Image tampering blind forensics method based on detection-segmentation architecture
A blind forensics, image technology, applied in image enhancement, neural architecture, image analysis and other directions, can solve the problems of solidification of detection methods, inaccurate positioning of tampered areas, etc., and achieve the effect of improving detection recall rate and
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] Next, the technical solutions in the embodiments of the present invention will be described in connection with the drawings in the embodiments of the present invention, and the described embodiments are merely embodiments of the present invention, not all of the embodiments. The embodiments described with reference to the accompanying drawings are exemplary, and is intended to be construed as limiting the invention.
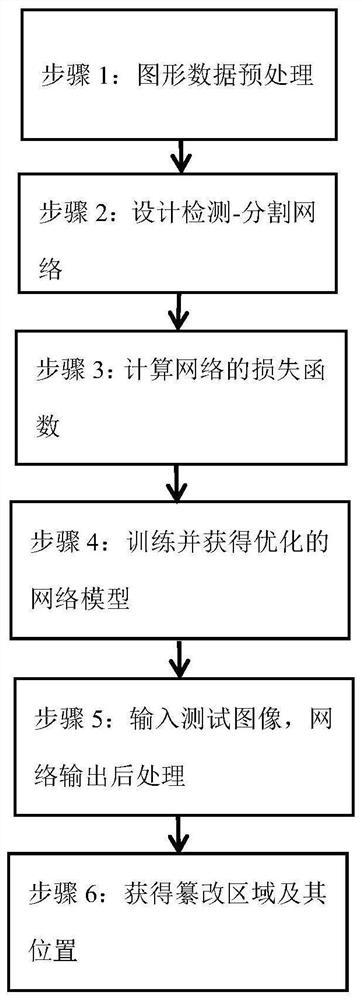
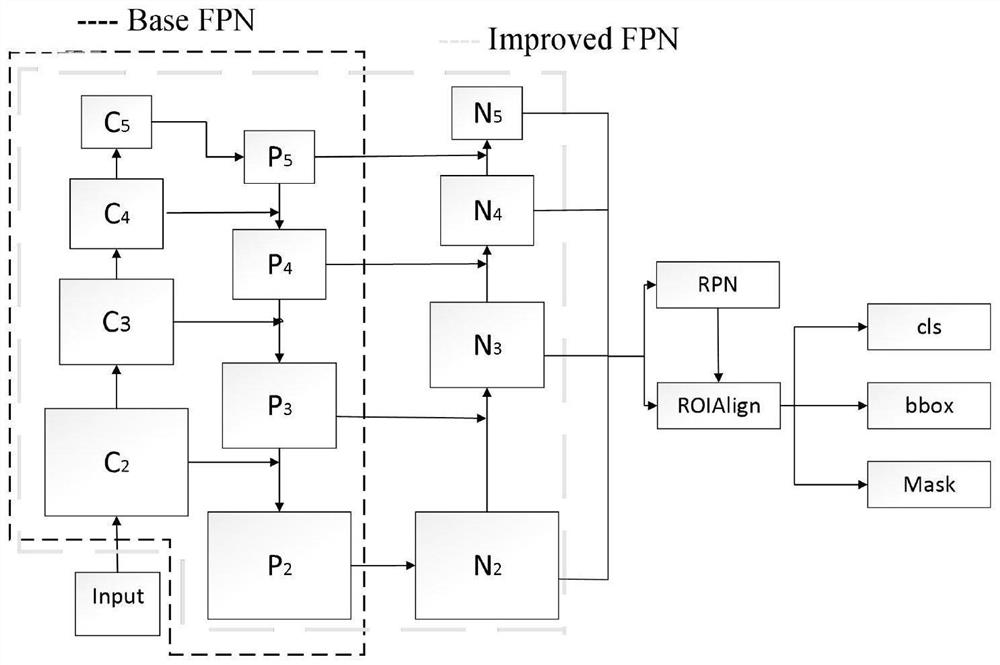
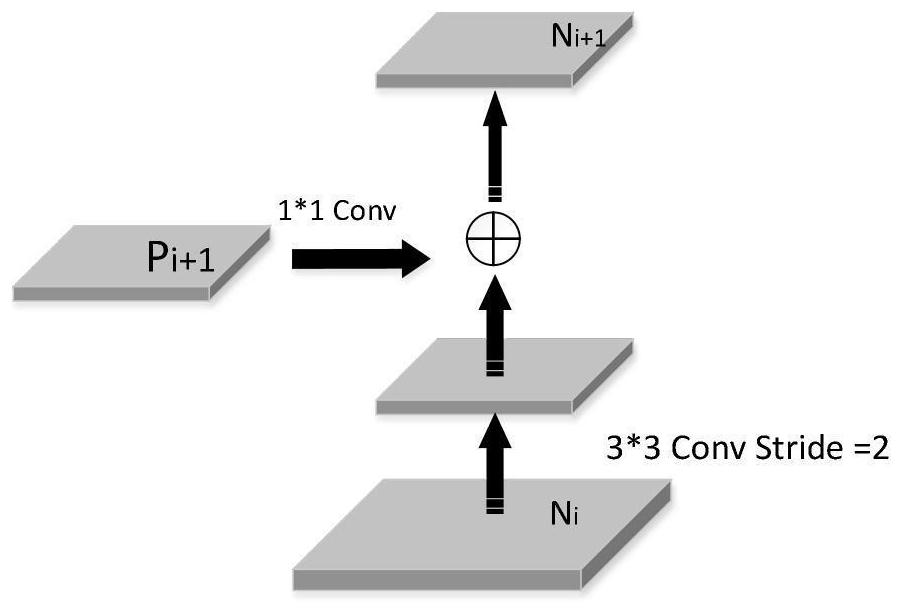
[0032] like figure 1 As shown, it is the basic flow of the algorithm of the present invention, and the specific steps are as follows:
[0033] like figure 1 As shown, an image-based image tampering method method based on the detection-segmentation architecture, the specific steps are as follows:
[0034] Step 1: Graphical data pretreatment, the data image of the present embodiment uses CASIA2 and Columbia public split data sets of 5303 images, and the label software Labelme marks its tampering area MASK. The original image and Mask image size are fixed to 1024...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com