Ciphertext analysis method and system for data transaction
An analysis method and transaction key technology, applied in data processing applications, payment systems, payment system structures, etc., can solve problems such as variable information exposure, and achieve the effect of reducing the risk of exposure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
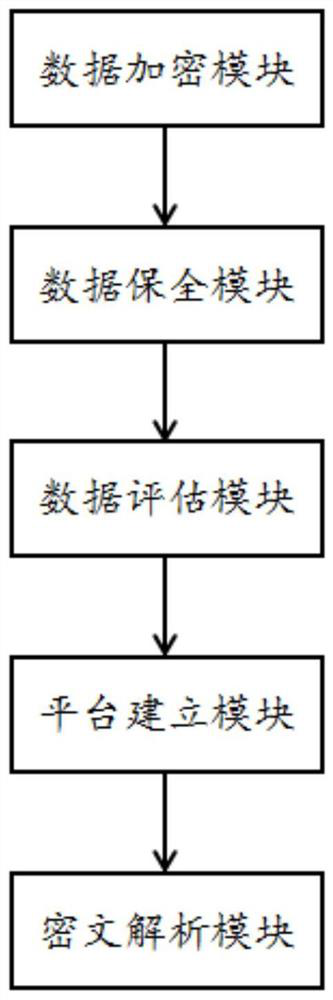
[0036] The embodiment is basically as attached figure 1 shown, including:
[0037] The data encryption module is used to register and encrypt data assets at the same time, and the registered data asset information forms a registration block chain;
[0038] The data preservation module is used for data preservation of data assets, and the preserved data asset information forms a preservation block chain;
[0039] The data evaluation module is used to use the AHP analysis method to evaluate the price of data assets, and the evaluated data asset information forms an evaluation block chain;
[0040] The platform building module is used to connect the registration block chain, security block chain and evaluation block chain through the block chain and CA algorithm to form a block chain rope network, and establish a data transaction platform based on the block chain rope network;
[0041] The ciphertext analysis module is used to obtain blocks containing variable information from ...
Embodiment 2
[0053] The only difference from Embodiment 1 is that the ciphertext analysis module generates a random number as the transaction key of the plaintext message, and performs symmetric encryption on the plaintext message according to the transaction key to obtain the ciphertext message corresponding to the variable information. The random number is randomly generated as the transaction key of the plaintext message to avoid the regularity of the transaction key of the plaintext message; the symmetrical encryption of the randomly generated transaction key can improve the encryption effect.
Embodiment 3
[0055] The only difference from Embodiment 2 is that, at each transaction, the variable information in the transaction process is related to the transaction rules, that is to say, the variable information is rule-sensitive. Therefore, the same transaction information, which was not judged as variable information in the last transaction, may be judged as variable information in this transaction due to the change of rules; similarly, the same transaction information is judged as variable information in this transaction It is not judged as variable information, but it may be judged as variable information in the next transaction due to the change of rules. In this embodiment, after the plaintext message of the variable information is obtained, the variable information is divided into variable information sensitive to rule quality and variable information sensitive to rule quantity.
[0056] In this embodiment, the changeable information includes three types, which are Type A tran...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com