Video real-time transmission safety monitoring method, system, device and readable storage medium
A technology of real-time transmission and security monitoring, applied in the direction of transmission system, digital transmission system, closed-circuit television system, etc., can solve the problems of inability to obtain the real situation of the monitoring location, poor detection effect of fake video, and affecting network monitoring security, etc., to prevent Effects of video forgery attack, avoiding video picture quality, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
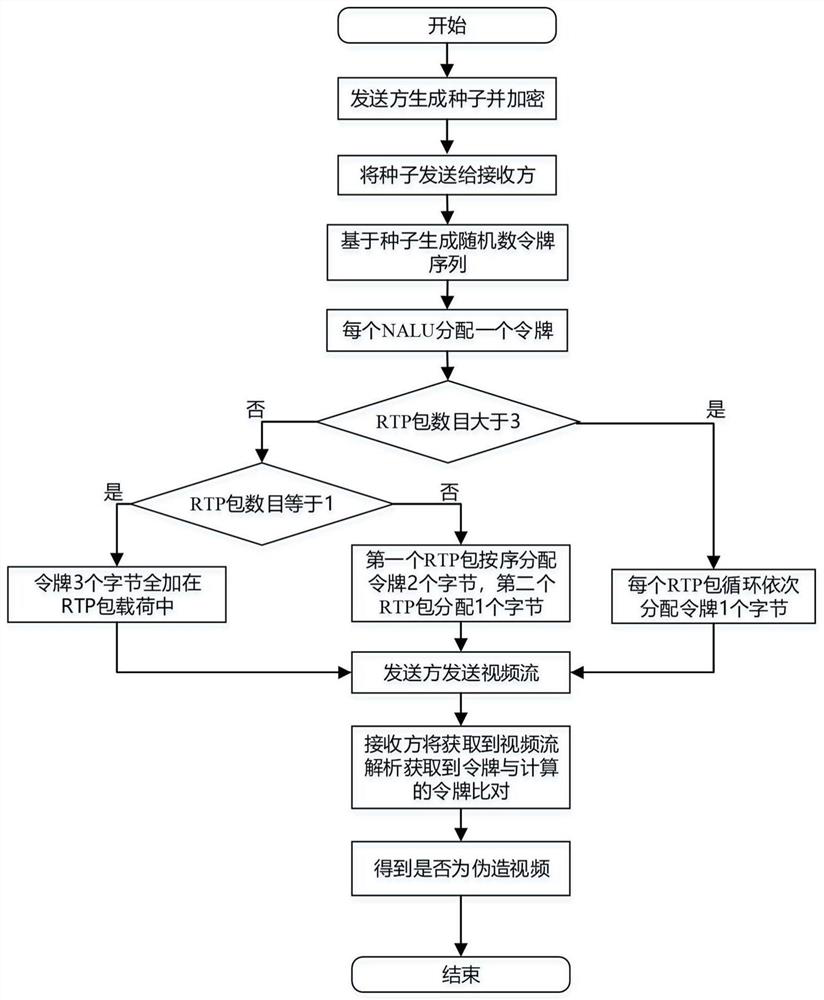
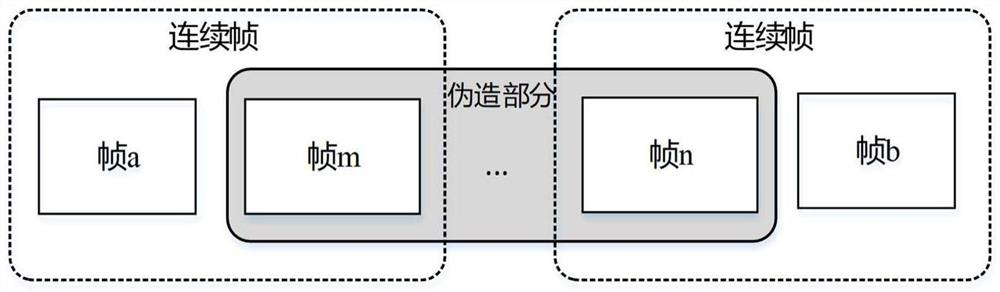
[0041] Embodiment: a section of video stream is provided with 5 NALU units, and several RTP packets are included in each NALU unit, and the specific data format is: {{P (0,0)}, {P (1,0) , P (1,1) , P (1,2) ,P (1,3) ,P (1,4)},{P (2,0) ,P (2,1) ,P (2,2) ,P (2,3)},{P (3,0) ,P (3,1) ,P (3,2) ,P (3,3) ,P (3,4)},{P (4,0) ,P (4,1) ,P (4,2) ,P (4,3) ,P (4,4)}} The sender sends the above data in order, and after the link transmission, the packets received by the receiver are P (0,0) ,P (1,0) ,P (1,2) ,P (1,3) ,P (1,4) ,P (x,0) ,P (x,1) ,...
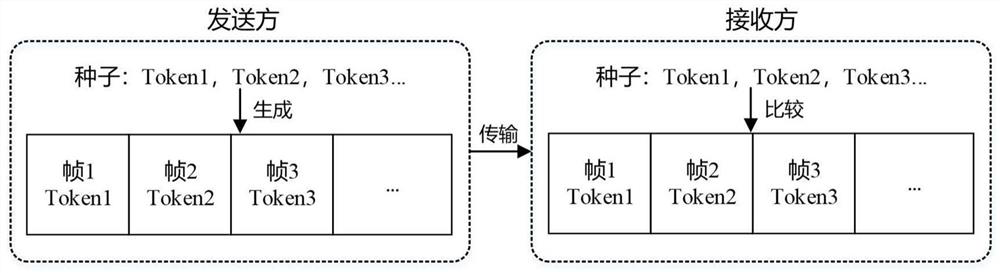
[0042] (1) The sender first randomly generates 3 random number seeds, which are 88, 66, and 44 respectively, and encrypts them using the ECC algorithm. In order to ensure the reliability of the transmission, the ciphertext is sent to the receiver using the TCP protocol ; At the same time, based on the 3 random number seeds, the pseudo-random number generation algorithm in the Crypto++ library is used to generate 3 random n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com