Key generation method based on position uniqueness information
A key generation and unique technology, applied in the key field, can solve the problems of low key cost, difficult key distribution and management, and immaturity, and achieve the effect of short running time, increased complexity, and resistance to dictionary attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
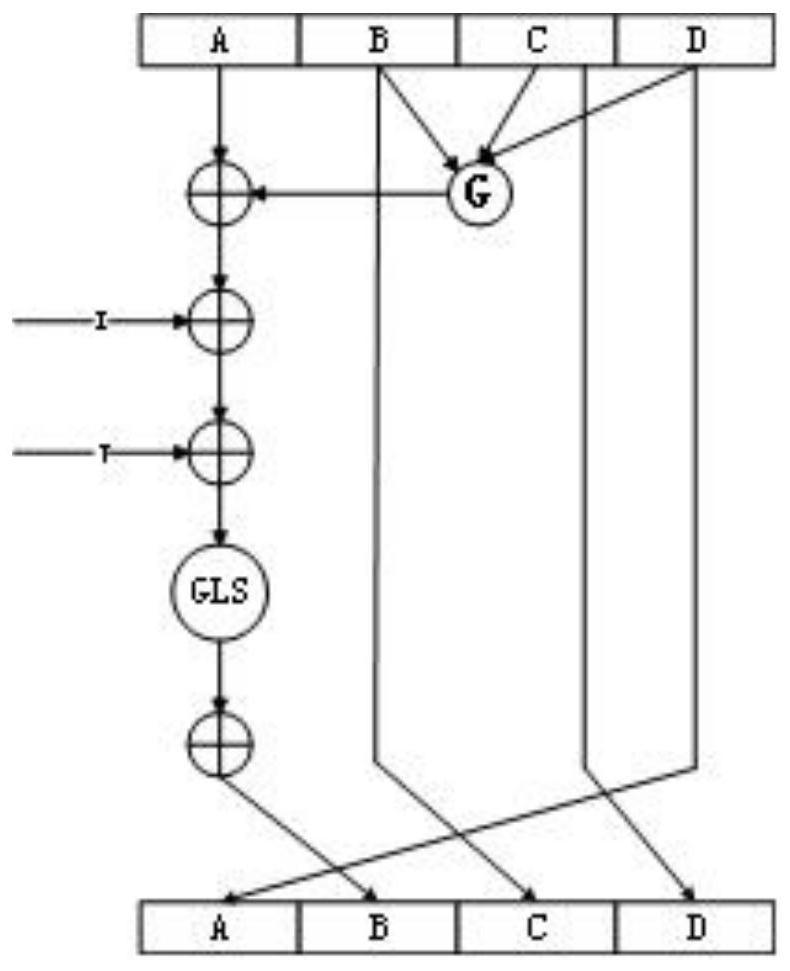
Method used
Image
Examples
Embodiment
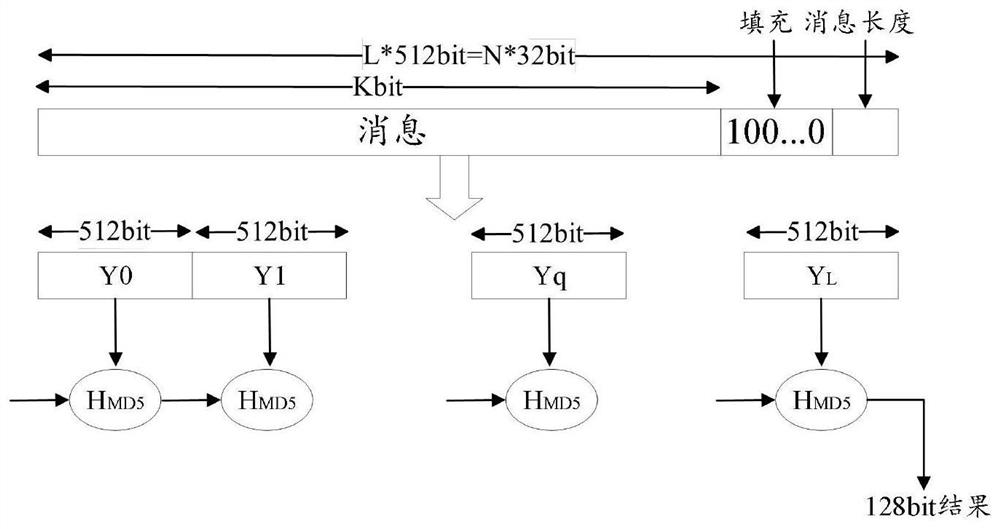
[0057] Table 1 is a statistical table of the initial value of the Logistic map changing with the time-varying factor. It can be seen that when the time-varying factor changes linearly, the generated random initial value changes irregularly and completely randomly. Under the same conditions, it can be guaranteed that the Logistic chaotic sequence generated by using the initial value is completely random, thereby ensuring the disorder of the filling method, which is beneficial to the MD5 algorithm to resist dictionary attacks.
[0058]
[0059]
[0060] Table 1 Logistic mapping initial value and time factor change result table
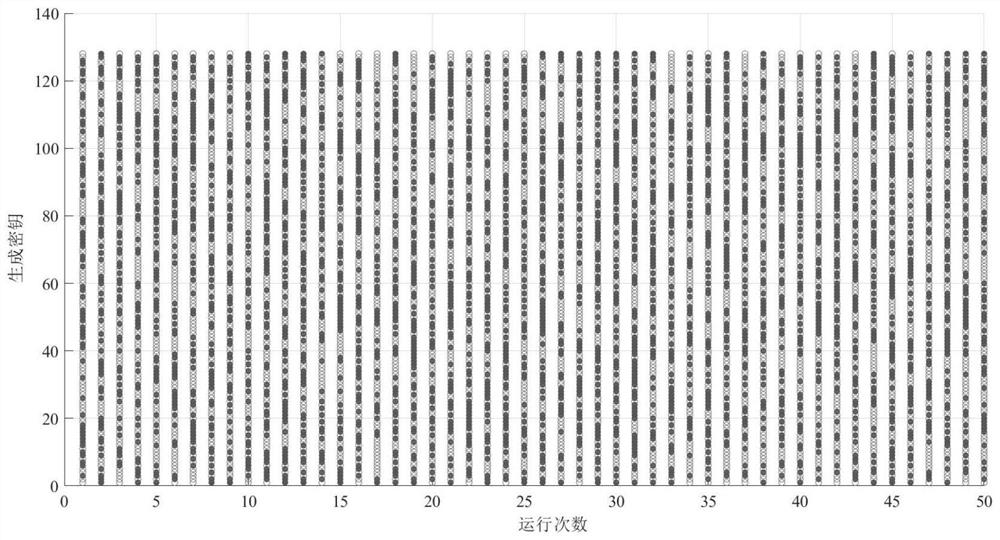
[0061] Table 2 and image 3 Respectively reflect the change result of the generated key with the time factor. It can be found from the table that when the time factor changes linearly from 70 to 79, the generated key changes irregularly and completely randomly; image 3 It reflects the key results generated by changing the time factor in repeated...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com