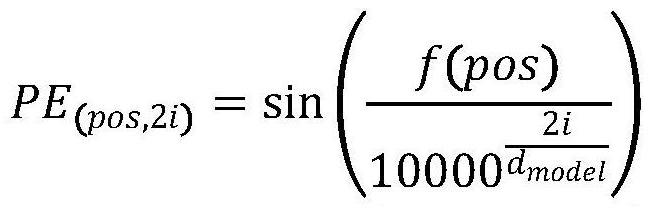A Method of Preventing Text Stream Sequence Transformation Attack
A text flow and sequence technology, applied in the field of artificial intelligence, can solve problems such as sequential attacks, destroying sequence information, and reducing model effectiveness, achieving the best performance, strong scalability, and good portability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
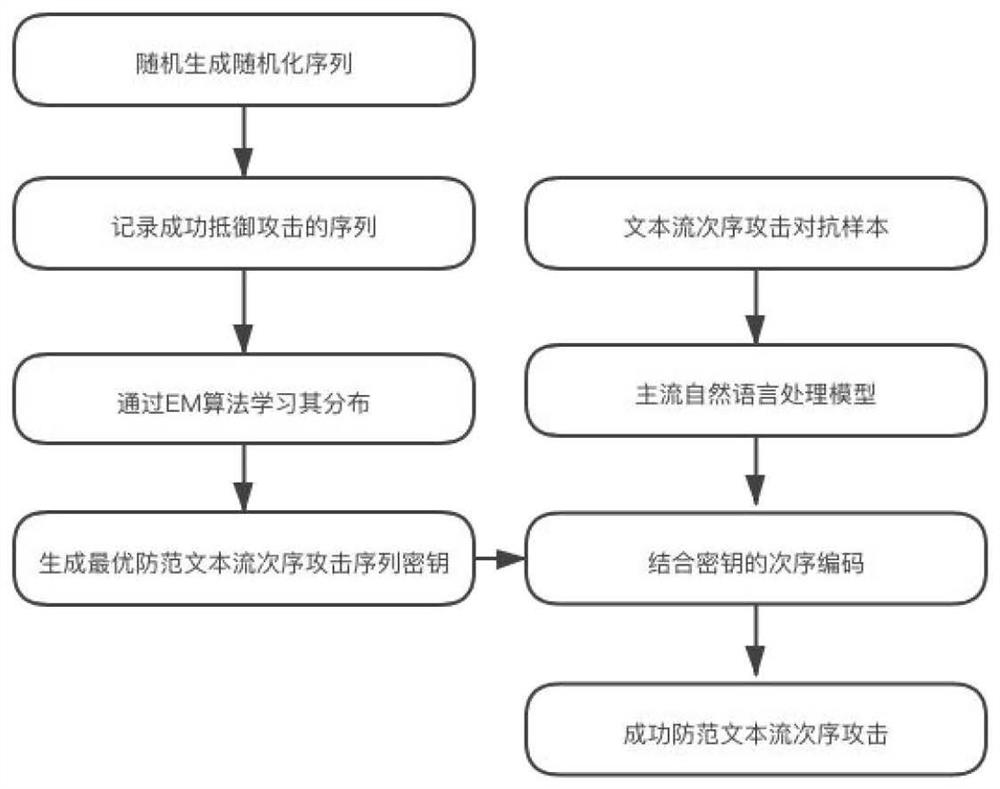
[0026] The method includes the following parts and processes:
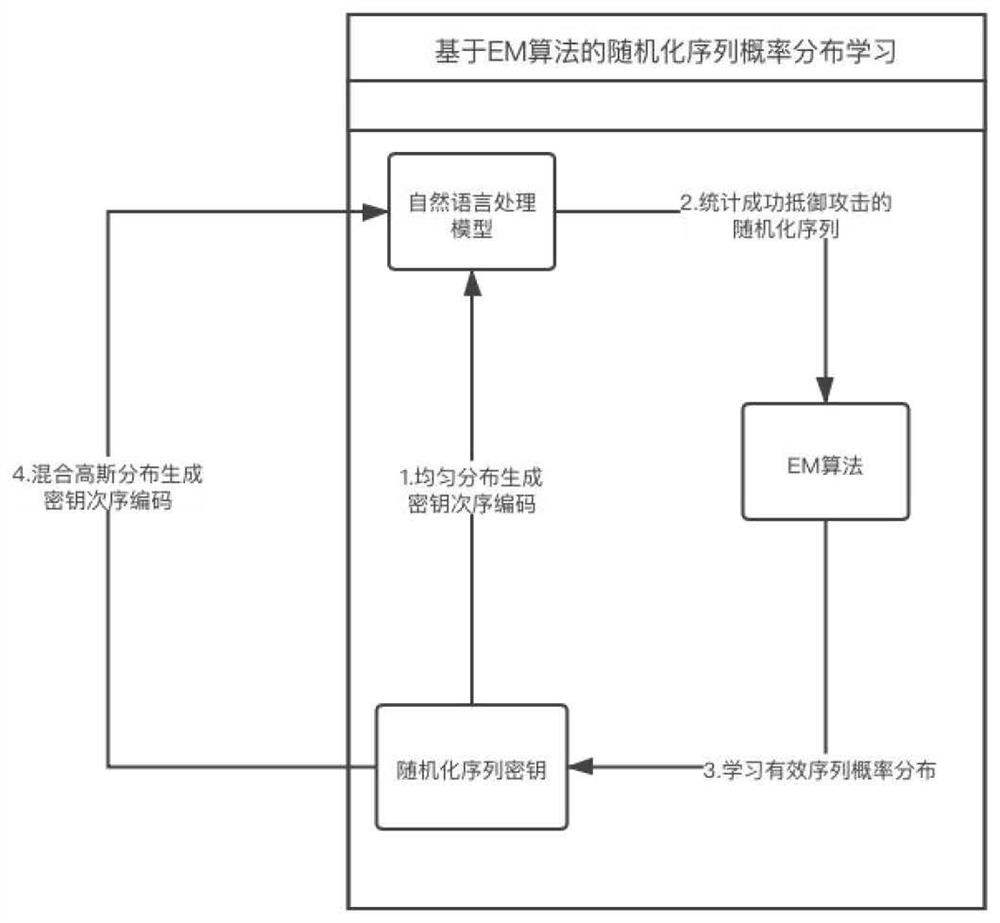
[0029] Generate a randomization sequence key: generate a randomization sequence key through the mixture Gaussian distribution learned by EM, and
[0034] The data we use mainly include two kinds, one is the ordinary text translation training data, and the other is the natural language
[0038] In order to make the randomization sequence have the best effect against attacks, we use the EM algorithm to randomize the sequence probability.
[0041]
[0042]
[0043] That is, the part of f(pos) in formulas 5.1 and 5.2 is not the normal order, but the position represented by the key. Likewise, in
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com