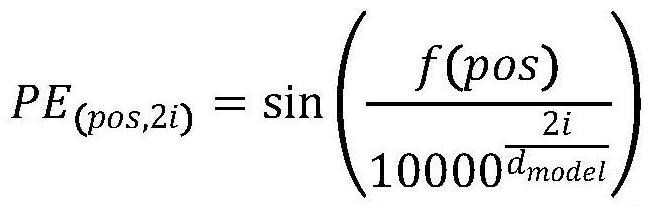Method for preventing text stream order transformation attack
A text flow and sequence technology, applied in text database query, unstructured text data retrieval, digital data protection, etc., can solve problems such as destroying sequence information, sequence attacks, and reducing model effectiveness, achieving strong scalability and performance Best, Portable Results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The following is a preferred embodiment of the present invention and the technical solutions of the present invention are further described in conjunction with the accompanying drawings, but the present invention is not limited to this embodiment.
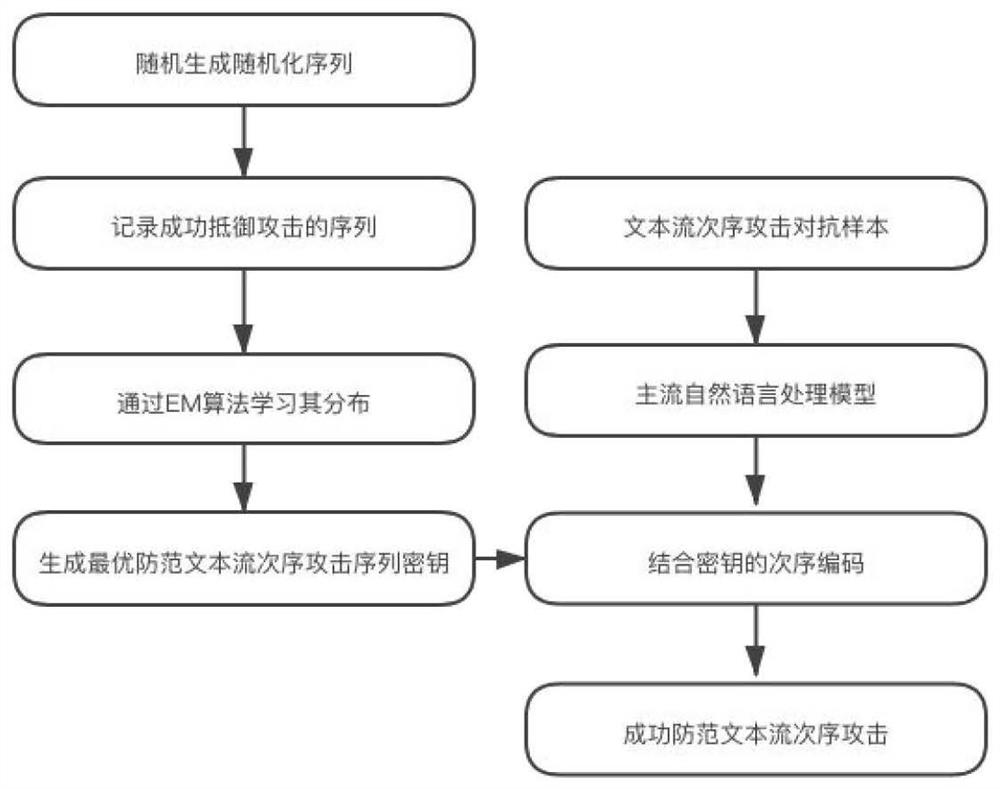
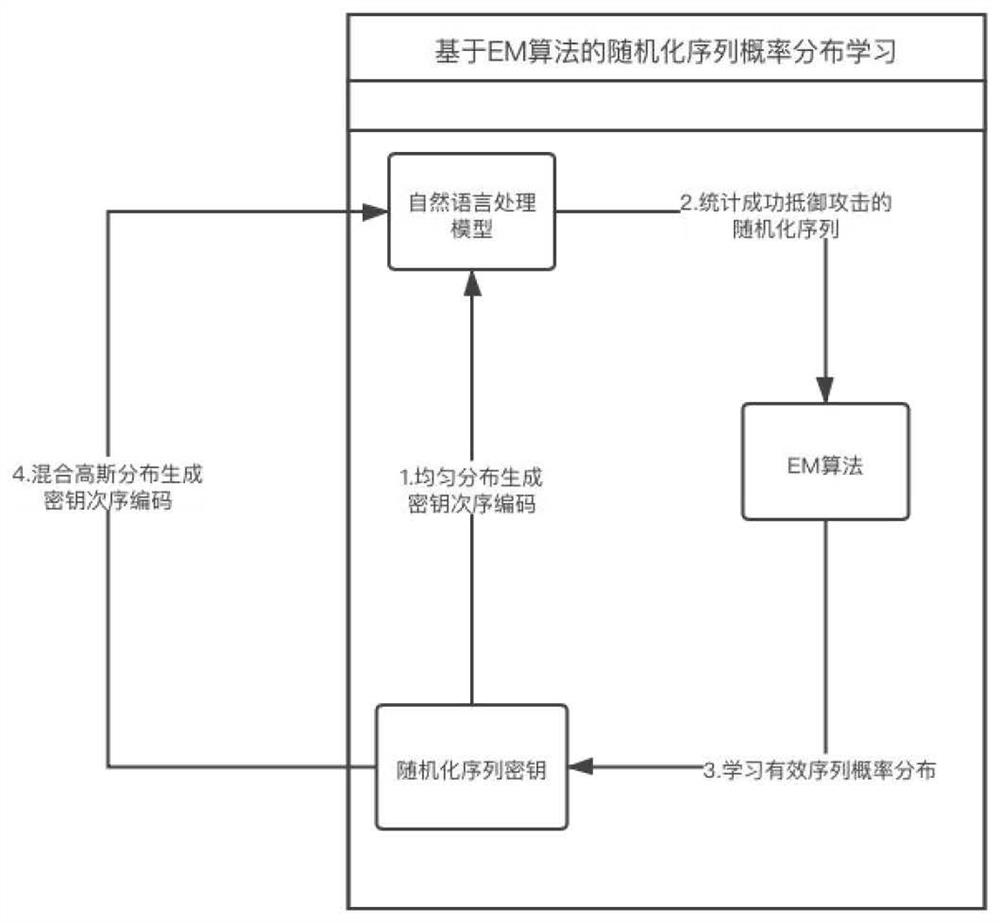
[0025] The present invention proposes a method for preventing text flow sequence transformation attacks, and learns the optimal sequence probability distribution for resisting attacks through EM algorithm, and finally prevents the attack sequence encoding of the adversarial samples against flow sequence attacks, so as to prevent text flow sequence attacks effect, to achieve design goals and application goals.
[0026] The method includes the following parts and processes:
[0027] Natural language processing model based on randomized sequence encoding: Based on the original transformer model, use the randomized sequence as the key to generate sequence encoding, and use the generated sequence encoding as the encoding for reco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com