Method and device for jointly generating data tuples for secure computing
A data tuple and security technology, applied in the field of data privacy security, can solve the problem of difficult implementation of machine learning model training, and achieve the effect of efficient multi-party secure computing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
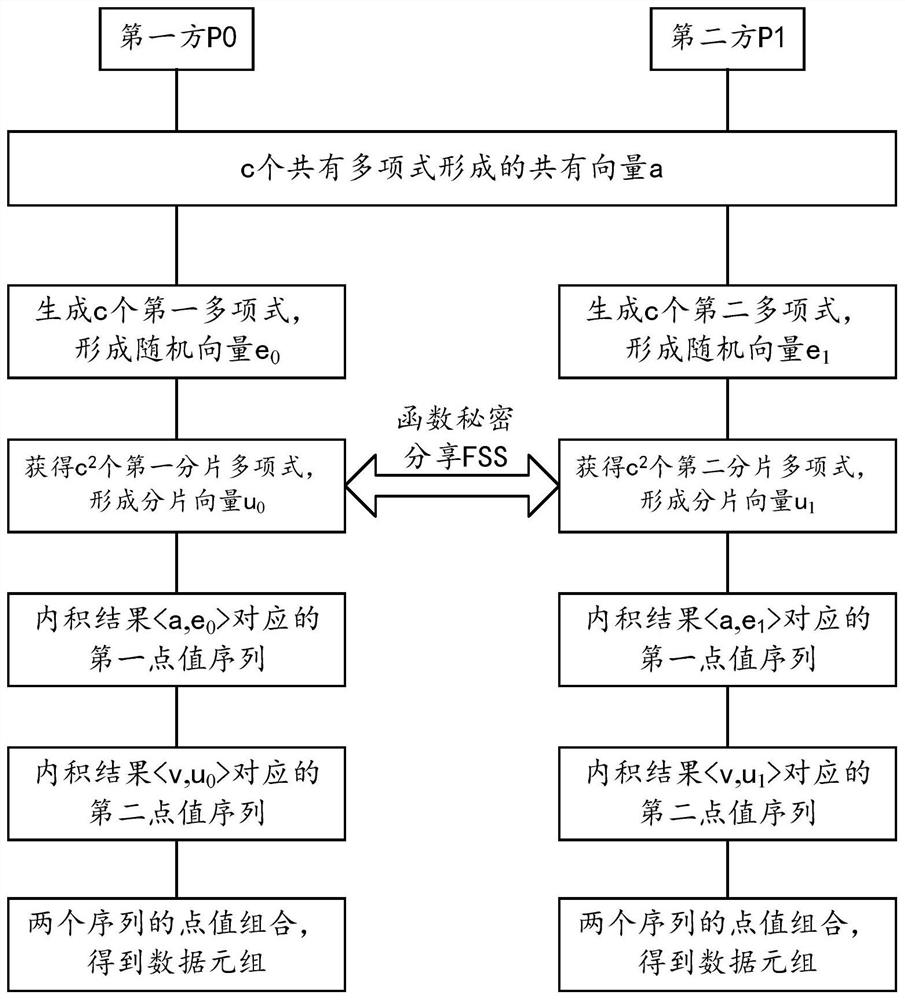
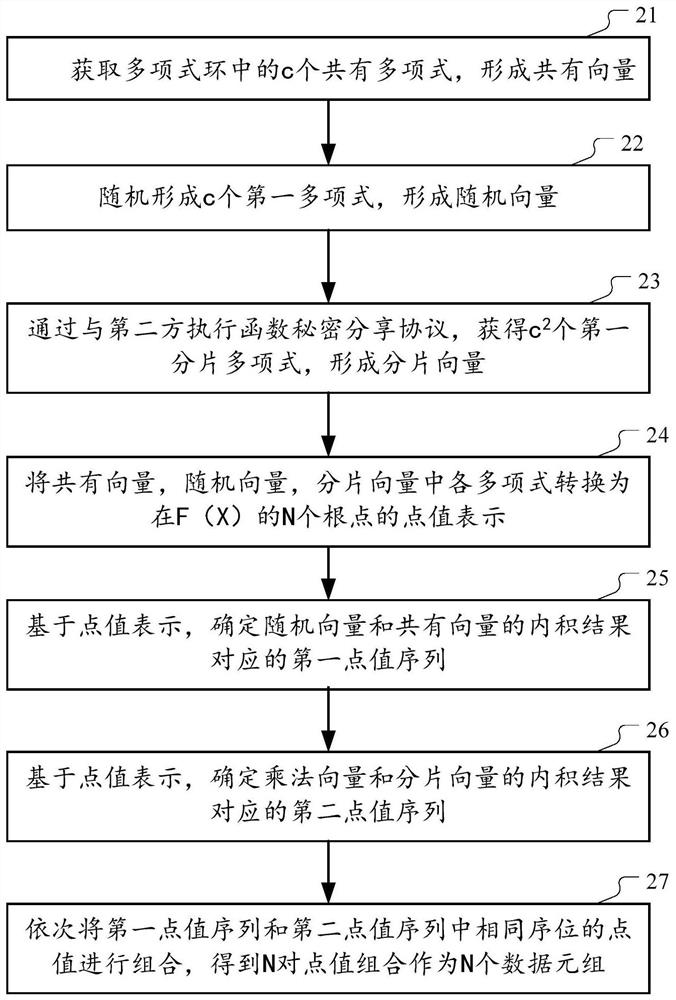
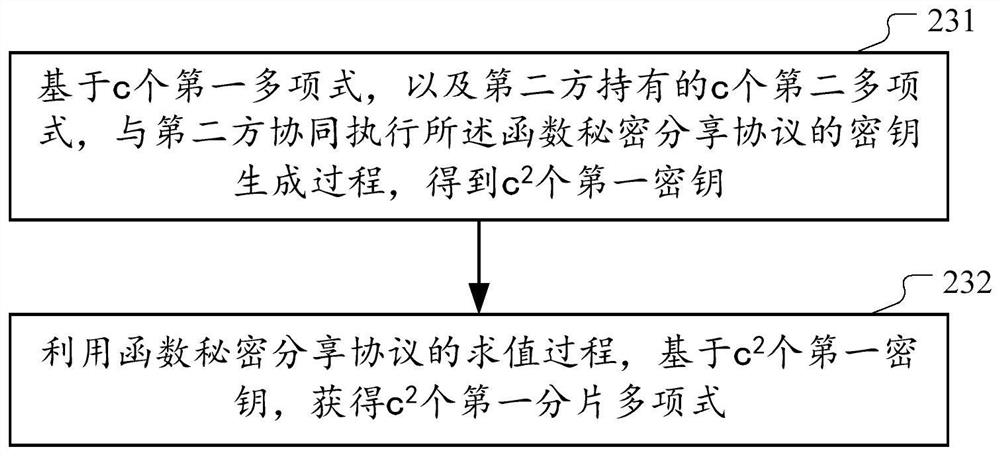
[0144] According to an implementation manner, the secret sharing unit 53 includes:
[0145] The key acquisition module 531 is configured to, based on the c first polynomials and the c second polynomials held by the second party, cooperate with the second party to execute the key generation of the functional secret sharing protocol process, get c 2 a first key;
[0146] The key expansion module 532 is configured to use the evaluation process of the function secret sharing protocol, based on the c 2 first key, get c 2 a first slice polynomial.
[0147] In one embodiment, the c first polynomials include polynomial i, and the c second polynomials include polynomial j; both polynomial i and polynomial j include t items; the function secret sharing protocol based on t 2 A distributed point function is constructed. In such cases, the key acquisition module 531 is configured as:
[0148] Based on the first coefficient of each item in polynomial i and the second co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com