A distributed backup synchronization system for public cloud tenant business sensitive data
A sensitive data, distributed technology, applied in database distribution/replication, redundancy in computing, data error detection, network data retrieval, etc., can solve problems such as poor data security, inability to hide, inability to backup, etc. Achieve the effect of ensuring safety and reducing protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
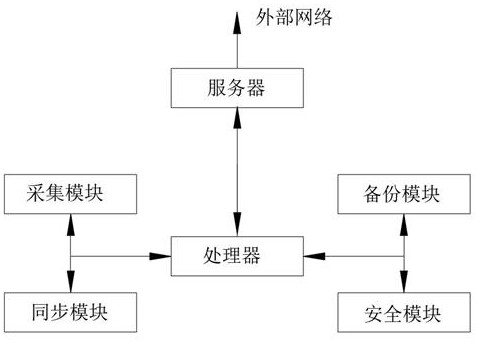
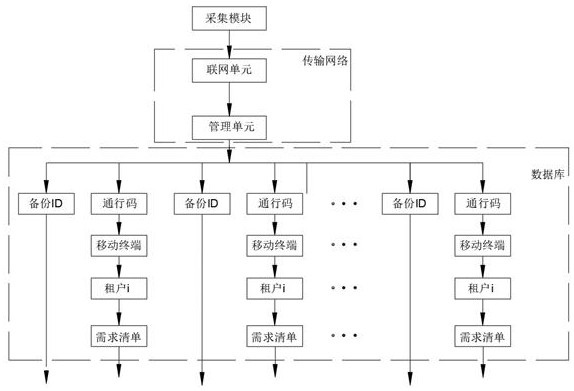
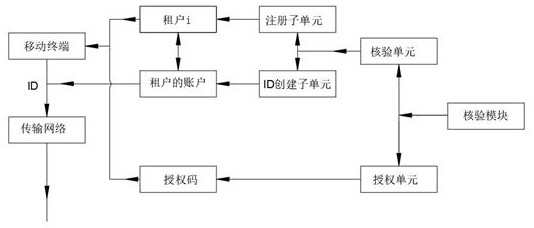
[0052] Embodiment one: according to Figure 1-Figure 5 , providing a distributed backup synchronization system for public cloud tenant business sensitive data, including a collection module, a security module, a backup module, a synchronization module, a verification module and a processor, the processor is respectively connected with the collection module, the The security module, the backup module, the synchronization module and the verification module control the connection, and carry out accurate backup or protection of the data of each tenant under the centralized control of the processor. In addition, the synchronization system further includes a server, the server is connected to the processor, and is connected to an external system or network through the server, so as to realize data protection for each tenant. Wherein, the collection module is used to collect the tenant's data, so as to realize the collection of the tenant's business and identity ID; the verification ...
Embodiment 2
[0083] Embodiment 2: This embodiment should be understood as at least including all the features of any one of the foregoing embodiments, and further improved on the basis of it, according to Figure 1-Figure 5 , is also to determine the real-time estimated distance of the demand submission equipment, wherein the estimated distance between the tenant’s provision location and the demand provision location is based on the demand provided by the tenant and through the search engine to satisfy the requirements in the list The location is determined, and the real-time estimated distance of the request submission device is determined, and the estimated distance is determined according to the following formula:
[0084]
[0085] Among them, in distance (u i , u j ), u i Indicates the location coordinates of the mobile terminal or the tenant, and its coordinates are represented by (x i ,y i ) means; u j Indicates the location coordinates that satisfy the requirements list, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com