Network intrusion detection method and system based on data enhancement and BiLSTM
A network intrusion detection and data technology, applied in the field of network security, can solve the problems of low recognition accuracy and low false positive rate, and achieve the effect of high overall detection rate, low false positive rate, and easy handling.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0049] The positional relationship described in the drawings is only for illustrative purposes and cannot be construed as a limitation to this patent;
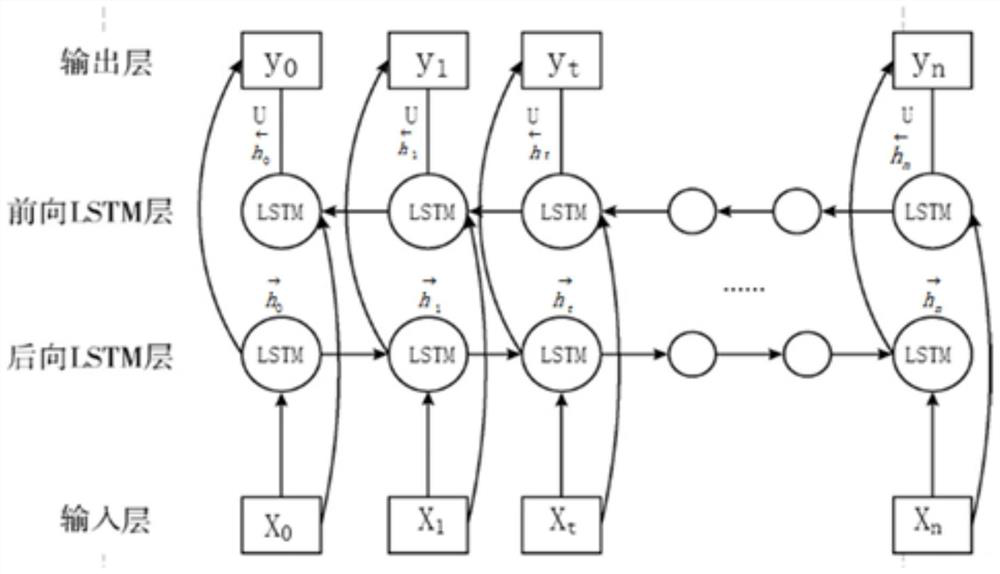
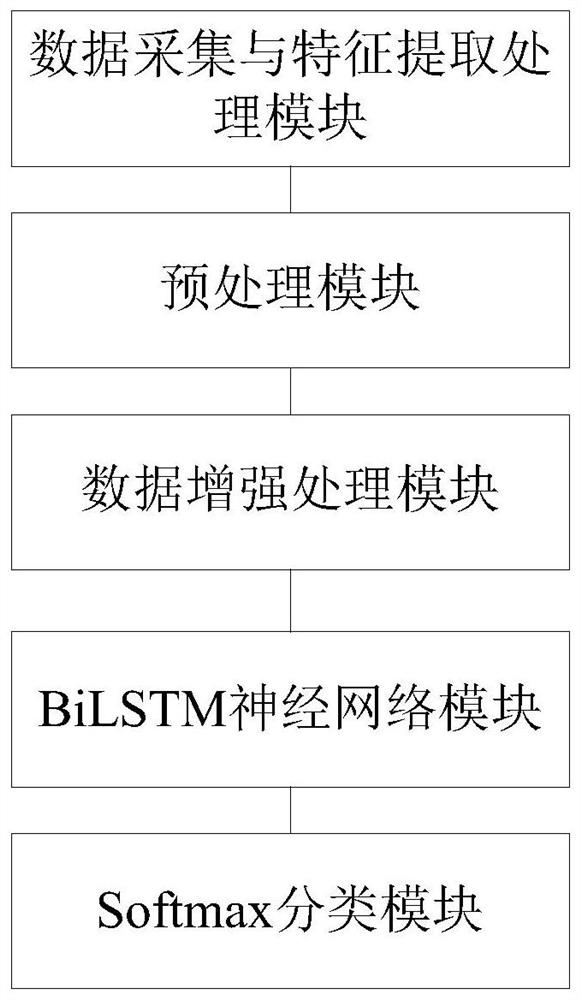
[0050] like figure 1 The flow diagram of the network intrusion detection method based on data enhancement and BiLSTM shown in figure 1 ,include:
[0051] S1. Collect network intrusion detection traffic data, and extract features of network intrusion detection traffic data; in this embodiment, methods for extracting features of network intrusion detection traffic data include: filtering method, wrapping method and embedded method, the class labels of the features of the extracted network intrusion detection traffic data are character features.
[0052] S2. Using the extracted features to construct a training data set, and preprocessing the training data set;
[0053] Since the original data in the training data set is the collected network traffic features, the class labels are character features, in order to facilitate subs...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com