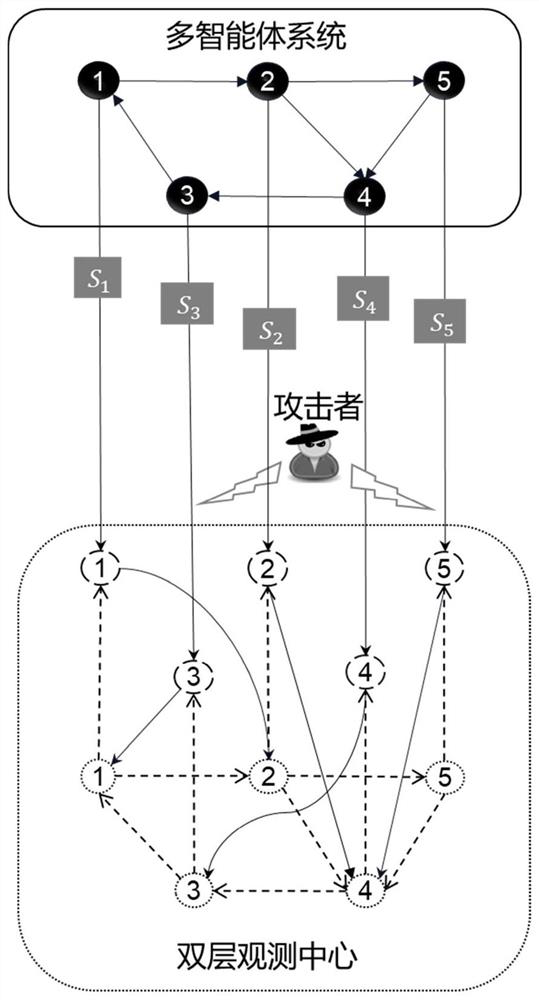
[0070] Step 2, the communication topology between the 5 cars and the double-layer observer is as follows image 3 The dotted circles represent the first-layer observer and the second-layer observer respectively; the solid line in the observer channel represents the communication topology channel when the observer determines that there is no malicious attack, and the dashed line represents the dynamic when the observer determines that there is a malicious attack. Switched communication channel. St...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com