Method for generating and using encrypted tamper-proof file
A tamper-proof, symmetric encryption algorithm technology, applied in the field of embedded industrial control and information security, can solve the problems of large resource consumption of file tampering monitoring, complicated authorization process, inaccurate positioning of tampered content, etc., to facilitate attack analysis and copy. Transfer and resolve the effect of self-recovery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The specific embodiment of the present invention will be further described below in conjunction with accompanying drawing:
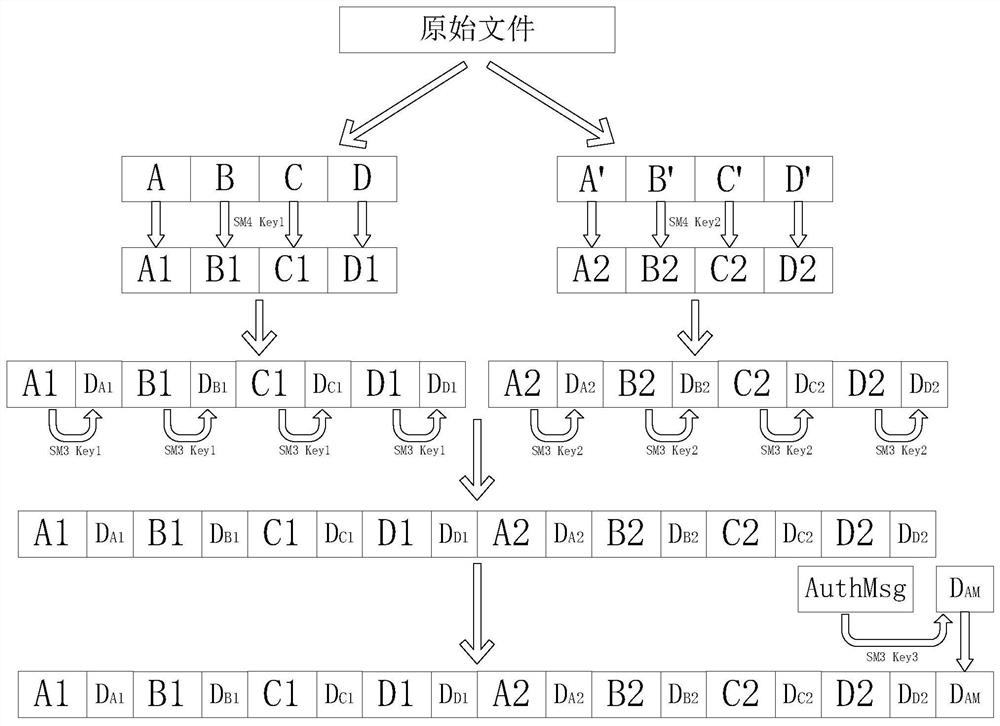
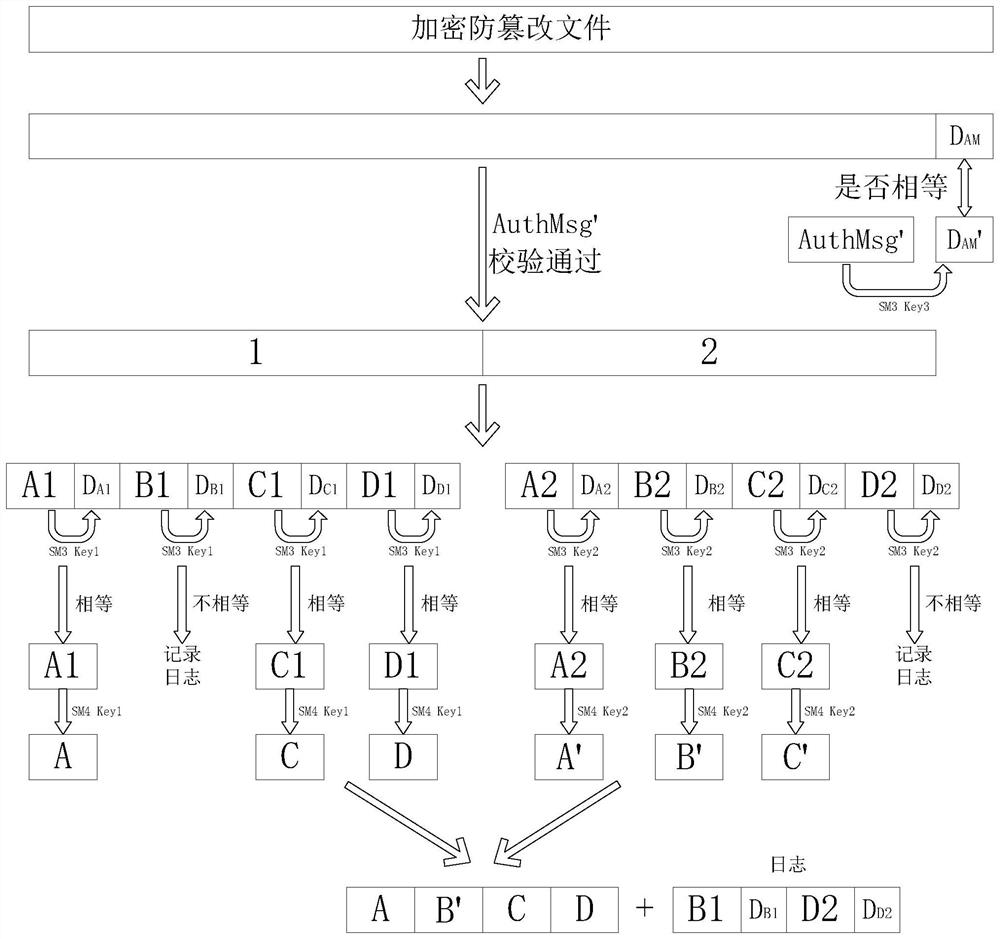
[0029] Such as figure 1 As shown, it is a schematic diagram of the generation process of the encrypted tamper-proof file of the present invention, and the specific steps of generating the file are as follows:
[0030]S1: The power secondary equipment application writes files with the authorization information code AuthMsg. The authorization information code is 200 bytes of plaintext data, and the format and content are determined by the application itself;
[0031] S2: After the file system generates the original file, obtain the file size SizeFile (assuming the file size is 4K), open up (SizeFile*2)+(SizeFile / 1K)*32*2+32 byte space to record the final generated encryption Tamper-proof documents;
[0032] S3: Group the original file in units of 1K bytes to obtain four groups A, B, C, and D, and make a copy of the four groups A', B', C', and D'; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com