Embedded operating system running environment monitoring method based on security chip
An operating system and security chip technology, applied in hardware monitoring, computer security devices, instruments, etc., can solve the problems of no integrated security chip, not providing much support and use, etc., to ensure credibility, avoid adversary tampering, efficiency boosted effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The specific implementation mode of the present invention is illustrated below in conjunction with accompanying drawing:
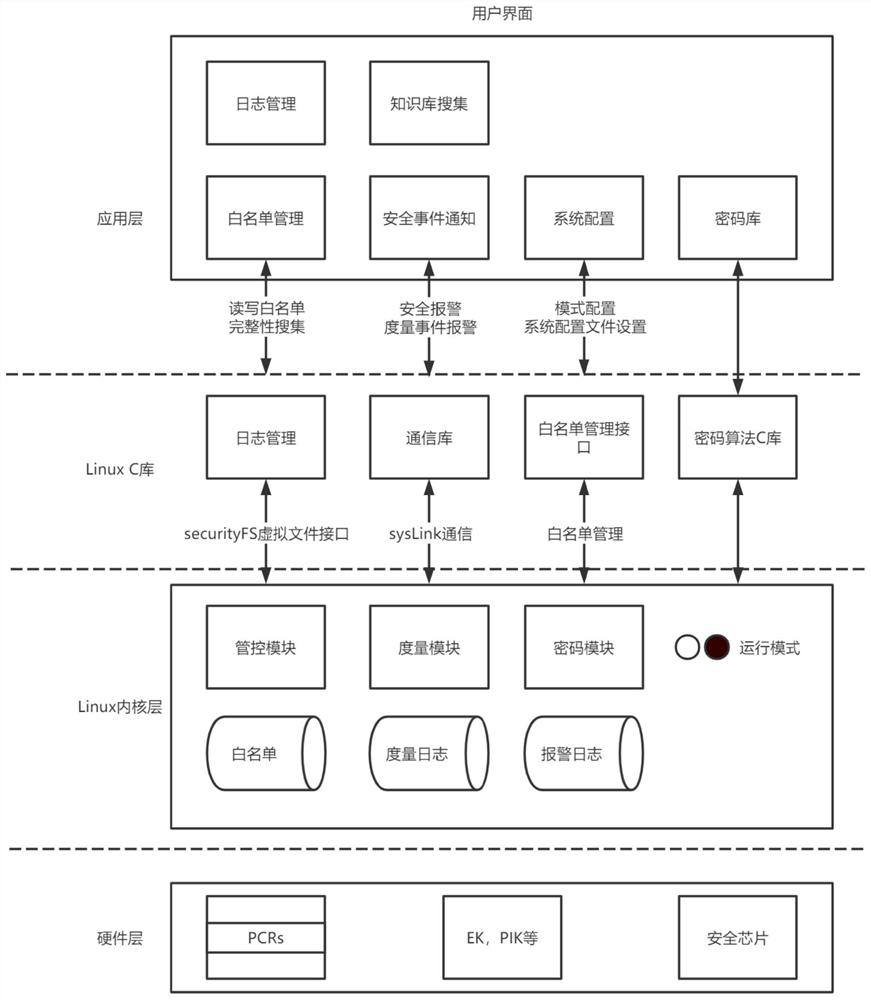
[0041]A method for monitoring the operating environment of an embedded system based on a security chip. Those skilled in the art can refer to the method to design and implement a corresponding system security protection system. It mainly includes the following steps: (1) the measurement framework collects the integrity data of the system environment; (2) the administrator manages the integrity through the interface; (3) formulates and deploys corresponding whitelist security policies according to their specific needs; (4) ) after deployment, the platform enters the control state, and applications not on the whitelist are prohibited from executing. details as follows:
[0042] 1. Terminal equipment manufacturers, embedded operating system manufacturers: According to the requirements of secure boot, realize the two-level digital signature verificatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com