Hardware authorization method and system
A technology of hardware and hardware attributes, applied in the field of electronic information, can solve the problems of cracking, the chip does not contain, it is difficult to obtain time and batches, etc., to prevent piracy and prevent missed detection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The specific embodiments of the present invention will be further described below in conjunction with the accompanying drawings. It should be noted here that the descriptions of these embodiments are used to help understand the present invention, but are not intended to limit the present invention. In addition, the technical features involved in the various embodiments of the present invention described below may be combined with each other as long as they do not constitute a conflict with each other.
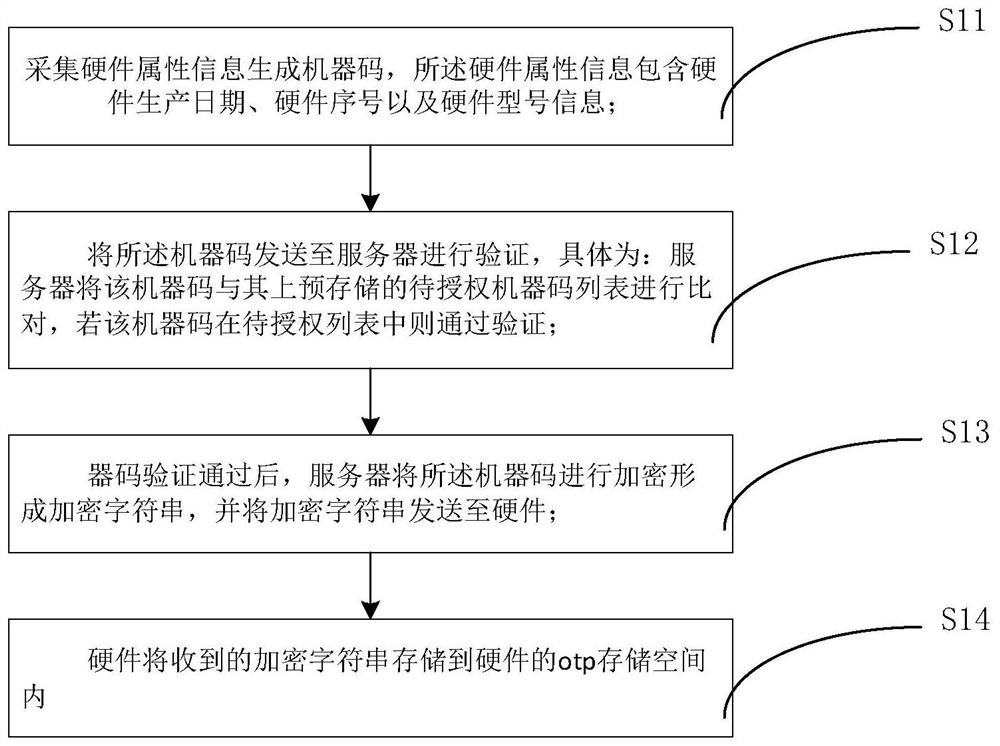
[0042] A hardware authorization method, including production test steps and hardware use steps:
[0043] The production test steps include:
[0044] S11: Collect hardware attribute information to generate a machine code, the hardware attribute information includes hardware production date, hardware serial number, and hardware model information;
[0045] In the above step S11, collecting hardware attribute information to generate machine codes includes:
[0046] The se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com