Proof-of-work algorithm optimization method and device, computer equipment and storage medium
An optimization method and an optimization device technology, which are applied in complex mathematical operations, special data processing applications, and other database retrievals, and can solve problems such as system performance degradation, memory read bandwidth performance bottlenecks, and unpredictable data extraction operation cycles
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
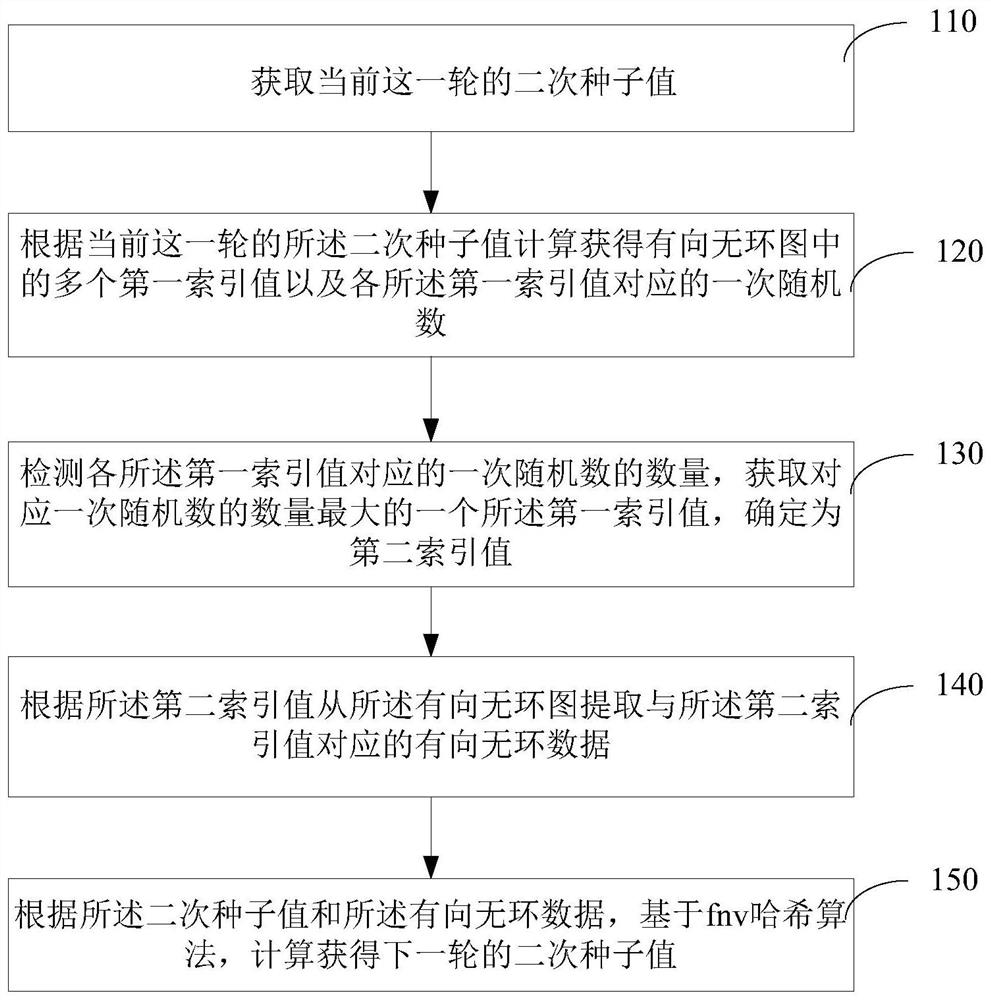
[0053] In this example, if figure 1 As shown, a workload proof algorithm optimization method is provided, which includes:
[0054] Step 110, obtain the secondary seed value of the current round.
[0055] Specifically, this step is one of the steps in the ethash algorithm, specifically the step of calculating and obtaining the secondary seed value. The secondary seed value can be obtained by encrypting the initial seed value in the initial round, or can be obtained by calculating the FNV hash algorithm in any round after the initial round.
[0056]In this embodiment, in the step of calculating the secondary seed value of the ethash algorithm, the secondary seed value of the current round is acquired. Specifically, in any round of the second seed value calculation step of the ethash algorithm, the second seed value of the current round is obtained.
[0057] Step 120 , calculating and obtaining a plurality of first index values in the DAG and primary random numbers correspon...
Embodiment 2
[0092] For ease of understanding, in this embodiment, the traditional proof-of-work algorithm is first described, such as Figure 4A As shown, in the traditional proof-of-work algorithm, the following steps are included:
[0093] 1. Calculate the seed
[0094] Header_hash is the seed used to generate verification cache and mining data set, with a length of 32 bytes.
[0095] Fill the nonce value into the last (40-32=8) bytes of the seed, (the nonce itself is 64 bits, corresponding to 8 bytes), and just fill the 40-byte seed completely with the hash and nonce.
[0096] The seed is encrypted with sha3-512 (Keccak512).
[0097] 2.Mix (mixing)
[0098] Convert the 64Bytes seed to 16 4Bytes types, copy 2 copies as Seed_mix
[0099] Calculate a DAG index according to the formula, obtain data from the DAG according to the index, and fnv hash the obtained data and seed as a new seed; this step is repeated 64 times;
[0100] in
[0101]
[0102] 0x01000193 is a hash prime numb...
Embodiment 3
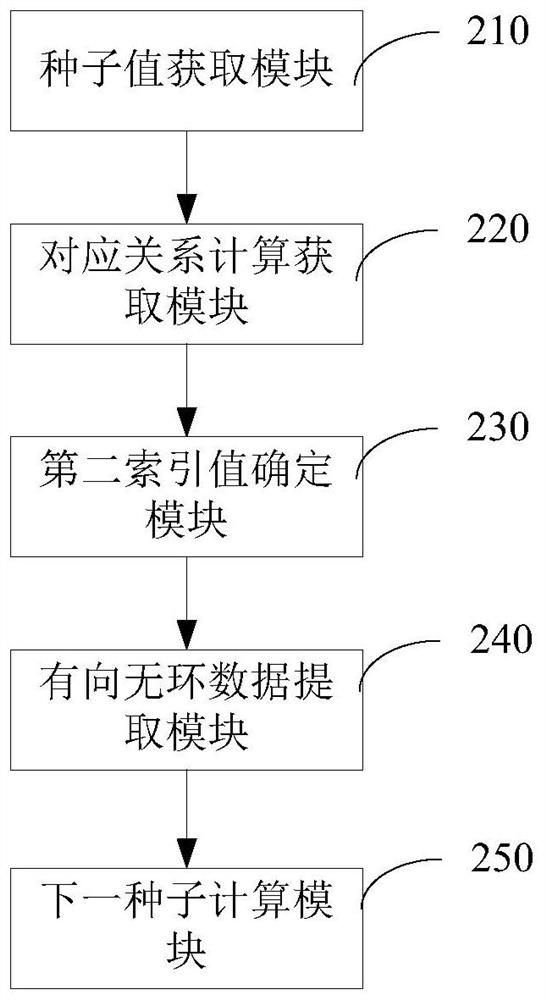
[0150] In this example, if figure 2 As shown, a proof-of-work algorithm optimization device is provided, including:
[0151] The secondary seed value acquisition module 210 is used to obtain the secondary seed value of the current round;
[0152] The correspondence calculation and acquisition module 220 is configured to calculate and obtain a plurality of first index values in the directed acyclic graph and a primary random number corresponding to each of the first index values according to the secondary seed value of the current round;
[0153] The second index value determining module 230 is configured to detect the number of primary random numbers corresponding to each of the first index values, obtain the first index value corresponding to the largest number of primary random numbers, and determine it as the second index value;
[0154] A directed acyclic data extraction module 240, configured to extract directed acyclic data corresponding to the second index value f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com