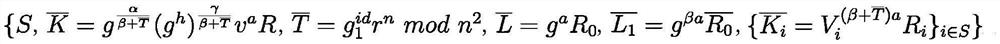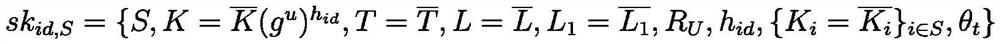Efficient responsibility-traceable and revocable attribute-based encryption method
An attribute-based encryption and efficient technology, applied in the field of information security and privacy protection, can solve problems such as no storage overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] Specific embodiments of the present invention are described below, so that those skilled in the art understand the present invention, but, the present invention is not limited to the scope of specific embodiments, for those of ordinary skill in the art, as long as various changes Within the scope of the present invention defined and determined by the claims, all inventions and creations utilizing the concept of the present invention are included in the protection.
[0044] Our scheme consists of eight phases: system initialization phase, key generation phase, encryption phase, decryption phase, key integrity verification, traitor tracing phase, user revocation phase, and public audit phase.
[0045] 1) System initialization (System Initialization contains two algorithms)
[0046] There is one entity participating in this stage, the system authority AT, the system authority executes the system establishment algorithm, and is responsible for generating the public paramete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com